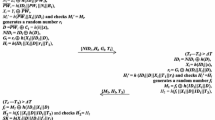
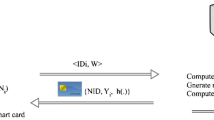
Abstract
In recent past, Mir and Nikooghadam presented an enhanced biometrics based authentication scheme using lightweight symmetric key primitives for telemedicine networks. This scheme was introduced in an anticipation to the former biometrics based authentication system proposed by Yan et al. Mir and Nikooghadam declared that their scheme is invincible against potential attacks while providing user anonymity. Our study and in-depth analysis unveil that Mir and Nikooghadam’s authentication scheme is susceptible to smart card stolen attack, moreover anonymity violation is still possible despite the claim of Mir and Nikooghadam. We have utilized the random oracle model in order to perform security analysis. The analysis endorses that the proposed scheme is robust enough to provide protection against all potential attacks specially smart card stolen attack and user anonymity violation attack. Analysis is further substantiated through an automated software application ProVerif. The analysis also shows that proposed scheme is computationally efficient than Mir and Nikooghadam’s scheme.



Similar content being viewed by others
References
Anderson GF, Reinhardt UE, Hussey PS, Petrosyan V (2003) It’s the prices, stupid: why the United States is so different from other countries. Health Aff 22 (3):89–105
Arshad H, Nikooghadam M (2014) Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J Med Syst 38(12):1–12
Arshad H, Nikooghadam M (2015) Security analysis and improvement of two authentication and key agreement schemes for session initiation protocol. J Supercomput 71(8):3163–3180. doi:10.1007/s11227-015-1434-8
Arshad H, Nikooghadam M (2016) An efficient and secure authentication and key agreement scheme for session initiation protocol using ecc. Multimedia Tools and Applications 75(1):181–197. doi:10.1007/s11042-014-2282-x
Awasthi AK, Srivastava K (2013) A biometric authentication scheme for telecare medicine information systems with nonce. J Med Syst 37(5):1–4
Chang YF, Tai WL, Chang HC (2014) Untraceable dynamic-identity-based remote user authentication scheme with verifiable password update. Int J Commun Syst 27(11):3430–3440
Chaudhry S, Naqvi H, Shon T, Sher M, Farash M (2015) Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J Med Syst 39(6):66. doi:10.1007/s10916-015-0244-0
Chaudhry SA, Farash MS, Naqvi H, Kumari S, Khan MK (2015) An enhanced privacy preserving remote user authentication scheme with provable security. Security and Communication Networks:1–13. doi:10.1002/sec.1299
Chuang MC, Chen MC (2014) An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst Appl 41(4):1411–1418
Das AK (2015) A secure and effective biometric-based user authentication scheme for wireless sensor networks using smart card and fuzzy extractor. Int J Commun Syst. doi:10.1002/dac.2933
He D, Kumar N, Lee JH, Sherratt R (2014) Enhanced three-factor security protocol for consumer usb mass storage devices. IEEE Trans Consum Electron 60(1):30–37. doi:10.1109/TCE.2014.6780922
He D, Zeadally S (2015) Authentication protocol for an ambient assisted living system. IEEE Commun Mag 53(1):71–77. doi:10.1109/MCOM.2015.7010518
Irshad A, Sher M, Faisal MS, Ghani A, Ul Hassan M, Ashraf Ch S (2014) A secure authentication scheme for session initiation protocol by using ecc on the basis of the Tang and Liu scheme. Security and Communication Networks 7(8):1210–1218
Irshad A, Sher M, Rehman E, Ch SA, Hassan MU, Ghani A (2013) A single round-trip sip authentication scheme for voice over internet protocol using smart card. Multimedia Tools and Applications:1–18
Jin Z, Chen Y (2015) Telemedicine in the cloud era: Prospects and challenges. IEEE Pervasive Comput 14(1):54–61. doi:10.1109/MPRV.2015.19
Khan MK, Kumari S (2013) An improved biometrics-based remote user authentication scheme with user anonymity. Biomed Res Int:2013
Kilinc HH, Yanik T (2014) A survey of sip authentication and key agreement schemes. IEEE Commun Surv Tutorials 16(2):1005–1023
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. In: Advances in cryptology, CRYPTO 99. Springer, pp 388–397
Lal Das M, Saxena A, Gulati VP (2007) A dynamic id-based remote user authentication scheme. arXiv:0712.2235
Lee T, Chang J, Chan C, Liu H (2010) Password-based mutual authentication scheme using smart cards. In: The e-learning and information technology symposium 2010 (EITS2010)
Leu JS, Hsieh WB (2014) Efficient and secure dynamic id-based remote user authentication scheme for distributed systems using smart cards. IET Inf Secur 8(2):104–113
Li CT, Hwang MS (2010) An efficient biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 33(1):1–5
Li X, Ma J, Wang W, Xiong Y, Zhang J (2013) A novel smart card and dynamic id based remote user authentication scheme for multi-server environments. Math Comput Model 58(1):85–95
Liu JY, Zhou AM, Gao MX (2008) A new mutual authentication scheme based on nonce and smart cards. Comput Commun 31(10):2205–2209
Lu Y, Li L, Peng H, Yang X, Yang Y (2015) A lightweight id based authentication and key agreement protocol for multi-server architecture. Int J Distrib Sens N 11(3):635890
Lu Y, Li L, Peng H, Yang Y (2015) An enhanced biometric-based authentication scheme for telecare medicine information systems using elliptic curve cryptosystem. J Med Syst 39(3):1–8
Mehmood Z, Nizamuddin N, Ch S, Nasar W, Ghani A (2012) An efficient key agreement with rekeying for secured body sensor networks. In: Second international conference on digital information processing and communications (ICDIPC), 2012. IEEE, pp 164–167
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Mir O, Nikooghadam M (2015) A secure biometrics based authentication with key agreement scheme in telemedicine networks for e-health services. Wirel Pers Commun 83(4):2439–2461
Mishra D, Das AK, Mukhopadhyay S (2014) A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst Appl 41(18):8129–8143
Mishra D, Mukhopadhyay S, Chaturvedi A, Kumari S, Khan MK (2014) Cryptanalysis and improvement of Yan others.’s biometric-based authentication scheme for telecare medicine information systems. J Med Syst 38(6):1–12
Nikooghadam M, Zakerolhosseini A, Moghaddam ME (2010) Efficient utilization of elliptic curve cryptosystem for hierarchical access control. J Syst Softw 83 (10):1917–1929. doi:10.1016/j.jss.2010.05.072. http://www.sciencedirect.com/science/article/pii/S0164121210001354
Srivastava K, Awasthi AK, Kaul SD, Mittal R (2015) A hash based mutual rfid tag authentication protocol in telecare medicine information system. J Med Syst 39(1):1–5
Tan Z (2013) An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204
Wang D, He D, Wang P, Chu C (2014) Anonymous two-factor authentication in distributed systems: certain goals are beyond attainment. IEEE Trans Dependable Secure Comput PP(99):1–1. doi:10.1109/TDSC.2014.2355850
Wang D, Wang P (2014) On the anonymity of two-factor authentication schemes for wireless sensor networks: attacks, principle and solutions. Comput Netw 73:41–57
Wang D, Wang P (2014) On the anonymity of two-factor authentication schemes for wireless sensor networks: attacks, principle and solutions. Comput Netw 73:41–57
Witteman M (2002) Advances in smartcard security. Information Security Bulletin 7(2002):11–22
Xie Q, Dong N, Wong DS, Hu B (2014) Cryptanalysis and security enhancement of a robust two-factor authentication and key agreement protocol. Int J Commun Syst
Xu X, Zhu P, Wen Q, Jin Z, Zhang H, He L (2013) A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. J Med Syst 38(1):9994. doi:10.1007/s10916-013-9994-8
Yan X, Li W, Li P, Wang J, Hao X, Gong P (2013) A secure biometrics-based authentication scheme for telecare medicine information systems. J Med Syst 37(5):9972. doi:10.1007/s10916-013-9972-1
Zhang L, Tang S, Cai Z (2014) Efficient and flexible password authenticated key agreement for voice over internet protocol session initiation protocol using smart card. Int J Commun Syst 27(11):2691–2702
Zhang M, Zhang J, Zhang Y (2015) Remote three-factor authentication scheme based on fuzzy extractors. Security and Communication Networks 8(4):682–693. doi:10.1002/sec.1016
Acknowledgments
Muhammad Khurram Khan extends his sincere appreciations to the Deanship of Scientific Research at King Saud University for its funding the Prolific Research Group (PRG-1436-16) 2.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Chaudhry, S.A., Naqvi, H. & Khan, M.K. An enhanced lightweight anonymous biometric based authentication scheme for TMIS. Multimed Tools Appl 77, 5503–5524 (2018). https://doi.org/10.1007/s11042-017-4464-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4464-9