Abstract
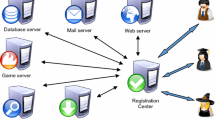
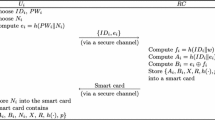
The paper firstly proposed a provable privacy-protection system (PPPS) which can achieve two kinds of privacy protection and switch between them optionally by users: The first is anonymous scheme which can make nobody know the users’ identity, including the server and the registration center (RC), and they only know these users are legal or paying members. The other is hiding identity scheme which owns also privacy-protection property, because the user’s identity is not transferred during the process of the proposed protocol, and only the server and the RC know the user’s identity. About practical environment, we adopt multi-server architecture which can allow the user to register at the RC once and can access all the permitted services provided by the eligible servers. Then a new PPPS authenticated key agreement protocol is given based on chaotic maps. Security of the scheme is based on chaotic maps hard problems, a secure one-way hash function and a secure symmetric cryptosystem. Compared with the related literatures recently, our proposed scheme can not only own high efficiency and unique functionality, but is also robust to various attacks and achieves perfect forward secrecy. Finally we give the security proof and the efficiency analysis of our proposed scheme.






Similar content being viewed by others
Notes
The Onion Router, an anonymous Internet communication system.
References
Katz, J., MacKenzie, P., Taban, G., Gligor, V.: Two-server password-only authenticated key exchange. Appl. Cryptogr. Netw. Secur. 3531, 1–16 (2005)
Zhu, H.: A provable one-way authentication key agreement scheme with user anonymity for multi-server environment. KSII Trans. Internet Inf. Syst. 9(2), 811–829 (2015)
Baptista, M.S.: Cryptography with chaos. Phys. Lett. A 240(1), 50–54 (1998)
Lee, C., Li, C., Hsu, C.: A three-party password-based authenticated key exchange protocol with user anonymity using extended chaotic maps. Nonlinear Dyn 73, 125–132 (2013)
Bresson, E., Chevassut, O., Pointcheval, D.: Group Diffie-Hellman key exchange secure against dictionary attack. Asiacrypt 2501, 497–514 (2002)
Li, H., Wu, C.-K., Sun, J.: A general compiler for password-authenticated group key exchange protocol. Inf. Process. Lett. 110, 160–167 (2010)
Wu, T.Y., Tseng, Y.M., Tsai, T.T.: A revocable ID-based authenticated group key exchange protocol with resistant to malicious participants. Comput. Netw. 56(12), 2994–3006 (2012)
Tseng, H., Jan, R., Yang, W.: A chaotic maps-based key agreement protocol that preserves user anonymity. In: IEEE International Conference on Communications ( ICC09), pp. 1–6, (2009)
Di Raimondo, M., Gennaro, R.: Provably secure threshold password-authenticated key exchange. J. Comput. Syst. Sci. 72(6), 978–1001 (2006)
Khan, M.K., Zhang, J.: Improving the security of a flexible biometrics remote user authentication scheme. Comput. Stand Interfaces 29(1), 82–85 (2007)
Li, L.H., Lin, I.C., Hwang, M.S.: A remote password authentication scheme for multi-server architecture using neural networks. IEEE Trans. Neural Netw. 12(6), 1498–1504 (2001)
Lin, I.C., Hwang, M.S., Li, L.H.: A new remote user authentication scheme for multi-server architecture. Future Gener. Comput. Syst. 19(1), 13–22 (2003)
Tsai, J.L.: Efficient multi-server authentication scheme based on one-way hash function without verification table. Comput. Secur. 27(3–4), 115–121 (2008)
Ravi, S.P., Jaidhar, C.D., Shashikala, T.: Robust smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. 72(1), 729–745 (2013)
Goldberg, I.: On the security of the tor authentication protocol. In: Danezis, G., Golle, P. (eds.) Privacy Enhancing Technologies, 6th International Workshop, PET 2006, Cambridge, UK, June 28-30, 2006. Revised Selected Papers, vol. 4258, pp. 316–331. Springer, Berlin (2006)
Kate, A., Zaverucha, G.M., Goldberg, I.: Pairing-based onion routing with improved forward secrecy. ACM Trans. Inf. Syst. Secur. 13(4), 29 (2010)
Morrissey, P., Smart, N.P., Warinschi, B.: A modular security analysis of the TLS handshake protocol. Adv. Cryptol. Proc. 5350, 55–73 (2008)
Goldberg, I., Stebila, D., Ustaoglu, B.: Anonymity and one-way authentication in key exchange protocols. Des. Codes Cryptogr. 67, 245–269 (2013)
Dierks, T., Allen, C.: The TLS protocol version 1.0, (1999). http://www.ietf.org/rfc/rfc2246.txt RFC 2246
NIST National Institute of Standards and Technology, Special Publication 800–56B, Recommendation for pair-wise key establishment schemes using integer factorization cryptography. http://csrc.nist.gov/publications/PubsSPs.html (2009)
Wang, X., Zhao, J.: An improved key agreement protocol based on chaos. Commun. Nonlinear Sci. Numer. Simul. 15, 4052–4057 (2010)
Zhang, L.: Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos Solitons Fractals 37(3), 669–674 (2008)
Kocarev, L., Lian, S. (eds.): Chaos-based cryptography: Theory, algorithms and applications. In: Studies in Computational Intelligence, vol. 354, pp. 53–54. Springer, Berlin (2011)
Ravi, S.P., Jaidhar, C.D., Shashikala, T.: Robust smart card authentication scheme for multi-server architecture. Wirel. Pers. Commun. 72, 729–745 (2013)
Canetti, R., Krawczyk, H.: Analysis of key-exchange protocols and their use for building secure channels. EUROCRYPT, Vol. 2045 of Lecture Notes in Computer Science. pp. 453–474, (2001)
Chen, T.-Y., Lee, C.-C., Hwang, M.-S., Jan, J.-K.: Towards secure and efficient user authentication scheme using smart card for multi-server environments. J. Supercomput. 66(2), 1008–1032 (2013)
Tsai, J.L.: Efficient multi-server authentication scheme based on one-way hash function without verification table. Comput. Secur. 27(3–4), 115–121 (2008)
Liao, Y.P., Wang, S.S.: A secure dynamic ID based remote user authentication scheme for multiserver environment. Comput. Stand Interfaces 31(1), 24–29 (2009)
Hsiang, H.C., Shih, W.K.: Improvement of the secure dynamic ID based remote user authentication scheme for multi-server environment. Comput. Stand Interfaces 31(6), 1118–1123 (2009)
Ying-Qian, Z., Xing-Yuan, W.: A symmetric image encryption algorithm based on mixed linear-nonlinear coupled map lattice. Inf. Sci. 273, 329–351 (2014)
Niu, Y., Wang, X.: An anonymous key agreement protocol based on chaotic maps. Commun. Nonlinear Sci. Numer. Simulat. 16, 1986–1992 (2011)
Wang, X., Luan, D., Bao, X.: Cryptanalysis of an image encryption algorithm using Chebyshev generator. Digital Signal Process. 25, 244–247 (2014)
Wang, X., Luan, D.: A secure key agreement protocol based on chaotic maps. Chin. Phys. B 22(11), 110503 (2013)
Wang, X., Luan, D.: A novel image encryption algorithm using chaos and reversible cellular automata. Commun. Nonlinear Sci. Numer. Simul. 18, 3075–3085 (2013)
Xing-yuan, W., Yong-feng, G.: A switch-modulated method for chaos digital secure communication based on user-defined protocol. Commun. Nonlinear Sci. Numer. Simul. 15, 99–104 (2010)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhu, H. A provable privacy-protection system for multi-server environment. Nonlinear Dyn 82, 835–849 (2015). https://doi.org/10.1007/s11071-015-2198-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-015-2198-7