Abstract
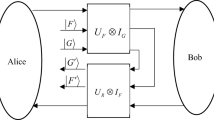
A detailed analysis has showed that the quantum secret sharing protocol based on the Grover algorithm (Phys Rev A, 2003, 68: 022306) is insecure. A dishonest receiver may obtain the full information without being detected. A quantum secret-sharing protocol is presents here, which mends the security loophole of the original secret-sharing protocol, and doubles the information capacity.
Similar content being viewed by others
References
Schneier B. Applied Cryptography: Protocols, Algorithms, and Source Code in C. 2nd ed. New York: John Wiley and Sons, Inc., 1996. 70
Gruska J. Foundations of Computing. London: Thomson Computer Press, 1997. 504
Hillery M, Bu E K V, Berthiaume A. Quantum secret sharing. Phys Rev A, 1999, 59: 1829–1832
Cleve R, Gottesman D, Lo H K. How to share a quantum secret. Phys Rev Lett, 1999, 83: 648–651
Karlsson A, Koashi M, Imoto N. Quantum entanglement for secret sharing and secret splitting. Phys Rev A, 1999, 59: 162–168
Gottesman D. Theory of quantum secret sharing. Phys Rev A, 2000, 61: 042311
Bandyopadhyay S. Teleportation and secret sharing with pure entangled states. Phys Rev A, 2000, 62: 012308
Xiao L, Long G L, Deng F G, et al. Efficient multiparty quantum-secret-sharing schemes. Phys Rev A, 2004, 69: 052307
Cabello A. N-particle N-level singlet states: Some properties and applications. Phys Rev Lett, 2002, 89: 100402
Deng F G, Zhou H Y, Long G L. Bidirectional quantum secret sharing and secret splitting with polarized single photons. Phys Lett A, 2005, 337: 329–334
Chen P, Deng F G, Long G L. High-dimension multiparty quantum secret sharing scheme with Einstein-Podolsky-Rosen pairs. Chin Phys, 2006, 15: 2228–2235
Song J, Zhang S. Secure quantum secret sharing based on reusable GHZ states as secure carriers. Chin Phys Lett, 2006, 23(6): 1383–1836
Wang X, Liu YM, Han L F, et al. Multiparty quantum secret of secure direct communication with high-dimensional quantum superdense coding. Int J Quant Inform, 2008, 6: 1155–1163
Gao T, Yan F L, Li Y C. Quantum secret sharing between m-party and n-party with six states. Sci China Ser G-Phy Mech Astron, 2009, 52: 1191–1202
Yan F L, Gao T, Li Y C. Quantum secret sharing between multiparty and multiparty with four states. Sci China Ser G-Phys Mech Astron, 2007, 50: 572–580
Yang Y G, Wen Q Y, Zhu F C. An efficient quantum secret sharing protocol with orthogonal product states. Sci China Ser G-Phys Mech Astron, 2007, 50: 331–338
Yang Y G, Wen Q Y. Threshold quantum secure direct communication without entanglement. Sci China Ser G-Phys Mech Astron, 2008, 51(2): 176–183
Hsu L Y. Quantum secret-sharing protocol based on Grover’s algorithm. Phys Rev A, 2003, 68: 022306
Wang C, Sheng Y B, Li X H, et al. Efficient entanglement purification for doubly entangled photon state. Sci China Ser E-Tech Sci, 2009, 52(12): 3464–3467
Wang W Y, Wang C, Zhang G Y, et al. Arbitrarily long distance quantum communication using inspection and power insertion. Chin Sci Bull, 2009, 54(1): 158–162
Wen H, Han Z F, Zhao Y B, et al. Multiple stochastic paths scheme on partiallytrusted relay quantum key distribution network. Sci China Ser F-Inf Sci, 2009, 52(1): 18–22
Xu FX, Chen W, Wang S, et al. Field experiment on a robust hierarchical metropolitan quantum cryptography network. Chin Sci Bull, 2009, 54: 2991–2997
Zhang X L, Ji D Y. Analysis of a kind of quantum cryptographic schemes based on secret sharing. Sci China Ser G-Phys Mech Astron, 2009, 52(9): 1313–1316
Gao T, Yan F L, Li Y C, et al. Quantum secret sharing between m-party and n-party with six states. Sci China Ser G-Phys Mech Astron, 2009, 52(8): 1191–1202
Yang Y G, Wen Q Y. Threshold quantum secret sharing between multiparty and multi-party. Sci China Ser G-Phys Mech Astron, 2009, 51(9): 1308–1315
Yang Y G, Wen Q Y, Zhang X. Multiparty simultaneous quantum identity authentication with secret sharing. Sci China Ser G-Phys Mech Astron, 2008, 51(3): 321–327
Tittel W, Zbinden H, Gisin N. Experimental demonstration of quantum secret sharing. Phys Rev A, 2001, 63: 042301
Hao L, Wang C, Long G L. Experimental demonstration of a quantum secret-sharing using Grover algorithm, submitted
Grover L K. Quantum mechanics helps in searching for a needle in a haystack. Phys Rev Lett, 1997, 79: 325–328
Grover L K. A fast quantum mechanical algorithm for database search. In: Proceedings of the 28th Annual ACM Symposium on the Theory of Computation. New York: ACM Press, 1996. 212–219
Long G L. Grover algorithm with zero theoretical failure rate. Phys Rev A, 2001, 64: 022307
Lo H-K, Chau H F. Is quantum bit commitment really possible? Phys Rev Lett, 1997, 78: 3410–3413; Mayers D. Unconditionally secure quantum bit commitment is impossible. Phys Rev Lett, 1997, 78: 3414–3417
Lo H-K, Chau H F. Unconditional security of quantum key distribution over arbitrarily long distances. Science, 1999, 283: 2050–2056
Bennett C H, Wiesner S J. Communication via one- and two-particle operators on Einstein-Podolsky-Rosen states. Phys Rev Lett, 1992, 69: 2881–2884
Liu X S, Long G L, Tong D M, et al. General scheme for superdense coding between multiparties. Phys Rev A, 2002, 65: 022304
Li C Y, Li X H, Deng F G, et al. Complete multiple round quantum dense coding with quantum logical network. Chin Sci Bull, 2007, 52(9): 1162–1165
Wei D X, Yang X D, Luo J, et al. NMR experimental implementation of three-parties quantum superdense coding. Chin Sci Bull, 2004, 49(5): 423–426
Bruß D. Optimal eavesdropping in quantum cryptography with six states. Phys Rev Lett, 1998, 81: 3018–3021
Chen P, Deng F G, Wang P X, et al. Measuring-basis-encrypted six-state quantum key distribution scheme. Prog Nat Sci, 2006, 16(1): 84–89
Bennett C H, Brassard G. Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India. New York: IEEE, 1984. 175–179
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hao, L., Li, J. & Long, G. Eavesdropping in a quantum secret sharing protocol based on Grover algorithm and its solution. Sci. China Phys. Mech. Astron. 53, 491–495 (2010). https://doi.org/10.1007/s11433-010-0145-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11433-010-0145-7