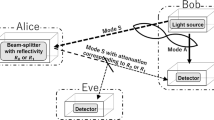
Abstract
Quantum secure direct communication provides a direct means of conveying secret information via quantum states among legitimate users. The past two decades have witnessed its great strides both theoretically and experimentally. However, the security analysis of it still stays in its infant. Some practical problems in this field to be solved urgently, such as detector efficiency mismatch, side-channel effect and source imperfection, are propelling the birth of a more impeccable solution. In this paper, we establish a new framework of the security analysis driven by numerics where all the practical problems may be taken into account naturally. We apply this framework to several variations of the DL04 protocol considering real-world experimental conditions. Also, we propose two optimizing methods to process the numerical part of the framework so as to meet different requirements in practice. With these properties considered, we predict the robust framework would open up a broad avenue of the development in the field.
Similar content being viewed by others
References
G.-L. Long and X.-S. Liu, Theoretically efficient high-capacity quantum-key-distribution scheme, Phys. Rev. A 65(3), 032302 (2002)
G. L. Long, F. G. Deng, C. Wang, X. H. Li, K. Wen, and W. Y. Wang, Quantum secure direct communication and deterministic secure quantum communication, Front. Phys. China 2(3), 251 (2007)
F. G. Deng, G. L. Long, and X. S. Liu, Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block, Phys. Rev. A 68(5), 042317 (2003)
C. Wang, F. G. Deng, Y. S. Li, X. S. Liu, and G. L. Long, Quantum secure direct communication with highdimension quantum superdense coding, Phys. Rev. A 71(4), 044305 (2005)
F. G. Deng and G. L. Long, Secure direct communication with a quantum one-time pad, Phys. Rev. A 69(5), 052319 (2004)
F. G. Deng, X. H. Li, C. Y. Li, P. Zhou, and H. Y. Zhou, Quantum secure direct communication network with Einstein-Podolsky-Rosen pairs, Phys. Lett. A 359(5), 359 (2006)
F. G. Deng, X. H. Li, C. Y. Li, P. Zhou, and H. Y. Zhou, Economical quantum secure direct communication network with single photons, Chin. Phys. 16(12), 3553 (2007)
Z. R. Zhou, Y. B. Sheng, P. H. Niu, L. G. Yin, G. L. Long, and L. Hanzo, Measurement-device-independent quantum secure direct communication, Sci. China Phys. Mech. Astron. 63(3), 230362 (2020)
P. H. Niu, Z. R. Zhou, Z. S. Lin, Y. B. Sheng, L. G. Yin, and G. L. Long, Measurement-device-independent quantum communication without encryption, Sci. Bull. 63(20), 1345 (2018)
Z. Gao, T. Li, and Z. Li, Long-distance measurement-device-independent quantum secure direct communication, EPL 125(4), 40004 (2019)
Z. K. Zou, L. Zhou, W. Zhong, and Y. B. Sheng, Measurement-device-independent quantum secure direct communication of multiple degrees of freedom of a single photons, EPL 131(4), 40005 (2020)
X. D. Wu, L. Zhou, W. Zhong, and Y. B. Sheng, High-capacity measurement-device-independent quantum secure direct communication, Quantum Inform. Process. 19(4), 354 (2020)
L. Zhou, Y. B. Sheng, and G. L. Long, Device-independent quantum secure direct communication against collective attacks, Sci. Bull. 65(1), 12 (2020)
J. H. Shapiro, Z. Zhang, and F. N. Wong, Secure communication via quantum illumination, Quantum Inform. Process. 13(1), 2171 (2014)
D. J. Lum, J. C. Howell, M. S. Allman, T. Gerrits, V. B. Verma, S. W. Nam, C. Lupo, and S. Lloyd, Quantum enigma machine: Experimentally demonstrating quantum data locking, Phys. Rev. A 94(2), 022315 (2016)
J. H. Shapiro, D. M. Boroson, P. B. Dixon, M. E. Grein, and S. A. Hamilton, Quantum low probability of intercept, J. Opt. Soc. Am. B 36(3), B41 (2019)
J. Y. Hu, B. Yu, M. Y. Jing, L. T. Xiao, S. T. Jia, G. Q. Qin, and G. L. Long, Experimental quantum secure direct communication with single photons, Light Sci. Appl. 5(9), e16144 (2016)
W. Zhang, D. S. Ding, Y. B. Sheng, L. Zhou, B. S. Shi, and G. C. Guo, Quantum secure direct communication with quantum memory, Phys. Rev. Lett. 118(22), 220501 (2017)
F. Zhu, W. Zhang, Y. Sheng, and Y. Huang, Experimental long-distance quantum secure direct communication, Sci. Bull. 62(22), 1519 (2017)
D. Pan, Z. Lin, J. Wu, H. Zhang, Z. Sun, D. Ruan, L. Yin, and G. Long, Experimental free-space quantum secure direct communication and its security analysis, Photon. Res. 8(9), 1522 (2020)
S. Pirandola, S. L. Braunstein, S. Lloyd, and S. Mancini, Confidential direct communications: A quantum approach using continuous variables, IEEE J. Sel. Top. Quantum Electron. 15(6), 1570 (2009)
C. Liu, K. Pang, Z. Zhao, P. Liao, R. Zhang, H. Song, Y. Cao, J. Du, L. Li, H. Song, Y. Ren, G. Xie, Y. Zhao, J. Zhao, S. M. H. Rafsanjani, A.N. Willner, J. H. Shapiro, R. W. Boyd, M. Tur, and A. E. Willner, Single-end adaptive optics compensation for emulated turbulence in a bidirectional 10-Mbit/s per channel free-space quantum communication link using orbital-angular-momentum encoding, Research 2019, 8326701 (2019)
N. Killoran, T. R. Bromley, J. M. Arrazola, M. Schuld, N. Quesada, and S. Lloyd, Continuous-variable quantum neural networks, Phys. Rev. Research 1(3), 033063 (2019)
C. Q. Hu, J. Gao, L. F. Qiao, R. J. Ren, Z. Cao, Z. Q. Yan, Z. Q. Jiao, H. Tang, Z. H. Ma, and X. M. Jin, Experimental test of tracking the king problem, Research 2019, 3474305 (2019)
R. Qi, Z. Sun, Z. Lin, P. Niu, W. Hao, L. Song, Q. Huang, J. Gao, L. Yin, and G. L. Long, Implementation and security analysis of practical quantum secure direct communication, Light Sci. Appl. 8(1), 22 (2019)
H. Lu, C. H. F. Fung, X. Ma, and Q. Y. Cai, Unconditional security proof of a deterministic quantum key distribution with a two-way quantum channel, Phys. Rev. A 84(4), 042344 (2011)
C. I. Henao and R. M. Serra, Practical security analysis of two-way quantum-key-distribution protocols based on nonorthogonal states, Phys. Rev. A 92(5), 052317 (2015)
J. Wu, Z. Lin, L. Yin, and G. L. Long, Security of quantum secure direct communication based on Wyner’s wiretap channel theory, Quantum Engineering 1(4), e26 (2019)
P. J. Coles, E. M. Metodiev, and N. Lütkenhaus, Numerical approach for unstructured quantum key distribution, Nat. Commun. 7(1), 11712 (2016)
A. Winick, N. Lütkenhaus, and P. J. Coles, Reliable numerical key rates for quantum key distribution, Quantum 2, 77 (2018)
L. M. Liang, S. H. Sun, M. S. Jiang, and C. Y. Li, Security analysis on some experimental quantum key distribution systems with imperfect optical and electrical devices, Front. Phys. 9(5), 613 (2014)
Z. Cao, Z. Zhang, H. K. Lo, and X. Ma, Discrete-phaserandomized coherent state source and its application in quantum key distribution, New J. Phys. 17(5), 053014 (2015)
C. H. Bennett, G. Brassard, and N. D. Mermin, Quantum cryptography without Bell’s theorem, Phys. Rev. Lett. 68(5), 557 (1992)
A. D. Wyner, The wire-tap channel, Bell Sys. Tech. J. 54(8), 1355 (1975)
G. Ribordy, J. Gautier, N. Gisin, O. Guinnard, and H. Zbinden, Automated “plug & play” quantum key distribution, Electron. Lett. 34(22), 2116 (1998)
P. J. Coles, L. Yu, V. Gheorghiu, and R. B. Griffiths, Information-theoretic treatment of tripartite systems and quantum channels, Phys. Rev. A 83(6), 062338 (2011)
P. J. Coles, Unification of different views of decoherence and discord, Phys. Rev. A 85(4), 042103 (2012)
S. Watanabe, R. Matsumoto, and T. Uyematsu, Tomography increases key rates of quantum-key-distribution protocols, Phys. Rev. A 78(4), 042316 (2008)
E. Bolduc, G. C. Knee, E. M. Gauger, and J. Leach, Projected gradient descent algorithms for quantum state tomography, npj Quantum Inf. 3(1), 1 (2017)
I. Sutskever, J. Martens, G. Dahl, and G. Hinton, On the importance of initialization and momentum in deep learning, in: International conference on machine learning, 2013, p. 1139
M. Jaggi, Revisiting Frank-Wolfe: Projection-free sparse convex optimization, in: Proceedings of the 30th international conference on machine learning, CONF, 2013, p. 427
L. Lydersen, C. Wiechers, C. Wittmann, D. Elser, J. Skaar, and V. Makarov, Hacking commercial quantum cryptography systems by tailored bright illumination, Nat. Photonics 4(10), 686 (2010)
S. Sajeed, P. Chaiwongkhot, J. P. Bourgoin, T. Jennewein, N. Lütkenhaus, and V. Makarov, Security loophole in free-space quantum key distribution due to spatial-mode detector-efficiency mismatch, Phys. Rev. A 91(6), 062301 (2015)
J. Lin, T. Upadhyaya, and N. Lütkenhaus, Asymptotic security analysis of discrete-modulated continuous variable quantum key distribution, Phys. Rev. X 9(4), 041064 (2019)
Acknowledgements
We would like to thank Jiawei Wu for his generous providing of the comparison data in Fig. 3 and thank Jie Lin for the help of the numerical techniques. This work was supported by the National Key Research and Development Program of China under Grant No. 2017YFA0303700, the Key Research and Development Program of Guangdong province under Grant No. 2018B030325002, the National Natural Science Foundation of China under Grant No. 11974205, and Beijing Advanced Innovation Center for Future Chip (ICFC).
Author information
Authors and Affiliations
Corresponding authors
Additional information
arXiv: 2011.14546. This article can also be found at http://journal.hep.com.cn/fop/EN/10.1007/s11467-020-1025-x.
Rights and permissions
About this article
Cite this article
Ye, ZD., Pan, D., Sun, Z. et al. Generic security analysis framework for quantum secure direct communication. Front. Phys. 16, 21503 (2021). https://doi.org/10.1007/s11467-020-1025-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11467-020-1025-x