Abstract
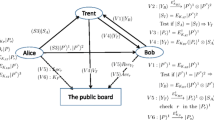
Very recently, an arbitrated quantum signature (AQS) scheme of classical message with an untrusted arbitrator was presented (Yang et al. in Eur. Phys. J., D, At. Mol. Opt. Plasma Phys. 61(3):773–778, 2011). In this paper, the security of the AQS scheme with an untrusted arbitrator is analyzed. An AQS scheme with an untrusted arbitrator should satisfy the unforgeable property and undeniable property. In particular, the malicious verifier can not modify a message and its signature to produce a new message with a valid signature, and the dishonest signer who really has sent the message to the verifier which the verifier accepted as an authentic one cannot later deny having sent this message. However, we show that, in the AQS scheme with an untrusted arbitrator, the dishonest signer can successfully disavow his/her signature and the malicious verifier can counterfeit a valued signature for any message by known message attack when he has received a message-signature pair. Then, we suggest an improved AQS scheme of classical message with an untrusted arbitrator which can solve effectively the two problems raised above. Furthermore, we prove the security of the improved scheme.
Similar content being viewed by others
References
Shor, P.W.: Algorithms for quantum computation: discrete logarithms and factoring. In: The 35th Annual Symposium on Proceedings of Foundations of Computer Science, 1994, pp. 124–134. IEEE, New York (1994)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, pp. 175–179. IEEE, New York (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121–3124 (1992)
Lo, H.K., Chau, H.F.: Unconditional security of quantum key distribution over arbitrarily long distances. Science 283(5410), 2050 (1999)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Mayers, D.: Unconditional security in quantum cryptography. J. ACM 48(3), 351–406 (2001)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–195 (2002)
Inamori, H., Lütkenhaus, N., Mayers, D.: Unconditional security of practical quantum key distribution. Eur. Phys. J., D, At. Mol. Opt. Plasma Phys. 41(3), 599–627 (2007)
Gottesman, D., Chuang, I.: Quantum digital signatures. arXiv:quant-ph/0105032 (2001)
Barnum, H., Crépeau, C., Gottesman, D., Smith, A., Tapp, A.: Authentication of quantum messages. In: The 43rd Annual IEEE Symposium on Foundations of Computer Science, 2002, pp. 449–458. IEEE, New York (2002)
Curty, M., Santos, D.J., Pérez, E., García-Fernández, P.: Qubit authentication. Phys. Rev. A 66(2), 022301 (2002)
Zeng, G., Keitel, C.H.: Arbitrated quantum-signature scheme. Phys. Rev. A 65(4), 042312 (2002)
Li, Q., Chan, W.H., Long, D.Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 79(5), 054307 (2009)
Lee, H., Hong, C., Kim, H., Lim, J., Yang, H.J.: Arbitrated quantum signature scheme with message recovery. Phys. Lett. A 321(5), 295–300 (2004)
Lu, X., Feng, D.: Quantum digital signature based on quantum one-way functions. In: The 7th International Conference on Advanced Communication Technology, 2005 (ICACT 2005), vol. 1, pp. 514–517. IEEE, New York (2004)
Wang, J., Zhang, Q., Tang, C.: Quantum signature scheme with message recovery. In: The 8th International Conference on Advanced Communication Technology, 2006 (ICACT 2006), vol. 2, pp. 1375–1378. IEEE, New York (2006)
Wang, J., Zhang, Q., Tang, C.: Quantum signature scheme with single photons. Optoelectron. Lett. 2(3), 209–212 (2006)
Wen, X., Liu, Y., Sun, Y.: Quantum multi-signature protocol based on teleportation. Z. Naturforsch. A 62(3/4), 147 (2007)
Zeng, G., Lee, M., Guo, Y., He, G.: Continuous variable quantum signature algorithm. Int. J. Quantum Inf. 5(4), 553–573 (2007)
Yang, Y.G.: Multi-proxy quantum group signature scheme with threshold shared verification. Chin. Phys. B 17, 415 (2008)
Lü, X., Feng, D.G.: An arbitrated quantum message signature scheme. In: Computational and Information Science, pp. 1054–1060 (2005)
Cao, Z., Markowitch, O.: Security analysis of one quantum digital signature scheme. In: The Sixth International Conference on Information Technology: New Generations, 2009 (ITNG’09), pp. 1574–1576. IEEE, New York (2009)
Zou, X., Qiu, D.: Security analysis and improvements of arbitrated quantum signature schemes. Phys. Rev. A 82(4), 042325 (2010)
Curty, M., Lütkenhaus, N.: Comment on “Arbitrated quantum-signature scheme”. Phys. Rev. A 77(4), 046301 (2008)
Zeng, G.: Reply to “Comment on ‘Arbitrated quantum-signature scheme’’’. Phys. Rev. A 78(1), 016301 (2008)
Greenberger, D.M., Horne, M.A., Zeilinger, A.: Going beyond Bell’s theorem. arXiv:0712.0921 (2007)
Greenberger, D.M., Bernstein, H.J., Horne, M.A., Shimony, A., Zeilinger, A.: Proposed GHZ experiments using cascades of down-conversions. In: Quantum Control and Measurement, vol. 1, p. 23 (1993)
Boykin, P.O., Roychowdhury, V.: Optimal encryption of quantum bits. Phys. Rev. A 67(4), 042317 (2003)
Ingemarsson, I., Simmons, G.: A protocol to set up shared secret schemes without the assistance of a mutually trusted party. In: Advances in Cryptology, 1990 (EUROCRYPT’90), pp. 266–282. Springer, Berlin (2006)
Cao, Z., Markowitch, O.: A note on an arbitrated quantum signature scheme. Int. J. Quantum Inf. 7(6), 1205–1209 (2009)
Yang, Y.G., Zhou, Z., Teng, Y.W., Wen, Q.Y.: Arbitrated quantum signature with an untrusted arbitrator. Eur. Phys. J., D, At. Mol. Opt. Plasma Phys. 61(3), 773–778 (2011)
Acknowledgements
This work is supported in part by the National Natural Science Foundation (Nos. 61272058, 61073054, 60873055), the Natural Science Foundation of Guangdong Province of China (Nos. 10251027501000004, S2012040007324, S2012010008833), the Specialized Research Fund for the Doctoral Program of Higher Education of China (No. 20100171110042), the Fundamental Research Funds for the Central Universities (No. 10lgzd12), the Foundation for Distinguished Young Talents in Higher Education of Guangdong Province of China (No. 2012LYM_0126), the Science and Technology Project of Jiangmen City of China (No. [2011]131), and the project of SQIG at IT, funded by FCT and EU FEDER projects QSecPTDC/EIA/67661/2006, AMDSC UTAustin/MAT/0057/2008, NoE Euro-NF, and IT Project QuantTel, FCT project PTDC/EEA-TEL/103402/2008 QuantPrivTel, FCT PEst-OE/EEI/LA0008/2011.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zou, X., Qiu, D. & Mateus, P. Security Analyses and Improvement of Arbitrated Quantum Signature with an Untrusted Arbitrator. Int J Theor Phys 52, 3295–3305 (2013). https://doi.org/10.1007/s10773-013-1626-z
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-013-1626-z