Abstract
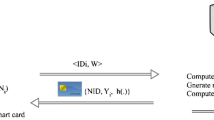
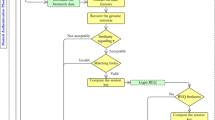
Telecare medicine information systems (TMIS) present the platform to deliver clinical service door to door. The technological advances in mobile computing are enhancing the quality of healthcare and a user can access these services using its mobile device. However, user and Telecare system communicate via public channels in these online services which increase the security risk. Therefore, it is required to ensure that only authorized user is accessing the system and user is interacting with the correct system. The mutual authentication provides the way to achieve this. Although existing schemes are either vulnerable to attacks or they have higher computational cost while an scalable authentication scheme for mobile devices should be secure and efficient. Recently, Awasthi and Srivastava presented a biometric based authentication scheme for TMIS with nonce. Their scheme only requires the computation of the hash and XOR functions.pagebreak Thus, this scheme fits for TMIS. However, we observe that Awasthi and Srivastava’s scheme does not achieve efficient password change phase. Moreover, their scheme does not resist off-line password guessing attack. Further, we propose an improvement of Awasthi and Srivastava’s scheme with the aim to remove the drawbacks of their scheme.



Similar content being viewed by others
References
Latré, B., Braem, B., Moerman, I., Blondia, C., Demeester, P., A survey on wireless body area networks. Wirel. Netw. 17(1):1-18, 2011.
Khan, M. K., Kumari, S., An authentication scheme for secure access to healthcare services. J. Med. Syst. 37(4):1-12, 2013.
Srivastava, K., Awasthi, A. K., Mittal, R., A review on remote user authentication schemes using smart cards. In: Quality, Reliability, Security and Robustness in Heterogeneous Networks. Springer (2013) 729–749.
Cao, T., Zhai, J., Improved dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 37(2):1-7, 2013.
Chen, H. M., Lo, J. W., Yeh, C. K., An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. J. Med. Syst. 36(6):3907-3915, 2012.
Chen, Y. Y., Lu, J. C., Jan, J. K., A secure ehr system based on hybrid clouds. J. Med. Syst. 36(5):3375–3384, 2012.
Das, A. K., Bruhadeshwar, B., An improved and effective secure password-based authentication and key agreement scheme using smart cards for the telecare medicine information system. J. Med. Syst. 37(5):1–17, 2013.
Debiao, H., Jianhua, C., Rui, Z., A more secure authentication scheme for telecare medicine information systems. J. Med. Syst. 36(3):1989–1995, 2012.
Guo, R., Wen, Q., Shi, H., Jin, Z., Zhang, H., An efficient and provably-secure certificateless public key encryption scheme for telecare medicine information systems. J. Med. Syst. 37(5):1–11, 2013.
Jiang, Q., Ma, J., Ma, Z., Li, G., A privacy enhanced authentication scheme for telecare medical information systems. J. Med. Syst. 37(1):1-8, 2013.
Jiang, Q., Ma, J., Lu, X., Tian, Y., Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. J. Med. Syst. 38(2):1–18, 2014.
Kumari, S., Khan, M. K., Kumar, R., Cryptanalysis and improvement of a privacy enhanced scheme for telecare medical information systems. J. Med. Syst. 37(4):1–11, 2013.
Lee, T. F. An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. J. Med. Syst. 37(6):1–9, 2013.
Lee, T. F., Liu, C. M., A secure smart-card based authentication and key agreement scheme for telecare medicine information systems. J. Med. Syst. 37(3):1–8, 2013.
Lin, S. S., Hung, M. H., Tsai, C .L., Chou, L. P., Development of an ease-of-use remote healthcare system architecture using rfid and networking technologies. J. Med. Syst. 36(6):3605–3619, 2012.
Pu, Q., Wang, J., Zhao, R., Strong authentication scheme for telecare medicine information systems. J. Med. Syst. 36(4):2609–2619, 2012
Siddiqui, Z., Abdullah, A. H., Khan, M. K., Alghamdi, A. S., Smart environment as a service: Three factor cloud based user authentication for telecare medical information system. J. Med. Syst. 38(1):1–14, 2014.
Wu, Z. Y., Lee, Y. C., Lai, F., Lee, H. C., Chung, Y., A secure authentication scheme for telecare medicine information systems. J. med. syst. 36(3):1529–1535, 2012.
Xie, Q., Zhang, J., Dong, N., Robust anonymous authentication scheme for telecare medical information systems. J. med. syst. 37(2):1–8, 2013.
Xu, X., Zhu, P., Wen, Q., Jin, Z., Zhang, H., He, L., A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. J. Med. Syst. 38(1):1–7, 2014.
Zhu, Z., An efficient authentication scheme for telecare medicine information systems. J. Med. Syst. 36(6):3833–3838, 2012.
Boyd, C., and Mathuria, A., Protocols for authentication and key establishment. Springer (2003)
Leng, L., Teoh, A. B. J., Li, M., Khan, M. K., A remote cancelable palmprint authentication proto- col based on multi-directional two-dimensional palmphasor-fusion. Secur. Commun. Networks, doi:10.1002/sec.900, 2013.
Bowyer, K. W., Hollingsworth, K. P., Flynn, P. J., A survey of iris biometrics research: 2008–2010. In: Handbook of iris recognition. Springer (2013) 15–54
Li, C. T., Hwang, M. S., An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 33(1):1–5, 2010.
Li, X., Niu, J. W., Ma, J., Wang, W. D., Liu, C. L., Cryptanalysis and improvement of a biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 34(1):73–79, 2011.
Truong, T. T., Tran, M. T., Duong, A. D., Robust biometrics based remote user authentication scheme using smart cards. In: 15th IEEE International Conference on Network-Based Information Systems (NBiS’2012), pp. 384–391, 2012
Awasthi, A. K, and Srivastava, K., A biometric authentication scheme for telecare medicine information systems with nonce.J. Med. Syst. 37(5):1–4, 2013.
Jin, A. T. B, Ling, D. N. C, Goh, A., Biohashing: two factor authentication featuring fingerprint data and tokenised random number.Pattern recognit. 37(11):2245–2255, 2004.
Zhou, X., and Kalker, T., On the security of biohashing. In: IS&T/SPIE Electronic Imaging, International Society for Optics and Photonics. pp. 75410–75410, 2010.
Leng, L., and Zhang, J., Palmhash code vs. palmphasor code. Neurocomput. 108:1–12, 2013.
Belguechi, R., Rosenberger, C., Ait-Aoudia, S.: Biohashing for securing minutiae template. In: 20th IEEE International Conference on Pattern Recognition (ICPR’2010), pp. 1168–1171, 2010.
Lumini, A., and Nanni, L., An improved biohashing for human authentication. Pattern Recognit. 40(3):1057–1065, 2007.
Yang, C.: Integration of biometrics and pin pad on smart card. PhD thesis, University of Newcastle Upon Tyne 2011.
Leng, L., Zhang, J., Khan, M. K., Chen, X., Ji, M., Alghathbar, K., Cancelable palmcode generated from randomized gabor filters for palmprint template protection. Sci. Res. Ess. 6(4):784–792, 2011.
Brier, E., Clavier, C., Olivier, F., Correlation power analysis with a leakage model. In: Cryptographic Hardware and Embedded Systems (CHES’2004), pp. 16–29. Springer, 2004.
Eisenbarth, T., Kasper, T., Moradi, A., Paar, C., Salmasizadeh, M., Shalmani, M. T. M., On the power of power analysis in the real world: A complete break of the keeloq code hopping scheme. In: Advances in Cryptology-(CRYPTO’2008), pp. 203–220. Springer, 2008.
Kocher, P., Jaffe, J., Jun, B., Differential power analysis. In: Advances in Cryptology (CRYPTO’99), pp. 388–397. Springer, 1999.
Messerges, T. S., Dabbish, E. A., Sloan, R. H., Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Consum. Electron. 51(5):541–552, 2002
Xu, J., Zhu, W. T., Feng, D. G., An improved smart card based password authentication scheme with provable security. Comput. Stand. Interfaces 31(4):723–728, 2009.
Yang, C. C., Yang, H. W., Wang, R. C., Cryptanalysis of security enhancement for the timestampbased password authentication scheme using smart cards. IEEE Trans. Consum. Electron. 50(2):578–579, 2004.
Chang, Y. F., Yu, S. H., Shiao, D. R., A uniqueness-and-anonymity-preserving remote user authentication scheme for connected health care. J. Med. Syst. 37(2):1–9, 2013
Liao, Y. P., and Wang, S. S., A secure dynamic id based remote user authentication scheme for multi-server environment. Comput. Stand. Interfaces 31(1):24–29, 2009
Potlapally, N. R., Ravi, S., Raghunathan, A., Jha, N. K., A study of the energy consumption characteristics of cryptographic algorithms and security protocols. IEEE Trans. Mob. Comput. 5(2):128–143, 2006
Wong, D. S., Fuentes, H. H., Chan, A. H., The performance measurement of cryptographic primitives on palm devices. In: Proceedings 17th IEEE Annual Computer Security Applications Conference (ACSAC’2001), pp. 92–101, 2001.
Author information
Authors and Affiliations
Corresponding author
Additional information
Conflict of interests
The authors declare that they have no conflict of interest.
This article is part of the Topical Collection on Mobile Systems
Rights and permissions
About this article
Cite this article
Mishra, D., Mukhopadhyay, S., Kumari, S. et al. Security Enhancement of a Biometric based Authentication Scheme for Telecare Medicine Information Systems with Nonce. J Med Syst 38, 41 (2014). https://doi.org/10.1007/s10916-014-0041-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0041-1