Abstract
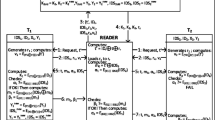
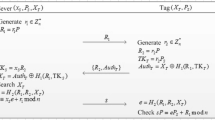
RFID technology is increasingly used in applications that require tracking, identification, and authentication. It attaches RFID-readable tags to objects for identification and execution of specific RFID-enabled applications. Recently, research has focused on the use of grouping-proofs for preserving privacy in RFID applications, wherein a proof of two or more tags must be simultaneously scanned. In 2010, a privacy-preserving grouping proof protocol for RFID based on ECC in public-key cryptosystem was proposed but was shown to be vulnerable to tracking attacks. A proposed enhancement protocol was also shown to have defects which prevented proper execution. In 2012, Lin et al. proposed a more efficient RFID ECC-based grouping proof protocol to promote inpatient medication safety. However, we found this protocol is also vulnerable to tracking and impersonation attacks. We then propose a secure privacy-preserving RFID grouping proof protocol for inpatient medication safety and demonstrate its resistance to such attacks.










Similar content being viewed by others
References
Batina, L., Lee, Y., Seys, S., Singele, D., Verbauwhede, I.: Privacy-preserving ECC-based grouping proofs for RFID. In: Burmester, M., Tsudik, G., Magliveras, S., Ili, I. (Eds.) Information Security, Lecture Notes in Computer Science, Vol. 6531. Heidelberg: Springer-Verlag, (2011). doi:10.1007/978-3-642-18178-8_14.
Chen, C.L., and Wu, C.Y., Using RFID yoking proof protocol to enhance inpatient medication safety. J. Med. Syst. 36(5):2849–2864, 2012. doi:10.1007/s10916-011-9763-5.
Chien, H.Y., Yang, C.C., Wu, T.C., Lee, C.F., Two RFID-based solutions to enhance inpatient medication safety. J.Med. Syst. 35 (3):369–375, 2011. doi:10.1007/s10916-009-9373-7.
Deursen, T.: 50 ways to break RFID privacy. In: Fischer-Hbner, S., Duquenoy, P., Hansen, M., Leenes, R., Zhang, G. (Eds.) Privacy and Identity Management for Life, IFIP Advances in Information and Communication Technology, Vol. 352, pp. 192–205. Springer-Verlag, Heidelberg (2011), doi:10.1007/978-3-642-20769-3_16.
Deursen, T., Mauw, S., Radomirovi, S.: Untraceability of RFID protocols. In: Onieva, J., Sauveron, D., Chaumette, S., Gollmann, D., Markantonakis, K. (Eds.) Information Security Theory and Practices. Smart Devices, Convergence and Next Generation Networks, Lecture Notes in Computer Science, Vol. 5019, pp. 1–15. Springer-Verlag, Heidelberg (2008), doi:10.1007/978-3-540-79966-5_1.
Diffie, W., and Hellman, M., New directions in cryptography. Inf. Theory, IEEE Trans. 22(6):644–654, 1976. doi:10.1109/TIT.1976.1055638.
Galbraith, S., Mathematics of Public Key Cryptography: Cambridge Uuniversity Press, 2012.
Hankerson, D., Menezes, A., Vanstone, S., Guide to Elliptic Curve Cryptography: Springer-Verlag, 2004.
Hein, D., Wolkerstorfer, J., Felber, N.: ECC is ready for RFID - a proof in silicon. In: Avanzi, R., Keliher, L., Sica, F. (Eds.) Selected Areas in Cryptography, Lecture Notes in Computer Science, Vol. 5381, pp. 401–413. Springer-Berlin, Heidelberg (2009), doi:10.1007/978-3-642-04159-4_26.
Huang, H.H., and Ku, C.Y., A RFID grouping proof protocol for medication safety of inpatient. J. Med. Syst. 33(6):467–474, 2009. doi:10.1007/s10916-008-9207-z.
Juels, A.: ”Yoking-Proofs” for RFID tags. In: Proceedings of the Second IEEE Annual Conference on Pervasive Computing and Communications Workshops, PERCOMW ’04, pp. 138–. IEEE Computer Society, Washington, DC, USA, http://dl.acm.org/citation.cfm?id=977405.978626 (2004)
Ko, W., Chiou, S., Lu, E., Chang, H., An improvement of privacy-preserving ECC-based grouping proof for RFID. In: Cross Strait Quad-Regional Radio Science and Wireless Technology Conference (CSQRWC), 2011, vol. 2, pp. 1062–1064. IEEE, 2011.
Koblitz, N., Elliptic curve cryptosystems. Math. Comput 48(177):203–209, 1987. http://www.jstor.org/stable/2007884.
Lin, Q., and Zhang, F., ECC-based grouping-proof RFID for inpatient medication safety. J. Med. Syst. 36(6):3527–3531, 2012. www.scopus.com.
Lv, C., Li, H., Ma, J., Niu, B., Jiang, H., Security analysis of a privacy-preserving ECC-based grouping-proof protocol. J. Converg. Inf. Technol. 6(3):113–119, 2011.
Miller, V.S. Use of elliptic curves in cryptography, pp. 417–426. New York: Springer-Verlag New York, Inc., 1986. http://dl.acm.org/citation.cfm?id=18262.25413.
Vaudenay, S.: On privacy models for RFID. In: Kurosawa, K. (Ed.) Advances in Cryptology ASIACRYPT 2007, Lecture Notes in Computer Science, Vol. 4833, pp. 68–87. Springer-Berlin, Heidelberg (2007), doi:10.1007/978-3-540-76900-2_5.
Wolkerstorfer, J.: Is elliptic-curve cryptography suitable to secure RFID tags? In: Workshop on RFID and Lightweight Crypto (2005)
Acknowledgements
This work was partially supported by the NSC under Grant NSC 102-2221-E-182-038. The authors also gratefully acknowledge the helpful comments and suggestions of the reviewers, which have improved the presentation.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Patient Facing Systems
Rights and permissions
About this article
Cite this article
Ko, WT., Chiou, SY., Lu, EH. et al. Modifying the ECC-Based Grouping-Proof RFID System to Increase Inpatient Medication Safety. J Med Syst 38, 66 (2014). https://doi.org/10.1007/s10916-014-0066-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-014-0066-5