Abstract
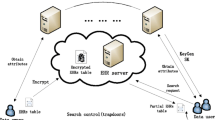
The boom of Internet of Things devices promotes huge volumes of eHealthcare data will be collected and aggregated at eHealthcare provider. With the help of these health data, eHealthcare provider can offer reliable data service (e.g., k-NN query) to doctors for better diagnosis. However, the IT facility in the eHealthcare provider is incompetent with the huge volumes of eHealthcare data, so one popular solution is to deploy a powerful cloud and appoint the cloud to execute the k-NN query service. In this case, since the eHealthcare data are very sensitive yet cloud servers are not fully trusted, directly executing the k-NN query service in the cloud inevitably incurs privacy challenges. Apart from the privacy issues, efficiency issues also need to be taken into consideration because achieving privacy requirement will incur additional computational cost. However, existing focuses on k-NN query do not (fully) consider the data privacy or are inefficient. For instance, the best computational complexity of k-NN query over encrypted eHealthcare data in the cloud is as large as \(O(k\log ^{3} N)\), where N is the total number of data. In this paper, aiming at addressing the privacy and efficiency challenges, we design an efficient and privacy-preserving k-NN query scheme for encrypted outsourced eHealthcare data. Our proposed scheme is characterized by integrating the k d-tree with the homomorphic encryption technique for efficient storing encrypted data in the cloud and processing privacy-preserving k-NN query over encrypted data. Compared with existing works, our proposed scheme is more efficient in terms of privacy-preserving k-NN query. Specifically, our proposed scheme can achieve k-NN computation over encrypted data with \(O(lk\log N)\) computational complexity, where l and N respectively denote the data dimension and the total number of data. In addition, detailed security analysis shows that our proposed scheme is really privacy-preserving under our security model and performance evaluation also indicates that our proposed scheme is indeed efficient in terms of computational cost.





Similar content being viewed by others
References
Philips healthcare case study. https://aws.amazon.com/cn/solutions/case-studies/philips/
Agrawal, R., Kiernan, J., Srikant, R., and Xu, Y.: Order-preserving encryption for numeric data. In: Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 563–574, 2004
Beis, J.S., and Lowe, D.G.: Shape indexing using approximate nearest-neighbour search in high-dimensional spaces. In: 1997 Conference on Computer Vision and Pattern Recognition (CVPR ’97), pp. 1000–1006, 1997
Elmehdwi, Y., Samanthula, B.K., and Jiang, W.: Secure k-nearest neighbor query over encrypted data in outsourced environments. In: International Conference on Data Engineering, pp. 664–675, 2014
Firouzi, F., Rahmani, A.M., Mankodiya, K., Badaroglu, M., Merrett, G.V., Wong, P., and Farahani, B., Internet-of-things and big data for smarter healthcare: From device to architecture, applications and analytics. Futur. Gener. Comput. Syst. 78:583–586, 2018.
Friedman, J.H., Baskett, F., and Shustek, L.J., An algorithm for finding nearest neighbors. IEEE Trans. Comput. 24(10):1000–1006, 1975.
Ghinita, G., Kalnis, P., Khoshgozaran, A., Shahabi, C., and Tan, K.: Private queries in location based services: anonymizers are not necessary. In: Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 121–132, 2008
Hacigümüs, H., Iyer, B.R., and Mehrotra, S.: Efficient execution of aggregation queries over encrypted relational databases. In: Database Systems for Advances Applications, pp. 125–136, 2004
Hore, B., Mehrotra, S., Canim, M., and Kantarcioglu, M., Secure multidimensional range queries over outsourced data. VLDB J. 21(3):333–358, 2012.
Hore, B., Mehrotra, S., and Tsudik, G.: A privacy-preserving index for range queries. In: (e)Proceedings of the Thirtieth International Conference on Very Large Data Bases, pp. 720–731, 2004
Hu, H., Xu, J., Ren, C., and Choi, B.: Processing private queries over untrusted data cloud through privacy homomorphism. In: Proceedings of the 27th International Conference on Data Engineering, pp. 601–612, 2011
Huang, C., Lu, R., Zhu, H., Shao, J., and Lin, X.: FSSR: Fine-grained ehrs sharing via similarity-based recommendation in cloud-assisted ehealthcare system. In: Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, AsiaCCS 2016, Xi’an, China, May 30 - June 3, 2016, pp. 95–106, 2016
Jiang, R., Lu, R., and Choo, K.R., Achieving high performance and privacy-preserving query over encrypted multidimensional big metering data. Futur. Gener. Comput. Syst. 78:392–401, 2018.
Karuppiah, M., Li, X., Das, A.K., Kumari, S., and Liu, Q., Introduction to the special section on big data and iot in e-healthcare. Comput. Electr. Eng. 65:261–264, 2018.
Paillier, P.: Public-key cryptosystems based on composite degree residuosity classes. In: Advances in Cryptology - EUROCRYPT ’99, International Conference on the Theory and Application of Cryptographic Techniques, pp. 223–238, 1999
Qi, Y., and Atallah, M.J.: Efficient privacy-preserving k-nearest neighbor search. In: 28th IEEE International Conference on Distributed Computing Systems, pp. 311–319, 2008
Shaneck, M., Kim, Y., and Kumar, V.: Privacy preserving nearest neighbor search. In: Workshops Proceedings of the 6th IEEE International Conference on Data Mining, pp. 541–545, 2006
Wong, W.K., Cheung, D.W., Kao, B., and Mamoulis, N.: Secure knn computation on encrypted databases. In: Proceedings of the ACM SIGMOD International Conference on Management of Data, pp. 139–152, 2009
Xu, R., Morozov, K., Yang, Y., Zhou, J., and Takagi, T., Efficient outsourcing of secure k-nearest neighbour query over encrypted database. Comput. Secur. 69:65–83, 2017.
Yang, X., Lu, R., Choo, K.K.R., Yin, F., and Tang, X.: Achieving efficient and privacy-preserving cross-domain big data deduplication in cloud. IEEE Transactions on Big Data, 2017
Yao, B., Li, F., and Xiao, X.: Secure nearest neighbor revisited. In: 29th IEEE International Conference on Data Engineering, pp. 733–744, 2013
Yekta, N.I., and Lu, R.: Xrquery: Achieving communication-efficient privacy-preserving query for fog-enhanced iot. In: 2018 IEEE International conference on communications, ICC 2018, Kansas city, May 20-24, 2018, pp. 1–6, 2018
Zheng, Y., and Lu, R.: An efficient and privacy-preserving k-nn query scheme for ehealthcare data. In: 2018 IEEE Conference on green computing and communications, pp. 358–365, 2018
Zhu, Y., Xu, R., and Takagi, T.: Secure k-nn computation on encrypted cloud data without sharing key with query users. In: Proceedings of the 2013 International Workshop on Security in Cloud Computing, pp. 55–60, 2013
Funding
This research was supported in part by NSERC Discovery Grants (04009), NBIf Start-Up Grant (Rif 2017-012), HMF2017 YS-04, LMCRF-S-2018-03, ZJNSF under Grant LZ18F020003 and NSFC under Grants 61472364.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interests
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Zheng, Y., Lu, R. & Shao, J. Achieving Efficient and Privacy-Preserving k-NN Query for Outsourced eHealthcare Data. J Med Syst 43, 123 (2019). https://doi.org/10.1007/s10916-019-1229-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-019-1229-1