Abstract
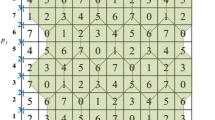
Data hiding research has focused mainly on determining how to embed secret data into various public host media, and to also ensure the host medium is not changed to a degree such that it can be perceived by the human eye. In 2014, Chang et al. proposed a novel concept, named the turtle shell matrix, to embed secret data. This scheme has obvious advantages with respect to its hiding capacity and image quality. However, its disadvantage is lack of flexibility due to the fixed turtle shell matrix structure. In this paper, we extend this turtle shell matrix structure into a different matrix model to meet different hiding capacity and image quality needs. Meanwhile, a general extraction function is derived to generate a matrix having a different turtle shell model. The values of the pixel pairs in the cover image are modified according to guidance provided by the turtle shell to hide a secret digit in an N-ary notational system. The experimental results show that the proposed scheme not only has better flexibility in balancing the trade-off between hiding capacity and stego-image quality, but also provides higher hiding capacity and stego-images with better visual quality than previous schemes.







Similar content being viewed by others
References
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(3):469–474
Chang CC, Chou YC, Kieu TD (2008) An information hiding scheme using Sudoku. Processing the Internation Conference on Innovative Computing Information and Control, 17–22
Chang CC, Liu YJ, Nguyen TS (2014) A Novel Turtle Shell Based Scheme for Data Hiding. Processing of Internation Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIH-MSP), 89–93
Fridrich J, Goljan M, Du R (2001) Reliable detection of LSB steganography in color and grayscale images. Processing of the Internation Conference on Multimedia and Security: new challenges, ACM, 27–30
Hajizadeh H, Ayatollahi A, Mirzakuchaki S (2013) A new high capacity and EMD-based image steganography scheme in spatial domain. Processing the Internation Conference on Electrical Engineering (ICEE), 1–6
Joo JC, Lee HK, Lee HY (2010) Improved steganographic method preserving pixel-value differencing histogram with modulus function. EURASIP J Adv Signal Process 2010:26
Kaur B, Kaur A, Singh J (2011) Steganographic approach for hiding image in DCT domain. Int J Adv Eng Technol 1(3):72–78
Kieu TD, Chang CC (2011) A steganographic scheme by fully exploiting modification directions. Expert Syst Appl 38(8):10648–10657
Kim HJ, Kim C, Choi Y, Wang S, Zhang X (2010) Improved modification direction methods. Comput Math Appl 60(2):319–325
Lee CF, Chen HL (2010) A novel data hiding scheme based on modulus function. J Syst Softw 83(5):832–843
Lee CF, Wang YR, Chang CC (2007) A steganographic method with high embedding capacity by improving exploiting modification direction. Process Int Conf Intell Inf Hiding Multimed Signal Process 1:497–500
Lin CC, Shiu PF (2010) High capacity data hiding scheme for DCT-based images. J Inf Hiding Multimed Signal Process 1(3):220–240
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited. IEEE Trans Inf Forensic Secur 5(2):201–214
Makbol NM, Khoo BE (2013) Robust blind image watermarking scheme based on redundant discrete wavelet transform and singular value decomposition. AEU-Int J Electron Commun 67(2):102–112
Mielikainen J (2006) LSB matching revisited. IEEE Signal Proc Lett 13(5):285–287
Panigrahi BK, Reddy PS (2014) High quality high capacity robust DWT based steganography. Int J Innov Res Dev 3(5)
Sharma VK, Shrivastava V (2012) A steganography algorithm for hiding image in image by improved LSB substitution by minimize detection. J Theor Appl Inf Technol 36(1):1–8
Shen SY, Huang LH (2015) A data hiding scheme using pixel value differencing and improving exploiting modification directions. Comput Secur 48:131–141
Thien CC, Lin JC (2003) A simple and high-hiding capacity method for hiding digit-by-digit data in images based on modulus function. Pattern Recogn 36(12):2875–2881
Wang SJ (2005) Steganography of capacity required using modulo operator for embedding secret image. Appl Math Comput 164(1):99–116
Wang J, Sun Y, Xu H et al (2010) An improved section-wise exploiting modification direction method. Signal Process 90(11):2954–2964
Wang CM, Wu NI, Tsai CS, Hwang MS (2008) A high quality steganographic method with pixel-value differencing and modulus function. J Syst Softw 81(1):150–158
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recogn Lett 24(9):1613–1626
Yang CH, Weng CY, Wang SJ, Sun HM (2008) Adaptive data hiding in edge areas of images with spatial LSB domain systems. IEEE Trans Inf Forensic Secur 3(3):488–497
Zhang X, Wang S (2004) Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security. Pattern Recogn Lett 25(3):331–339
Zhang X, Wang S (2006) Efficient steganographic embedding by exploiting modification direction. Commun Lett, IEEE 10(11):781–783
Acknowledgements
This work was supported in part by The National Natural Science Foundation of China (No.61540009, No.61272262).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, L., Chang, CC. & Wang, A. Data hiding based on extended turtle shell matrix construction method. Multimed Tools Appl 76, 12233–12250 (2017). https://doi.org/10.1007/s11042-016-3624-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3624-7