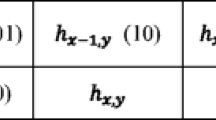Abstract
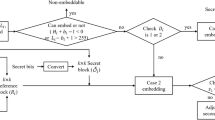
Analyzing multimedia data in mobile devices is often constrained by limited computing capacity and power storage. Therefore, more and more studies are trying to investigate methods with algorithm efficiency. Sun et al. proposed a low computing cost reversible data hiding method for absolute moment block truncation coding (AMBTC) images with excellent embedding performance. Their method predicts quantization values and uses encrypted data bits, division information, and prediction errors to construct the stego codes. This method successfully embeds data while providing a comparable bit-rate; however, it does not fully exploit the correlation of neighboring pixels and division of prediction error for better embedment. Therefore, the payload and bit-rate are penalized because the embedding performance directly depends on the prediction accuracy and division efficiency. In this paper, we use median edge detection predictor to better predict the quantization values. We also employ an alternative prediction technique to increase the prediction accuracy by narrowing the range of prediction values. Besides, an efficient centralized error diversion technique is proposed to further decrease the bit-rate. The experimental results show that the proposed method offers 8 % higher payload with 5 % lower bit-rate on average if compared to Sun et al.’s method and has better embedding performance than prior related works.










Similar content being viewed by others
References
Chang CC, Chen TS, Chung LZ (2002) A steganographic method based upon JPEG and quantization table modification. Inform Sci 141(1-2):123–128
Chang CC, Kieu TD, Wu WC (2009) A lossless data embedding technique by joint neighboring coding. Pattern Recogn 42(7):1597–1630
Chen J, Hong W, Chen TS, Shiu CW (2010) Steganography for BTC compressed images using no distortion technique. Imag Sci J 58(4):177–185
Chen B, Shu H, Coatrieux G, Chen SX, Coatrieux JL (2015) Color image analysis by quaternion-type moments. J Math Imag Vision 51(1):124–144
Delp EJ, Mitchell OR (1979) Image compression using block truncation coding. IEEE Trans Commun 27(9):1335–1342
Fu Z, Sun X, Liu Q, Zhou L, Shu J (2015) Achieving efficient cloud search services: multi-keyword ranked search over encrypted cloud data supporting parallel computing. IEICE Trans Commun E98-B(1):190–200
Gu B, Sheng VS, Tay KY, Romano W, Li S (2015) Incremental support vector learning for ordinal regression. IEEE Trans Neural Netw Learn Syst 26(7):1403–1416
Gu B, Sheng VS, Wang Z, Ho D, Osman S, Li S (2015) Incremental learning for v-support vector regression. Neural Netw 67:140–150
Guo P, Wang J, Xue HG, Chang SK, Kim JU (2014) A variable threshold-value authentication architecture for wireless mesh networks. J Internet Technol 15(6):929–936
Hong W (2013) Adaptive image data hiding in edges using patched reference table and pair-wise embedding technique. Inform Sci 221(1):473–489
Hong W, Chen TS (2012) A novel data embedding method using adaptive pixel pair matching. IEEE Trans Inform Forensics Sec 7(1):176–184
Hong W, Chen TS, Shiu CW, Wu MC (2011) Lossless data embedding in BTC codes based on prediction and histogram shifting. Appl Mech Mater 65:182–185
Hong W, Chen TS, Chen J (2015) Reversible data hiding using Delaunay triangulation and selective embedment. Inf Sci 308(1):140–154
Hong W, Chen TS, Shiu CW (2009) Reversible data hiding for high quality images using modification of prediction errors. J Syst Software 82:1833–1842
Huang YH, Chang CC, Chen YH (2016) Hybrid secret hiding schemes based on absolute moment block truncation coding. Multimed Tools Appl. doi:10.1007/s11042-015-3208-y
Lema M, Mitchell OR (1984) Absolute moment block truncation coding and its application to color images. IEEE Trans Commun 32(10):1148–1157
Li J, Li X, Yang B, Sun X (2015) Segmentation-based image copy-move forgery detection scheme. IEEE Trans Inform Forensics Sec 10(3):507–518
Lin CC, Liu XL, Tai WL, Yuan SM (2015) A novel reversible data hiding scheme based on AMBTC compression technique. Multimed Tools Appl 74(11):3823–3842
Lou DC, Hu CH (2012) LSB steganographic method based on reversible histogram transformation function for resisting statistical steganalysis. Inf Sci 188(4):346–358
Malik A, Sikka G, Verma HK (2016) A high payload data hiding scheme based on modified AMBTC technique. Doi: 10.1007/s11042-016-3815-2
Ni ZC, Shi YQ, Ansari N, Su W (2006) Reversible data hiding. IEEE Trans Circ Syst Video Technol 16(3):354–362
Ou D, Sun W (2015) High payload image steganography with minimum distortion based on absolute moment block truncation coding. Multimed Tools Appl 74(21):9117–9139
Shen J, Tan H, Wang J, Wang J, Lee S (2015) A novel routing protocol providing good transmission reliability in underwater sensor networks. J Internet Technol 16(1):171–178
Shiu CW, Chen YC, Hong W (2015) Encrypted image-based reversible data hiding with public key cryptography from difference expansion. Signal Process Image Commun 39:226–233
Sun W, Lu ZM, Wen YC, Yu FX, Shen RJ (2013) High performance reversible data hiding for block truncation coding compressed images. SIViP 7(2):297–306
The USC-SIPI Image Database. http://sipi.usc.edu/database
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circ Syst Video Technol 13(8):890–896
Wen X, Shao L, Xue Y, Fang W (2015) A rapid learning algorithm for vehicle classification. Inf Sci 295(1):395–406
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2014) Steganalysis of LSB matching using differences between nonadjacent pixels. Multimed Tools Appl. doi:10.1007/s11042-014-2381-8
Xia Z, Wang X, Sun X, Wang B (2013) Steganalysis of least significant bit matching using multi-order differences. Security Commun Netw 7(8):1283–1291
Xia Z, Wang X, Sun X, Wang Q (2016) A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans Parallel Distrib Syst 27(2):340–352
Yuan C, Sun X, Rui L (2016) Fingerprint liveness detection based on multi-scale LPQ and PCA. Chin Commun 13(7):60–65
Zhang Y, Guo SZ, Lu ZM, Luo H (2013) Reversible data hiding for BTC-compressed images based on lossless coding of mean tables. IEICE Trans Commun E96.B(2):624–631
Zheng Y, Jeon B, Xu D, Wu QMJ, Zhang H (2015) Image segmentation by generalized hierarchical fuzzy C-means algorithm. J Intell Fuzzy Syst 28(2):961–973
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hong, W., Ma, YB., Wu, HC. et al. An efficient reversible data hiding method for AMBTC compressed images. Multimed Tools Appl 76, 5441–5460 (2017). https://doi.org/10.1007/s11042-016-4032-8
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-4032-8