Abstract
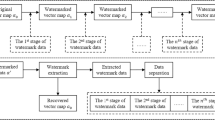
The rapid flourishing of GIS applications has made the copyright protection and content authentication of vector maps two important issues in the digital world. In this paper, a multipurpose watermarking scheme is proposed for the scenarios when the two requirements are needed simultaneously. In the scheme, robust watermark and fragile watermarks are embedded into the host map simultaneously. To avoid the interference between the two kinds of watermarks, robust watermark is embedded into the feature points of the objects in the map, while fragile watermarks are embedded into the nonfeature points. Due to the independence of the feature points and non-feature points, the robust watermark and fragile watermarks can be detected independently. After watermark detection, the robust watermark can be used for copyright protection, and the fragile watermarks can be used for tamper localization and characterization. The fragility of the proposed scheme is analyzed theoretically, and both the robustness and the fragility are verified by a set comprehensive experiments.





Similar content being viewed by others
Notes
As Mintzer and Braudaway [23] noted, robust watermark should be embedded first since fragile watermark should be sensitive to any data modification, including robust watermarking.
Feature points are the points that are most essential to represent an object and can not be arbitrarily changed. The classical Douglas-Peucker algorithm [8] is amended to use relative threshold so that the feature points can always be properly selected, even after map scaling.
References
Bazin C, Le Bars JM, Madelaine J (2007) A blind, fast and robust method for geographical data watermarking ACM symposium on information, computer and communications security (ASIACCS 07), pp 265–272
Belussi A, Catania B, Podest P (2005) Towards topological consistency and similarity of multiresolution geographical maps Proceedings of the 13th annual ACM international workshop on geographic information systems, pp 220–229
Brewer CA, Buttenfield BP (2007) Framing guidelines for multi-scale map design using databases at multiple resolutions. Cartogr Geogr Inf Sci 34(1):3–15
Celik MU, Sharma G, Saber E, Tekalp AM (2002) Hierarchical watermarking for secure image authentication with localization. IEEE Trans Image Process 11 (6):585–595
Chen BG, Wornell W (2001) Quantization index modulation: a class of provably good methods for digital watermarking and information embedding. IEEE Trans Inf Theory 47(4):1423–1443
Chen N, Zhu J (2008) Multipurpose audio watermarking algorithm. J Zhejiang Univ Sci A 9(4):517–523
Doncel VR, Nikolaidis N, Pitas I (2007) An optimal detector structure for the Fourier descriptors domain watermarking of 2D vector graphics. IEEE Trans Vis Comput Graph 13(5):851–863
Douglas DH, Peucker TK (1973) Algorithms for the reduction of the number of points required to represent a digitized line or its caricature. Canadian Cartographer 10:112–122
Gokyoz T (2005) Generalization of contours using deviation angels and error bands. Cartogr J 42(2):145–150
Gou HM, Wu M (2005) Data hiding in curves with application to fingerprinting maps. IEEE Trans Signal Process 53(10):3988–4005
Guo H, Li Y, Liu A, Jajodia S (2006) A fragile watermarking scheme for detecting malicious modifications of database relations. Inf Sci 176:1350–1378
Huang M, Zhou X, Cao JH et al Geo-WDBMS: an improved DBMS with the function of watermarking geographical data DASFAA 2007. LNCS, 4443:1098–1109
IEEE standard for binary floating-point arithmetic ANSI/IEEE Standard 754–1985
Kang H, Kim K, Choi J (2001) A vector watermarking using the generalized square mask Proceedings international symposium on information technology: coding and computing 2001, pp 234–236
Kirovski D, Malvar HS (2003) Spread spectrum watermarking of audio signals. IEEE Trans Signal Process 51(4):1020–1033
Lafaye J, Bguec J, Gross-Amblard D, Ruas A (2007) Invisible graffiti on your buildings: blind and squaring-proof watermarking of geographical databases 10th international symposium on spatial and temporal databases. Lecture notes in computer science, advances in spatial and temporal databases. LNCS 4605, pp 312–329
Langelaar GC, Lagendijk RL (2001) Optimal differential energy watermarking of DCT encoded images and video. IEEE Trans Image Process 10(1):148–158
Li YY, Xu LP (2003) A blind watermarking of vector graphics images Proceedings of fifth international conference on computational intelligence and multimedia applications (ICCIMA 2003), pp 424–429
Li J, Wang R, Yan D, Li Y (2012) A multipurpose audio aggregation watermarking based on multistage vector quantization. Multimedia Tools Appl:1–23
Lin CH, Li YC, Wu MN, Yang SS, Chen KJ (2009) Multipurpose watermarking method based on blind vector quantization. Journal of Information Hiding and Multimedia Signal Process:636–639
Lu CS, Liao HYM (2005) Multipurpose watermarking for image authentication and protection. IEEE Trans Image Process 10(10):1579–1592
Lu Z, Xu D, Sun S (2005) Multipurpose image watermarking algorithm based on multistage vector quantization. IEEE Trans Image Process 14(6):822–831
Mintzer F, Braudaway GW (1999) If one watermark is good, are more better? International Conference on Acoustics, Speech and Signal Processing, pp 2067–2070
Mobasseri BG, Sieffert MJ, Simard RJ (2000) Content authentication and tamper detection in digital video. IEEE Int Conf Image Process 1:458–461
Niu X, Shao CY, Wang X (2006) A Survey of Digital Vector Map Watermarking. Int J Innov Comput Inf Control 2(6):1301–1316
Niu XM, Shao CY, Wang XT (2007) XT. GIS watermarking: hiding data in 2D vector maps. Stud Comp Intelligence 58:123–155
Ohbuchi R, Ueda H, Endoh S Robust watermark of vector digital maps. ICME2002
Pan Z, Zhang Y, Kwong S (2015) Efficient motion and disparity estimation optimization for low complexity multiview video coding. IEEE Trans Broadcast 61 (2):166–176
Petitcolas FAP, Anderson RJ, Kuhn MG (1999) Information hiding: a survey. Proc IEEE 87(7):1062–1078
Solachidis V, Nikolaidis N, Pitas I (2000) Watermarking polygonal lines using Fourier descriptors Proc. IEEE international conference on acoustics, speech and signal processing (ICASSP 2000), pp 1955–1958
Varodayan D, Lin YC, Girod B (2008) Audio authentication based on distributed source coding IEEE International Conference on Acoustics, Speech and Signal Processing, pp 225–228
Wang N, Men C (2012) Reversible fragile watermarking for 2-D vector map authentication with localization. Comput Aided Des 44:320–330
Wang Y, Doherty JF, Van Dyck RE (2002) A wavelet-based watermarking algorithm for ownership verification of digital images. IEEE Trans Image Process 11 (2):77–88
Wang Z, Yang B, Niu X, Zhang Y (2006) A practical multipurpose watermarking scheme for visual content copyright protection and authentication IEEE international conference on intelligent information hiding and multimedia signal processing, pp 461–464
Wang CJ, Peng ZY, Peng YW, Yu L, Wang JZ, Zhao QZ (2012) Watermarking geographical data on spatial topological relations. Multimedia Tools Appl 57(1):67–89
Xia Z, Wang X, Sun X, Wang B (2014) Steganalysis of least significant bit matching using multi-order differences. Security and Commun Netw 7(8):1283–1291
Xia Z, Wang X, Sun X, Liu Q, Xiong N (2016) Steganalysis of LSB matching using differences between nonadjacent pixels. Multimedia Tools Appl 75 (4):1947–1962
Xu T, Shao X, Yang Z (2009) Multi-watermarking scheme for copyright protection and content authentication of digital audio. Adv Multimedia Inf Process:1281–1286
Yan H, Li J (2012) Blind watermarking technique for topographic map data. Appl Geomatics 4(4):225–229
Yan H, Li J, Wen H (2011) A key points-based blind watermarking approach for vector geospatial data. Comput Environ Urban Syst 35(6):485–492
Yu-Chi P, I-Chang J (2009) Blind and robust watermarking for street-network vector maps. Inf Technol J 8(7):982–989
Zhang H, Gao M (2009) A semi-fragile digital watermarking algorithm for 2D vector graphics tamper localization. IEEE International Conference on Multimedia Information Networking and Security 1:549–552
Zhao Y, Zhou Z (2012) Multipurpose blind watermarking algorithm for color image based on DWT and DCT IEEE international conference on wireless communications networking and mobile computing, pp 1–4
Zheng L, You F (2009) A fragile digital watermark used to verify the integrity of vector map IEEE International Conference on E-Business and Information System Security, pp 1–4
Zhu C, Liao X, Li Z (2006) Chaos-based multipurpose image watermarking algorithm. Wuhan Univ J Nat Sci 11(6):1675–1678
Acknowledgment
This work is supported by the National Natural Science Foundations of China under grant (No.71603252). This work is also partially supported by a project funded by the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology (CICAEET).
Author information
Authors and Affiliations
Corresponding author
Additional information
This work is supported by the National Natural Science Foundation of China under grant (No.71603252). This work is partially supported by a project funded by the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD) and Jiangsu Collaborative Innovation Center on Atmospheric Environment and Equipment Technology (CICAEET).
Rights and permissions
About this article
Cite this article
Peng, Y., Lan, H., Yue, M. et al. Multipurpose watermarking for vector map protection and authentication. Multimed Tools Appl 77, 7239–7259 (2018). https://doi.org/10.1007/s11042-017-4631-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4631-z