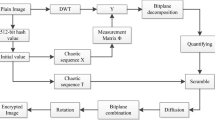
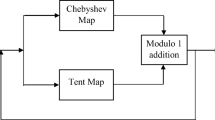
Abstract
Compressive sensing based encryption achieves simultaneous compression-encryption by utilizing a low complex sampling process, which is computationally secure. In this paper, a new novel 1D–chaotic map is proposed that is used to construct an incoherence rotated chaotic measurement matrix. The chaotic property of the proposed map is experimentally analysed. The linear measurements obtained are confused and diffused using the chaotic sequence generated using the proposed map. The chaos based measurement matrix construction results in reduced data storage and bandwidth requirements. As it needs to store only the parameters required to generate the chaotic sequence. Also, the sensitivity of the chaos to the parameters makes the data transmission secure. The secret key used in the encryption process is dependent on both the input data and the parameter used to generate the chaotic map. Hence the proposed scheme can resist chosen plaintext attack. The key space of the proposed scheme is large enough to thwart statistical attacks. Experimental results and the security analysis verifies the security and effectiveness of the proposed compression-encryption scheme.









Similar content being viewed by others
References
Banderia AS, Dobriban E, Mixon DG, Sawin WF (2012) Certifying the Restricted Isometry Property is Hard. IEEE Trans Inf Theory 59:3448–3450
Baraniuk R (2007) Compressive Sensing (lecture notes). IEEE Signal Process Mag 24(4):118–121
Belazi AAA, El-Latif BS (2016) A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process 128:155–170
Cambareri V, Mangia M, Pareschi F, Rovatti R, Setti G (2015) On known-plaintext attacks to a compressed sensing-based encryption: a quantitative analysis. IEEE Trans Inf Forensics Security 10(10):2182–2195
Cambareri V, Mangia M, Pareschi F, Rovatti R, Setti G (2015) Low-complexity multiclass encryption by compressed sensing. IEEE Trans Signal Process 63(9):2183–2195
Candes EJ (2008) The restricted isometry property and its implications for compressed sensing. C R Math 346(9–10):589–592
Cui J, Liu Y, Xu Y, Zhao H, Zha H (2013) Tracking generic human motion via fusion of low-and high-dimensional approaches. IEEE Trans Syst Man Cybern 43(4):996–1002
Deepak M, Ashwin V, Amutha R (2014) A new Multistage multiple image encryption using a combination of Chaotic Block Cipher and Iterative Fractional Fourier Transform. In First International Conference on Networks & Soft Computing (ICNSC2014):360–364
Donoho DL (2006) Compressed Sensing. IEEE Trans Inf Theory 52:1289–1306
Fay R (2016) Introducing the counter mode of operation to Compressed Sensing based encryption. Inform Process Lett 16(4):279–283
Gordon WB (1996) Period three trajectories of the logistic map. Math Mag 69(2):118–120
Hanis S, Amutha R (2017) Double image compression and encryption scheme using logistic mapped convolution and cellular automata. Multimed Tools Appl :1-16
Hu G, Xiao D, Wang Y, Xiang T (2017) An image coding scheme using parallel compressive sensing for simultaneous compression-encryption applications. J Vis Commun Image R 44:116–127
Hua Z, Zhou Y, Pun CM, Chen CP (2015) 2D Sine Logistic modulation map for image encryption. Inform Sciences 297:80–94
Huang R, Sakurai K (2011) A robust and compression-combined digital image encryption method based on compressive sensing. In Proc Intelligent Information Hiding and Multimedia Signal Processing IIH-MSP, 105–108
Huang R, Rhee KH, Uchida S (2014) A parallel image encryption method based on compressive sensing. Multimed Tools Appl 72(1):71–93
Jiang J, He X, Gao M, Wang X, Wu X (2015) Human action recognition via compressive-sensing-based dimensionality reduction. Optik-Int J Light Electron Optics 126(9):882–887
Liao X, Shu C (2015) Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J Vis Commun Image R 28:21–27
Liao X, Li K, Yin J (2017) Separable data hiding in encrypted image based on compressive sensing and discrete Fourier transform. Multimed Tools Appl 76(20):20739–20753
Liao X, Qin Z, Ding L (2017) Data embedding in digital images using critical functions. Signal Proces-Image 58:146–156
Liu E, Temlyakov VN (2012) The orthogonal super greedy algorithm and application in compressed sensing. IEEE Trans Inf Theory 58:2040–2047
Liu Y, Zhang X, Cui J, Wu C, Aghajan H, Zha H (2010) Visual analysis of child-adult interactive behaviors in video sequences. In Proc of IEEE Int Conf Virtual Systems and Multimedia (VSMM) :26–33
Liu Y, Cui J, Zhao H, Zha H (2012) Fusion of low-and high-dimensional approaches by trackers sampling for generic human motion tracking. In Proc of IEEE Int Conf Patt Recog (ICPR) :898–901
Liu Y, Nie L, Han L, Zhang L, Rosenblum DS (2015) Action2Activity: Recognizing Complex Activities from Sensor Data. In Proc of Int Joint Conf Artif (IJCAI) :1617–1623
Liu Y, Zhang L, Nie L, Yan Y, Rosenblum DS (2016) Fortune Teller: Predicting Your Career Path. In Proc of AAAI :201-207
Liu L, Cheng L, Liu Y, Jia Y, Rosenblum DS (2016) Recognizing Complex Activities by a Probabilistic Interval-Based Model. In Proc of AAAI 30:1266–1272
Liu Y, Zheng Y, Liang Y, Liu S, Rosenblum DS (2016) Urban water quality prediction based on multi-task multi-view learning. In Proc of Int Joint Conf Artif (IJCAI) :2576–2582
Liu Y, Nie L, Liu L, Rosenblum DS (2016) From action to activity: Sensor-based activity recognition. Neurocomputing 12(181):108–115
Niyat AY, Moattar MH, Torshiz MN (2017) Color image encryption based on hybrid hyper-chaotic system and cellular automata. Opt Laser Eng 90:225–237
Orsdemir A, Altun HO, Sharma G, Bocko MF (2008) On the security and robustness of encryption via compressed sensing. In IEEE Milit Commun C (MILCOM 2008) San Diego, CA :1-7
Phamila AVY, Amutha R (2013) Low complexity energy efficient very low bit-rate image compression scheme for wireless sensor network. Inform Process Lett 113(18):672–676
Phamila AVY, Amutha R (2015) Energy-efficient low bit rate image compression in wavelet domain for wireless image sensor networks. Electron Lett 51(11):824–826
Preoţiuc-Pietro D, Liu Y, Hopkins D, Ungar L (2017) Beyond binary labels: political ideology prediction of Twitter users. In Proc of the 55th Annual Meeting of the Association for. Computational Linguistics 1:729–740
Rachlin Y, Baron D (2008) The secrecy of compressed sensing measurements. In Proc 46th Annual Allerton Conf. Comm. Control Comput :813-817
Tong XJ, Wang Z, Zhang M, Liu Y (2013) A new algorithm of the combination of image compression and encryption technology based on cross chaotic map. Nonlinear Dynam 72(1–2):229–241
Wu X, Wang D, Kurths J, Kan H (2016) A novel lossless color image encryption scheme using 2D DWT and 6D hyperchaotic system. Inform Sciences 349:137–153
Yao S, Wang T, Shen W, Shaoming P, Chong Y (2017) Research of incoherence rotated chaotic measurement matrix in compressed sensing. Multimed Tools Appl 76(17):17699–17717
Yu L, Barbot JP, Zheng G, Sun H (2010) Compressive sensing with chaotic sequence. IEEE Signal Process Lett 17(8):731–734
Yuan X, Wang X, Wang C, Weng J, Ren K (2016) Enabling secure and fast indexing for privacy-assured healthcare monitoring via compressive sensing. IEEE Trans Multimedia 18(10):2002–2014
Yuen CH, Wong KW (2011) A chaos-based joint image compression and encryption scheme using DCT and SHA-1. Appl Soft Comput 11(8):5092–5098
Zhang LY, Wong KW, Zhang Y, Zhou J (2016) Bi-level protected compressive sampling. IEEE Trans Multimedia 18(9):1720–1732
Zhang W, Yu H, Zhao YL, Zhu ZL (2016) Image encryption based on three-dimensional bit matrix permutation. Signal Process 118:36–50
Zhang Y, Zhang LY, Zhou J, Liu L, Chen F, He X (2016) A review of compressive sensing in information security field. IEEE Access 4:2507–2519
Zhou NR, Zhang AD, Zheng F, Gong LH (2014) Novel image compression–encryption hybrid algorithm based on key-controlled measurement matrix in compressive sensing. Opt Laser Technol 62:152–160
Zhou N, Zhang A, Wu J, Pei D, Yang Y (2014) Novel hybrid image compression–encryption algorithm based on compressive sensing. Optik-International Journal for Light and Electron Optics 125(18):5075–5080
Zhou Y, Bao L, Chen CP (2014) A new 1D chaotic system for image encryption. Signal Process 97:172–182
Zhou Y, Hua Z, Pun CM, Chen CP (2015) Cascade chaotic system with applications. IEEE Trans Cybern 45(9):2001–2012
Zhu H, Zhao C, Zhang X (2013) A novel image encryption–compression scheme using hyper-chaos and Chinese remainder theorem. Signal Process-Image 28(6):670–680
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ponuma, R., Amutha, R. Compressive sensing based image compression-encryption using Novel 1D-Chaotic map. Multimed Tools Appl 77, 19209–19234 (2018). https://doi.org/10.1007/s11042-017-5378-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-5378-2