Abstract
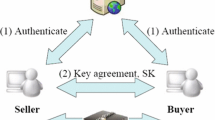
With the aim of guaranteeing secure communication through public networks, three-factor password authentication (TF-PWA) scheme plays a key role in many internet applications. Since in TF-PWA scheme, the communicating entities can mutually authenticate each other and generate a shared session key, which will be used for secure exchange of messages in succeeding communication among them. As a result, the TF-PWA schemes gain enormous consideration in recent years. More recently, due to light-weight features of the extended chaotic map, it is also extensively applied in designing of public key encryption, key agreement, image encryption, S-box, hash function, digital signature, password authentication, etc. The aim of this paper was to design a dynamic identity-based three-factor password authentication scheme using extended chaotic map (ECM-TF-PWA) in the random oracle model. The proposed scheme is provably secure based on the intractability assumption of chaotic map-based Diffie–Hellman problem. The informal security analysis gives the evidence that our scheme protects all attacks and provides functionality attributes that are needed in a three-factor authentication system. Besides, the performance discussion shows that our scheme performs better than others in respect of computation and communication cost.









Similar content being viewed by others
References
He, D., Chen, Y., Chen, J.: Cryptanalysis and improvement of an extended chaotic maps-based key agreement protocol. Nonlinear Dynamics 69, 1149–1157 (2012)
He, D., Chen, J., Zhang, R.: A more secure authentication scheme for telecare medicine information systems. Journal of Medical Systems (2010). doi:10.1007/s10916-011-9658-5
Islam, S. H., Bisws, G. P.: Improved remote login scheme based on ECC. In: Proceedings of the International Conference on Recent Trends in Information Technology, pp. 1221–1226 (2011)
Islam, S.H., Bisws, G.P.: Comments on ID-based client authentication with key agreement protocol on ECC for mobile client-server environment. In: Proceedings of the International Conference on Advanced in Computing and Communications, CCIS, Springer-Verlag, Part II, vol. 191, pp. 628–635 (2011)
Islam, S.H., Bisws, G.P.: An improved ID-based client authentication with key agreement scheme on ECC for mobile client-server environments. Theoretical and Applied Informatics 24(4), 293–312 (2012)
Li, C.-T., Hwang, M.-S.: An efficient biometrics-based remote user authentication scheme using smart cards. Journal of Networkcand Computer Applications 33, 1–5 (2010)
Das, A.K.: Cryptanalysis and further improvement of a biometric-based remote user authentication scheme using smartcards. International Journal of Network Security & Its Applications 3(2), 13–28 (2011)
Das, A.K.: Analysis and improvement on an efficient biometric-based remote user authentication scheme using smart cards. IET Information Security 5(3), 145–151 (2012)
Lee, J.K., Ryu, S.R., Yoo, K.Y.: Fingerprint-based remote user authentication scheme using smart cards. Electronics Letter 38, 554–555 (2002)
Lin, C.H., Lai, Y.Y.C.H.: A flexible biometrics remote user authentication scheme. Computer Standards and Interfaces 27, 19–23 (2004)
Khan, M.K., Zhang, J.S.: Improving the security of ‘a flexible biometrics remote user authentication scheme’. Computer Standards and Interfaces 29, 82–85 (2007)
Fan, C.I., Lin, Y.H.: Provably secure remote truly three-factor authentication scheme with privacy protection on biometrics. IEEE Transaction on Information Forensics and Security 4, 933–945 (2009)
Li, X., Niu, J.W., Ma, J., Wang, W.D., Liu, C.L.: Cryptanalysis and improvement of a biometric-based remote authentication scheme using smart cards. Journal of Network and Computer Application 34, 73–79 (2011)
An, Y.: Security Analysis and Enhancements of an Effective Biometric-Based Remote User Authentication Scheme Using Smart Cards. Journal of Biomedicine and Biotechnology (2012). doi:10.1155/2012/519723
Li, X., Niu, J., Khan, M. K., Liao. J.: Robust biometrics based three-factor remote user authentication scheme with key agreement. In: Proceedings of the International Symposium on Biometrics and Security Technologies, pp. 105–110 (2013)
Hsieh, B-T., Yeh, H-Y., Sun, H-M., Lin, C-T.: Cryptanalysis of a fingerprint-based remote user authentication scheme using smart cards. In: Proceedings of 37th IEEE conference on security technology, pp. 349–350 (2003)
Lin, C.-H., Lai, Y.-Y.: A flexible biometrics remote user authentication scheme. Computer Standards and Interfaces 27(1), 19–23 (2004)
Lee, C.-C., Hsu, C.-W.: A secure biometric-based remote user authentication with key agreement scheme using extended chaotic maps. Nonlinear Dynamics 71, 201–211 (2013)
Yeh, H.-L., Chen, T.-H., Hu, K.-J., Shih, W.-K.: Robust elliptic curve cryptography-based three factor user authentication providing privacy of biometric data. IET Information Security (2013). doi:10.1049/iet-ifs.2011.0348
Zhang, L.H.: Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons and Fractals 37, 669–74 (2008)
Wang, K., Pei, W., Zhou, L., Cheung, Y., He, Z.: Security of public key encryption technique based on multiple chaotic system. Physics Letters A 360, 259–262 (2006)
Xiao, D., Liao, X.F., Deng, S.J.: A novel key agreement protocol based on chaotic maps. Inform Sciences 177, 1136–1142 (2007)
Xiao, D., Liao, X.F., Deng, S.J.: Using time-stamp to improve the security of a chaotic maps-based key agreement protocol. Inform Sciences 178, 1598–1602 (2008)
Wang, X.Y., Zhao, J.F.: An improved key agreement protocol based on chaos. Communications in Nonlinear Science and Numerical Simulation 15, 4052–4057 (2010)
Guo, X.F., Zhang, J.S.: Secure group key agreement protocol based on chaotic hash. Inform Sciences 180, 4069–4074 (2010)
Niu, Y.J., Wang, X.Y.: An anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation 16, 1986–1992 (2011)
Xie, Q., Tu, X.: Chaotic maps-based three-party password-authenticated key agreement scheme. Nonlinear Dynamics 74, 1021–1027 (2013)
Zhao, F., Gong, P., Li, S., Li, M., Li, P.: Cryptanalysis and improvement of a three-party key agreement protocol using enhanced Chebyshev polynomials. Nonlinear Dynamics 74, 419–427 (2013)
Lee, C.-C., Li, C.-T., Hsu, C.-W.: A three-party password-based authenticated key exchange protocol with user anonymity using extended chaotic maps. Nonlinear Dynamics 73, 125–132 (2013)
Farash, M.S., Attari, M.A.: An efficient and provably secure three-partypassword-based authenticated key exchange protocol based on Chebyshev chaotic maps. Nonlinear Dynamics (2014). doi:10.1007/s11071-014-1304-6
Farash, M.S., Attari, A.: Cryptanalysis and improvement of a chaotic map-based key agreement protocol using Chebyshev sequence membership testing. Nonlinear Dynamics (2014). doi:10.1007/s11071-013-1204-1
Chen, G., Mao, Y., Chui, C.: A symmetric image encryption scheme based on 3D chaotic cat maps. Chaos, Solitons and Fractals 21(3), 749–761 (2004)
Wang, X., Yang, L., Liu, R.: A chaotic image encryption algorithm based on perceptron model. Nonlinear Dynamics 62, 615–621 (2010)
Wang, X., Wang, X., Zhao, J.: Chaotic encryption algorithm based on alternant of stream cipher and block cipher. Nonlinear Dynamics 63, 587–597 (2011)
Chen, G., Chen, Y., Liao, X.: An extended method for obtaining S-boxes based on three-dimensional chaotic baker maps. Chaos, Solitons and Fractals 31(3), 571–579 (2007)
Wang, Y., Wong, K., Liao, X., Xiang, T.: A block cipher with dynamic S-boxes based on tent map. Communications in Nonlinear Science and Numerical Simulation 14(7), 3089–3099 (2009)
Jye, S.: A speech encryption using fractional chaotic systems. Nonlinear Dynamics 65, 103–108 (2011)
Deng, S., Li, Y., Xiao, D.: Analysis and improvement of a chaos-based Hash function construction. Communications in Nonlinear Science and Numerical Simulation 15(5), 1338–1347 (2010)
Xiao, D., Liao, X., Deng, S.: One-way hash function construction based on the chaotic map with changeable parameter. Chaos, Solitons and Fractals 24(1), 65–71 (2005)
Xiao, D., Shih, F., Liao, X.: A chaos-based hash function with both modification detection and localization capabilities. Communications in Nonlinear Science and Numerical Simulation 15(9), 2254–2261 (2010)
Chain, K., Kuo, W.-C.: A new digital signature scheme based on chaotic maps. Nonlinear Dynamics 74, 1003–1012 (2013)
Lee, C.-C., Chen, C.-C., Wu, C.Y., Huang, S.-Y.: An extended chaotic maps-based key agreement protocol with user anonymity. Nonlinear Dynamics 69, 79–87 (2012)
Xue, K., Hong, P.: Security improvement on an anonymous key agreement protocol based on chaotic maps. Communications in Nonlinear Science and Numerical Simulation 17, 2969–2977 (2012)
Tan, Z.: A chaotic maps-based authenticated key agreement protocol with strong anonymity. Nonlinear Dynamics 72, 311–320 (2013)
Li, C.-T., Lee, C.-C., Weng, C.-Y.: An extended chaotic maps based user authentication and privacy preserving scheme against DoS attacks in pervasive and ubiquitous computing environments. Nonlinear Dynamics 74, 1133–1143 (2013)
Guo, Cheng, Chang, C.-C.: Chaotic maps-based password-authenticated key agreement using smart cards. Communications in Nonlinear Science and Numerical Simulation 18, 1433–1440 (2013)
Lee, C.-C., Lou, D.-C., Li, C.-T.: An extended chaotic-maps-based protocol with key agreement for multiserver environments. Nonlinear Dynamics (2013). doi:10.1007/s11071-013-1174-3
Khan, M.K., Zhang, J., Wang, X.: Chaotic hash-based fingerprint biometric remote user authentication scheme on mobile devices. Chaos, Solitons and Fractals 35, 519–524 (2008)
Bergamo, P., Arco, P., Santis, A., Kocarev, L.: Security of public key cryptosystems based on Chebyshev polynomials. IEEE Transaction on Circuits and Systems-I 52, 1382–1393 (2005)
Zhang, L.: Cryptanalysis of the public key encryption based on multiple chaotic systems. Chaos, Solitons and Fractals 37(3), 669–674 (2008)
Ballare, M., Rogaway, P.: Random Oracles Are Practical: A Paradigm for Designing Efficient Protocols. In: Proceedings of the 1st ACM Conference on Computer and Communications Security (CCS’93), pp. 62–73 (1993)
Shoup, V.: Sequences of Games: A Tool for Taming Complexity in Security Proofs (2004). Cryptology ePrint Archieve, Report 2004/332. http://eprint.iacr.org/2004/332
Xu, J., Zhu, W.T., Feng, D.G.: An improved smart card based password authentication scheme with provable security. Computer Standards and Interfaces 31(4), 723–728 (2009)
Dolev, D., Yao, A.: On the security of public key protocols. IEEE Transactions on Information Theory 29(2), 198–208 (1983)
Kocher, P., Jaffe, J., Jun, B.: Differential power analysis. In: Proceedings of Advances in Cryptology (Crypto’99), LNCS, pp, 388–397 (1999)
Messerges, T.S., Dabbish, E.A., Sloan, R.H.: Examining smart-card security under the threat of power analysis attacks. IEEE Transactions on Computers 51(5), 541–552 (2002)
Joye, M., Olivier, F.: Side-channel analysis, Encyclopedia of Cryptography and Security. Kluwer Academic Publishers, pp. 571–576 (2005)
Inuma, M., Otsuka, A., Imai, H.: Theoretical framework for constructing matching algorithms in biometric authentication systems. In: Proceedings of ICB’09. LNCS, vol. 5558, pp. 806–815. Springer, Berlin (2009)
Islam, S.H., Biswas, G.P.: A more efficient and secure ID-based remote mutual authentication with key agreement scheme for mobile devices on elliptic curve cryptosystem. Journal of Systems and Software 84(11), 1892–1898 (2011)
Islam, S.H., Biswas, G.P.: Design of improved password authentication and update scheme based on elliptic curve cryptography. Mathematical and Computer Modelling 57(11–12), 2703–2717 (2013)
Das, A.K., Goswami, A.: An Improved and Effective Secure Password-Based Authentication and Key Agreement Scheme Using Smart Cards for the Telecare Medicine Information System. Journal of Medical Systems 37(3), 1–16 (2013)
Das, A.K., Bruhadeshwar, B.: An Improved and Effective Secure Password-Based Authentication and Key Agreement Scheme Using Smart Cards for the Telecare Medicine Information System. Journal of Medical Systems 37(5), 1–17 (2013)
Blake-Wilson, S., Johnson, D., Menezes, A.: Key agreement protocols and their security analysis. In: Proceedings of Sixth IMA International Conference on Cryptography and Coding, Cirencester, pp. 30–45 (1997)
Acknowledgments
The author would like to thank Editor-in-Chief, Associate Editor and anonymous reviewers for their constructive comments and suggestions that help to improve the quality and presentation of the work.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Islam, S.H. Provably secure dynamic identity-based three-factor password authentication scheme using extended chaotic maps. Nonlinear Dyn 78, 2261–2276 (2014). https://doi.org/10.1007/s11071-014-1584-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-014-1584-x