Abstract
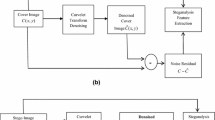
An ideal steganographic technique embeds secret information into a carrier cover object with virtually imperceptible modification of the cover object. Steganalysis is a technique to discover the presence of hidden embedded information in a given object. Each steganalysis method is composed of feature extraction and feature classification components. Using features that are more sensitive to information hiding yields higher success in steganalysis. So far, several steganalysis methods have been presented which extract some features from DCT or wavelet coefficients of images. Multi-scale and time-frequency localization of an image is offered by wavelets. However, wavelets are not effective in representing the images in different directions. Contourlet transform addresses this problem by providing two additional properties, directionality and anisotropy. The present paper offers an universal approach to steganalysis called CBS, which uses statistical moments of contourlet coefficients as features for analysis. After feature extraction, a non-linear SVM classifier is applied to classify cover and stego images. The efficiency of the proposed method is demonstrated by experimental investigations. The proposed steganalysis method is compared with two well-known steganalyzers against typical steganography methods. The results showed the superior performance of our method.




Similar content being viewed by others
References
Xuan, G., Shi, Y., Gao, J., & Zou, D. (2005). Steganalysis based on multiple features formed by statistical moments of Wavelet characteristic functions. In Proc. of International Workshop on Information Hiding, pp. 262–277.
Lyu, S., & Farid, H. (2002). Detecting hidden messages using higher-order statistics and support vector machines. In Proc. of 5th International Workshop on Information Hiding.
Farid, H., & Lyu, S. (2006). Steganalysis using higher-order image statistics. IEEE Transactions on Information Forensics and Security, 1(1), 111–119.
Kharrazi, M., Sencar, H. T., & Memon, N. (2006). Performance study of common image steganography and steganalysis techniques. Journal of Electronic Imaging, 15(4), 041104–041116.
Fridrich, J. (2004). Feature-based steganalysis for JPEG images and its implications for future design of steganographic schemes. In Proc. of 6th International Workshop on Information Hiding.
Raghavendra, B. S., & Subbanna Bhat, P. (2004). Contourlet based multiresolution texture segmentation using contextual Hidden Markov Models. In Proc. of International Conference on Computer and Information Technology (CIT), pp. 336–343.
Sallee, P. (2003). Model-based steganography. In Proc. of International Workshop on Digital Watermarking.
Fridrich, J., Goljan, M., & Soukal, D. (2004). Perturbed quantization steganography with wet paper codes. In Proc. of ACM Multimedia Workshop.
Solanki, K., Sarkar, A., & Manjunath, B. S. (2007). YASS: Yet another steganographic scheme that resists blind steganalysis. In Proc. of 9th International Workshop on Information Hiding.
Sajedi, H., & Jamzad, M. (2009). “ContSteg: Contourlet-based steganography method”, Wireless Sensor Network, Scientific Research Publishing (SRP) in California (US), 1(3), 163–170.
Sarkar, A., Solanki, K., & Manjunath, B. S. (2008). Further study on YASS: Steganography based on Randomized Embedding to Resist Blind Steganalysis. Proc. of SPIE—Security, Steganography, and Watermarking of Multimedia Contents.
Lu, Y., & Do, M. N. (2005). A directional extension for multidimensional wavelet transforms. IEEE Trans. Image Processing.
Baraniuk, R. G., Kingsbury, N., & Selesnick, I. W. (2005). The dual-tree complex wavelet transform—a coherent framework for multiscale signal and image processing. IEEE Signal Processing Magazine.
Do, M. N., & Vetterli, M. (2002). Contourlets: a directional multiresolution image representation. Proceedings of IEEE International Conference on Image processing, 1, 357–360.
Po, D. D.-Y., & Do, M. N. (2003). Directional multiscale modeling of images using the contourlet transform. In Proc. of IEEE Workshop on Statistical Signal Processing, pp. 262–265.
Long, Z., & Younan, N. H. (2006). Contourlet spectral histogram for texture classification. In Proc. of IEEE Southwest Symposium on Image Analysis and Interpretation, pp. 31–35.
Po, D. D.-Y., & Do, M. N. (2006). Directional multiscale modeling of images using the contourlet transform. IEEE Transactions on Image Processing, 15(6), 1610–1620.
Burges, C. J. C. (1998). A tutorial on support vector machines for pattern recognition. Data Mining and Knowledge Discovery, 2, 121–167.
Asadi, N., Jamzad, M., & Sajedi, H. (2008). Improvements of image steganalysis using boosted combinatorial classifiers and guassian highpass filtering. In Proc. of 4th International Conference on Intelligent Information Hiding and Multimedia Signal Processing (IIHMSP).
Acknowledgements
We would like to thank Iran Telecommunication Research Center for their financial support.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Sajedi, H., Jamzad, M. CBS: Contourlet-Based Steganalysis Method. J Sign Process Syst 61, 367–373 (2010). https://doi.org/10.1007/s11265-010-0460-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11265-010-0460-2