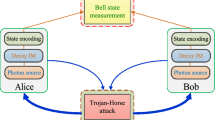
Abstract
Measurement-device-independent quantum key distribution (MDI-QKD) is aimed at removing all detector side channel attacks, while its security relies on the assumption that the encoding systems including sources are fully characterized by the two legitimate parties. By exploiting the mismatched-basis statistics in the security analysis, MDI-QKD even with uncharacterized qubits can generate secret keys. In this paper, considering the finite size effect, we study the decoy-state MDI-QKD protocol with mismatched-basis events statistics by performing full parameter optimization, and the simulation result shows that this scheme is very practical.
Similar content being viewed by others
References
Bennett C H, Brassard G. Quantum cryptography: Public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems, and Signal Processing. Bangalore, 1984. 175–179
Zhang C M, Li M, Huang J Z, et al. Fast implementation of length-adaptive privacy amplification in quantum key distribution. Chin Phys B, 2014, 23: 090310
Zhang C M, Song X T, Treeviriyanupab P, et al. Delayed error verification in quantum key distribution. Chin Sci Bull, 2014, 59: 2825–2828
Li M, Treeviriyanupab P, Zhang C M, et al. Efficient error estimation in quantum key distribution. Chin Phys B, 2015, 24: 010302
Zhao L Y, Li H W, Yin Z Q, et al. Security of biased BB84 quantum key distribution with finite resource. Chin Phys B, 2014, 23: 100304
Zhang S, Zou X, Li C, et al. A universal coherent source for quantum key distribution. Chin Sci Bull, 2009, 54: 1863–1871
Wang C Z, Guo H, Ren J G, et al. Experimental validation of dynamic polarization compensation in ground-satellite quantum key distribution. Sci China-Phys Mech Astron, 2014, 57: 1233–1237
Makarov V, Anisimov A, Skaar J. Effects of detector efficiency mismatch on security of quantum cryptosystems. Phys Rev A, 2006, 74: 022313
Qi B, Fung C H F, Lo H K, et al. Time-shift attack in practical quantum cryptosystems. Quantum Inf Comput, 2007, 7: 073–082
Fung C H F, Qi B, Tamaki K, et al. Phase-remapping attack in practical quantum-key-distribution systems. Phys Rev A, 2007, 75: 032314
Lydersen L, Wiechers C, Wittmann C, et al. Hacking commercial quantum cryptography systems by tailored bright illumination. Nat Photonics, 2010, 4: 686–689
Li H W, Wang S, Huang J Z, et al. Attacking a practical quantumkey-distribution system with wavelength-dependent beam-splitter and multiwavelength sources. Phys Rev A, 2011, 84: 062308
Jain N, Wittmann C, Lydersen L, et al. Device calibration impacts security of quantum key distribution. Phys Rev Lett, 2011, 107: 110501
Acín A, Brunner N, Gisin N, et al. Device-independent security of quantum cryptography against collective attacks. Phys Rev Lett, 2007, 98: 230501
Clauser J F, Horne M A, Shimony A, et al. Proposed experiment to test local hidden-variable theories. Phys Rev Lett, 1969, 23: 880
Braunstein S L, Pirandola S. Side-channel-free quantum key distribution. Phys Rev Lett, 2012, 108: 130502
Lo H-K, Curty M, Qi B. Measurement-device-independent quantum key distribution. Phys Rev Lett, 2012, 108: 130503
Rubenok A, Slater J A, Chan P, et al. Real-world two-photon interference and proof-of-principle quantum key distribution immune to detector attacks. Phys Rev Lett, 2013, 111: 130501
Silva T F, Vitoreti D, Xavier G B, et al. Proof-of-principle demonstration of measurement-device-independent quantum key distribution using polarization qubits. Phys Rev A, 2013, 88: 052303
Liu Y, Chen T Y, Wang L J, et al. Experimental measurement-deviceindependent quantum key distribution. Phys Rev Lett, 2013, 111: 130502
Tang Z, Liao Z, Xu F, et al. Experimental demonstration of polarization encoding measurement-device-independent quantum key distribution. Phys Rev Lett, 2014, 112: 190503
Tang Y L, Yin H L, Chen S J, et al. Measurement-device-independent quantum key distribution over 200 km. Phys Rev Lett, 2014, 113: 190501
Yin Z Q, Fung C H F, Ma X, et al. Measurement-device-independent quantum key distribution with uncharacterized qubit sources. Phys Rev A, 2013, 88: 062322
Li H W, Yin Z Q, Chen W, et al. Quantum key distribution based on quantum dimension and independent devices. Phys Rev A, 2014, 89: 032302
Zhang C M, Li M, Li H W, et al. Decoy-state measurement-deviceindependent quantum key distribution based on the Clauser-Horne-Shimony-Holt inequality. Phys Rev A, 2014, 90: 034302
Tamaki K, Curty M, Kato G, et al. Loss-tolerant quantum cryptography with imperfect sources. Phys Rev A, 2014, 90: 052314
Yin Z Q, Fung C H F, Ma X, et al. Mismatched-basis statistics enable quantum key distribution with uncharacterized qubit sources. Phys Rev A, 2014, 90: 052319
Huttner B, Imoto N, Gisin N, et al. Quantum cryptography with coherent states. Phys Rev A, 1995, 51: 1863–1869
Brassard G, Lütkenhaus N, Mor T, et al. Limitations on practical quantum cryptography. Phys Rev Lett, 2000, 85: 1330–1333
Lo H K, Ma X, Chen K. Decoy state quantum key distribution. Phys Rev Lett, 2005, 94: 230504
Ma X, Qi B, Zhao Y, et al. Practical decoy state for quantum key distribution. Phys Rev A, 2005, 72: 012326
Ma X, Fung C H F, Razavi M. Statistical fluctuation analysis for measurement-device-independent quantum key distribution. Phys Rev A, 2011, 86: 052305
Li M, Zhang C M, Yin Z Q, et al. Measurement-device-independent quantum key distribution with modified coherent state. Opt Lett, 2014, 39: 880–883
Curty M, Xu F, Cui W, et al. Finite-key analysis for measurementdevice-independent quantum key distribution. Nat Commun, 2014, 5: 3732
Ma X, Fung C H F, Boileau J C, et al. Universally composable and customizable post-processing for practical quantum key distribution. Comput & Secur, 2011, 30: 172–177
Xu F, Xu H, Lo H K. Protocol choice and parameter optimization in decoy-state measurement-device-independent quantum key distribution. Phys Rev A, 2014, 89: 052333
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Zhang, C., Li, M., Yin, Z. et al. Decoy-state measurement-device-independent quantum key distribution with mismatched-basis statistics. Sci. China Phys. Mech. Astron. 58, 590301 (2015). https://doi.org/10.1007/s11433-015-5687-2
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11433-015-5687-2