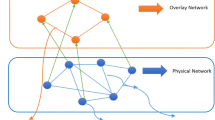
Abstract
Peer-to-Peer (P2P) technology has seen a remarkable progress due to its decentralized and distributed approach. A wide range of applications such as social networking, file sharing, long range interpersonal communication etc. are carried out with ease by employing P2P protocol candidates. There exists a huge span of such P2P protocols. In this paper, we review advanced protocols like ZeroNet, Dat, Ares Galaxy, Accordion etc. evolved from classic peer-to-peer (P2P) overlay networks. We utilize term classic to allude protocols like Chord, Pastry, Tapestry, Kademlia, BitTorrent, Gnutella, Gia, NICE etc. While coming to their design, several challenges existed with classic approach under high churn environment with growing network communication rate. To address these multifaceted network issues with classic P2P systems, novel approaches evolved which helped researchers to built new application layer networks on existing P2P networks. We contribute in this paper by systematically characterizing next-level P2P (NL P2P) and examining their key concepts. Arrangement of distributed networks is completed by numerous analysts, which incorporates classic P2P systems. In this work, we therefore aim to make a further stride by deliberately talking about protocols created from classic P2P systems, and their performance comparison in dynamically changing environment. Different aspects of P2P overlay frameworks like routing, security, query, adaptation to non-critical failure and so forth dependent on developed conventions are additionally examined. Further, based on our review and study we put forward some of the exploring challenges with NL P2P frameworks.








Similar content being viewed by others
References
Ktari S, Hecker A (2011) A peer-to-peer social network overlay for efficient information retrieval and diffusion. In: Park JJ, Yang LT, Lee C (eds) Future information technology. Communications in Computer and Information Science, vol 185. Springer, Berlin, Heidelberg
Popescu A (2005) routing in overlay networks: developments and challenges. IEEE Global Communication Letter, IEEE Communications Magazine 43(8)
Kamel M, Scoglio C, Easton T (2007) Optimal Topology Design for Overlay Networks. In: Akyildiz IF, Sivakumar R, Ekici E, Oliveira JC, McNair J (eds) Networking. Ad Hoc and Sensor Networks, Wireless Networks, Next Generation Internet. Lecture Notes in Computer Science, vol 4479. Springer, Berlin, Heidelberg
Lua EK, Crowcroft J, Pias M, Sharma R, Lim S (2005) A survey and comparison of peer-to-peer overlay network schemes. IEEE Commun Surveys Tutor 7(2):72-93. https://doi.org/10.1109/COMST.2005.1610546
Malatras A (2015) State-of-the-art survey on P2P overlay networks in pervasive computing environments. J Netw Comput Appl 55:1-23
Korzun D, and Gurtov A (2013) Flat DHT Routing Topologies. In: Korzun, Dmitry and Gurtov, Andrei (eds) Structured Peer-to-peer Systems: Fundamentals of Hierarchical Organization, Routing, Scaling and Security, pp.25-42. https://doi.org/10.1007/978-1-4614-5483-0_2
Dorrigiv R, Lopez-Ortiz A, Pralat P (2007) "Search Algorithms for Unstructured Peer-to-Peer Networks," 32nd IEEE Conference on Local Computer Networks (LCN), Dublin, pp. 343-352. https://doi.org/10.1109/LCN.2007.65
Kunzmann G (2005) “Iterative or Recursive Routing? Hybrid!,” In KIVS, Kurzbeiträge und Workshop der 14. GI/ITG- Fachtagung in Kaiserslautern, vol. P-61 of Lecture Notes in Informatics (LNI)
Cohen B (2003) Incentives build robustness in BitTorrent. Workshop on economics of PeertoPeer systems.6
Ripeanu M (2001) "Peer-to-peer architecture case study: Gnutella network," Proceedings First International Conference on Peer-to-Peer Computing, Linkoping, Sweden, pp. 99-100. https://doi.org/10.1109/P2P.2001.990433
Benet J (2014) “IPFS - content addressed, versioned, P2P file system,” CoRR, vol. abs/1407.3561, 2014. [Online]. Available: http://qrxiv.org/abs1407.3561, arXiv preprint arXiv:1407.3561
Stoica I et al (2003) Chord: a scalable peer-to-peer lookup protocol for Internet applications. IEEE ACM Trans Netw 11(1):17-32. https://doi.org/10.1109/TNET.2002.808407
Medrano-Chávez AG, Pérez-Cortés E, Lopez-Guerrero M (2015) A performance comparison of Chord and Kademlia DHTS under high churn scenarios. Peer-to-Peer Netw Appl 8:807. https://doi.org/10.1007/s12083-014-0294-y
Rowstron A, Druschel P (2001) Pastry: scalable, decentralized object location, and routing for large-scale peer-to-peer systems. In: Guerraoui R (ed) Middleware. Lecture notes in computer science, vol 2218. Springer, Berlin, Heidelberg
Maymounkov P, Mazières D (2002) Kademlia: a peer-to-peer information system based on the XOR metric. In: Druschel P, Kaashoek F, Rowstron A (eds) Peer-to-peer systems. Lecture notes in computer science, vol 2429. Springer, Berlin, Heidelberg
Ratnasamy S, Francis P, Handley M, Karp R, Shenker S (2001) A Scalable Content-Addressable Network. ACM SIGCOMM Comput Commun Rev 31. https://doi.org/10.1145/383059.383072
Urdaneta G et al (2011) A survey of DHT security techniques. ACM Comput Survey (CSUR) 43:8:1-8:49
Swamy N, Frangiadakis N, Bitsakos K (2019) A Distributed Algorithm for Constructing a Generalization of de Bruijn Graphs
Richa A, Scheideler C, Stevens P (2011) Self-stabilizing De Bruijn networks. In: Défago X, Petit F, Villain V (eds) Stabilization, safety, and security of distributed systems. SSS. Lecture notes in computer science, vol 6976. Springer, Berlin, Heidelberg
Zhang J, Su J, Wu D (2017), Poster: A Novel P2P-over-Zeronet Anonymous Communication Platform, 38th IEEE Symposium on Security and Privacy
Robinson DC, Hand JA, Madsen MB, McKelvey K (2018) The Dat project, a new approach to support data preservation through decentralization. Sci Data 5:180221. https://doi.org/10.1038/sdata.2018.221
Ogden M (2017) “Dat - Distributed Dataset Synchronization and Versioning.” OSF Preprints. January 31. https://doi.org/10.31219/osf.io/nsv2c
Pouwelse J, Garbacki P, Wang J, Bakker A, Yang J, Iosup A, Sips HJ (2007) Tribler: a social-based peer-to-peer system. Concurr Comput Pract Exp 20(2):127-138. https://doi.org/10.1002/cpe.1189
Zeilemaker N, Pouwelse JA (2012) Open source column: Tribler: P2P search, share and stream. ACM SIG Multimed Rec 4:20-24. https://doi.org/10.1145/2206765.2206767
Kolenbrander F, Le-Khac N-A, Kechadi T (2016) Forensic analysis of Ares galaxy peer-to-peer network, 11th annual adfsl conference on digital forensics, Security and Law At: Florida, USA
Labs P (2018) Filecoin: a decentralized storage network. [online]. Available: https://filecoin.io/filecoin.pdf
Techical Report (2014) Filecoin: A Cryptocurrency Operated File Network. http://filecoin.io/filecoin.pdf
Dori A (2016) “The future of Ransomware-ZeroNet protocol” threat intelligence and research
Belzarena P, Sena GG, Amigo I, Vaton S: SDN-based overlay networks for qos-aware routing. In: proceedings of the 2016 workshop on fostering Latin-American research in data communication networks, LANCOMM ‘16, pp. 19-21. ACM, New York, NY, USA. https://doi.org/10.1145/2940116.2940121
Kaashoek MF, Karger DR (2003) Koorde: a simple degree-optimal distributed hash table. In: Kaashoek MF, Stoica I (eds) Peer-to-peer systems II. IPTPS. Lecture notes in computer science, vol 2735. Springer, Berlin, Heidelberg
Furness J, Chowdhury F, Kolberg M (2013) An Evaluation of EpiChord in OverSim. 5th International Conference on Network Communication (NetCom). https://doi.org/10.1007/978-3-319-03692-2_1
Li J, Stribling J, Morris R, Frans Kaashoek M (2005). Bandwidth-efficient Management of DHT Routing Tables. Proceeding NSDI’05 Proceedings of the 2nd conference on Symposuim on Networked systems Design & Implementation -Volume 2 pp 99-114
Tian Z, Wen X, Sun Y, Zheng W, Cheng Y "Improved bamboo algorithm based on hierarchical network model," 2009 ISECS International Colloquium on Computing, Communication, Control, and Management, Sanya, pp. 297-300. https://doi.org/10.1109/CCCM.2009.5270447
Dischinger M (2004) A flexible and scalable peer-to-peer multi- cast application using bamboo. University of Karlsruhe, University of Cambridge. https://www.cl.cam.ac.uk/research/srg/netos/projects/archive/futuregrid/
Rowstron AIT, Kermarrec A-M, Castro M, Druschel P (2001) SCRIBE: The Design of a Large-Scale Event Notification Infrastructure. 2233. 30-43. Conference: Networked Group Communication Proceedings. https://doi.org/10.1007/3-540-45546-9_3
Zhang R, Hu Y (2003). Borg: A hybrid protocol for scalable application-level multicast in peer-to-peer networks. Proc Int Workshop Netw Oper Syst Support Digital Audio Video 172-179. https://doi.org/10.1145/776322.776349
Kaiqi Z, Xiumin Z. "A new approach to simulate ALMI using NS2," 2010 3rd International Conference on Advanced Computer Theory and Engineering(ICACTE), Chengdu, pp. V5-614-V5-617. https://doi.org/10.1109/ICACTE.2010.5579343
J. Chen, S. Grottke, J. Sablatnig, R. Seiler and A. Wolisz, "Scalability of a distributed virtual environment based on a structured peer-to-peer architecture," 2011 Third International Conference on Communication Systems and Networks (COMSNETS), Bangalore, 2011, pp.1-8. https://doi.org/10.1109/COMSNETS.2011.5716424
Knutsson B, Lu H, Xu W, Hopkins B (2004) "Peer-to-peer support for massively multiplayer games," IEEE INFOCOM, Hong Kong pp107 https://doi.org/10.1109/INFCOM.2004.1354485
Gai A-T, Viennot L. Broose: A Practical Distributed Hash table Based on the De-Brujin Topology. [Research Report] RR- 5238, INRIA. 2004, pp.16. <inria-00070760>
Bhagwan R, Savage S, Voelker GM (2003) Understanding Availability. In: Kaashoek MF, Stoica I (eds) Peer-to-Peer Systems II. IPTPS 2003. Lecture notes in computer science, vol 2735. Springer, Berlin, Heidelberg
Gupta A, Sahin OD, Agrawal D, ElAbbadi A (2004) Meghdoot: Content-Based Publish/Subscribe over P2P Networks. Proceedings of the 5th ACM/IFIP/USENIX International Conference on Middleware. 3231. 254-273. https://doi.org/10.1007/978-3-540-30229-2_14
Hu Y, Bhuyan L, Feng M (2012) P2P consistency support for large-scale interactive applications. Comput Netw 56:1731-1744. https://doi.org/10.1016/j.comnet.2012.01.012
Qiao Y, Bustamante FE (2006) “Structured and unstructured overlays under the microscope: a measurement-based view of two P2P systems that people use.” USENIX Annual Technical Conference, General Track
Naoumov N, Ross KW (2006) Exploiting P2P systems for DDoS attacks. International Conference on Scalable information systems (InfoScale) 47. https://doi.org/10.1145/1146847.1146894
Sampaio A, Sousa P (2018) An adaptable and ISP-friendly multicast overlay network. Peer-to-Peer Netw Appl 12:809-829. https://doi.org/10.1007/s12083-018-0680-y
Helal D, Naser A, Rehan M, El Naggar A (2014) Link-Aware Nice Application Level Multicast Protocol. Int J Comput Netw Commun Secur 6:13-27. https://doi.org/10.5121/ijcnc.2014.6302
GauthierDickey C, Lo V, Zappala D (2005) “Using n-trees for scalable event ordering in peer-to-peer games”, Proceedings of the international workshop on Network and operating systems support for digital audio and video, Stevenson, Washington, USA. https://doi.org/10.1145/1065983.1066005
Tanin E, Harwood A, Samet H (2005) "A distributed quadtree index for peer-to-peer settings," 21st international conference on data engineering (ICDE'05), Tokoyo, Japan, pp. 254-255. https://doi.org/10.1109/ICDE.2005.7
Prodan R, Iosup A (2016) Operation analysis of massively multiplayer online games on unreliable resources. Peer-to-Peer Netw Appl 9:1145. https://doi.org/10.1007/s12083-015-0383-6
Backhaus H, Krause S (2007) Voronoi-based adaptive scalable transfer revisited: gain and loss of a Voronoi-based peer-to- peer approach for MMOG. 49-54. 6th ACM SIGCOMM workshop on Network and system support for games (NetGames0, Melbourne, Australia. https://doi.org/10.1145/1326257.1326266
Backhaus H, Krause S (2010) QuON: A quad-tree-based overlay protocol for distributed Virtual Worlds. Int J Adv Media Commun 4(2):126-139. https://doi.org/10.1504/IJAMC.2010.032139
Buyukkaya E, Abdallah M, Simon G (2015) A survey of peer-to-peer overlay approaches for networked virtual environments. Peer-to-Peer Netw Appl 8:276-300. https://doi.org/10.1007/s12083-013-0231-5
Hussain A, Keshavamurthy BN (2018) A multi-dimensional routing based approach for efficient communication inside partitioned social networks. Peer-to-Peer Netw Appl 12:830-849. https://doi.org/10.1007/s12083-018-0683-8
Srivatsa M, Liu L (2004) Vulnerabilities and security threats in structured overlay networks: A quantitative analysis. In ACSAC ‘04: Proc. 20th Annual Computer Security Applications Conf., pages 252-261. IEEE Computer Society
Acknowledgements
This research work is funded by Science and Engineering Research Board (SERB), DST, under Grant (EEQ/2016/000413) for Secure and Efficient Communication Inside Partitioned Social Overlay Networks project, currently going on at National Institute of Technology Goa, Ponda, India.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Naik, A.R., Keshavamurthy, B.N. Next level peer-to-peer overlay networks under high churns: a survey. Peer-to-Peer Netw. Appl. 13, 905–931 (2020). https://doi.org/10.1007/s12083-019-00839-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-019-00839-8