Abstract
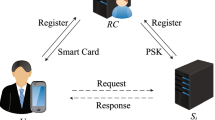
The critical system is an open control system using distributed computing method and possessing increasing levels of autonomy. Due to openness of the network, the system is vulnerable various attacks. To enhance its security, the mutual authentication among the server, the user and the registration is essential. In last several years, many biometrics-based authentication schemes for critical systems based on the client-server environment were proposed for practical applications. However, those schemes are not suitable for critical systems based on the multi-server environment. To guarantee secure communication in critical systems based on the multi-server environment, we propose a new biometrics-based authentication scheme for the multi-server environment. Security analysis and performance analysis show that the proposed scheme avoids security weaknesses in previous schemes while additional cost is small.








Similar content being viewed by others
References
Babak A, Esmael SP, Mohammad Hussein S (2014) Axiomatic agent based architecture for agile decision making in strategic information systems. J Ambient Intell Humaniz Comput 5:93–104
Cao X, Zhong S (2006) Breaking a remote user authentication scheme for multi-server architecture. IEEE Commun Lett 10:580–581
Catuogno L, Galdi C (2014) On user authentication by means of video events recognition. J Ambient Intell Humaniz Comput 5:909–918
Choi K, Toh K, Uh Y, Byun B (2012) Service-oriented architecture based on biometric using random features and incremental neural networks. Soft Comput 16:1539–1553
Guo P, Wang J, Li B, Lee S (2014) A variable threshold-value authentication architecture for wireless mesh networks. J Internet Technol 15:929–936
He D, Chen J, Hu J (2012) Improvement on a smart card based password authentication scheme. J Internet Technol 13:405–410
He D, Wang D, Wu S (2013) Cryptanalysis and improvement of a password-based remote user authentication scheme without smart cards. Inf Technol Control 42:170–177
He D, Zhang Y, Chen J (2014) Cryptanalysis and improvement of an anonymous authentication protocol for wireless access networks. Wireless Pers Commun 74:229–243
He D, Huang Y (2012) Weaknesses in a dynamic id-based remote user authentication scheme for multi-server environment. Int J Electron Secur Digit Forensics 4:43–53
Hiroaki K, Kei N, Wakaha O, Masakatsu N (2010) Privacy-preserving similarity evaluation and application to remote biometrics authentication. Soft Comput 14:529–536
Hsiang C, Shih WK (2009) Improvement of the secure dynamic id based remote user authentication scheme for multi-server environment. Comput Stand Interfaces 31:1118–1123
Juang WS (2004) Efficient multi-server password authenticated key agreement using smart cards. IEEE Trans Consum Electron 50:251–254
Ku WC, Chuang HM, Chiang MH, Chang KT (2005) Weaknesses of a multi-server password authenticated key agreement schemes. Proceedings of 2005 National Calculater Symposium, pp 1–5
Lee CC, Lin TH, Chang RX (2011) A secure dynamic id based remote user authentication scheme for multi-server environment using smart cards. Expert Syst Appl 38(11):13863–13870
Li J, Wang Q, Wang C, Ren K (2011) Enhancing attribute-based encryption with attribute hierarchy. Mobile Networks Appl 16:553–561
Li J, Huang X, Li J, Chen X, Xiang Y (2014) Securely outsourcing attribute-based encryption with checkability. IEEE Trans Parallel Distrib Syst 25:2201–2210
Liao YP, Wang SS (2009) A secure dynamic id based remote user authentication scheme for multi-server environment. Comput Stand Interfaces 31:24–29
Li J, Kim K (2010) Hidden attribute-based signatures without anonymity revocation. Inf Sci 180:1681–1689
Massimo T, Ben S (2011) Biometrics in ambient intelligence. J Ambient Intell Humaniz Comput 2:113–126
Yoon EJ, Yoo KY (2013) Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J Supercomput 63:235–255
Acknowledgments
This research was supported by the Guangzhou Zhujiang Science and Technology Future Fellow Fund under Grant No. 2012J2200094, the Guangdong Province Distinguished Young Scholars Fund of Department of Education under Grant No. Yq2013126, the Natural Science Foundation of Hubei Province of China under Grant No. 2015CFB257 and the National Natural Science Foundation of China (NSFC) under Grants Nos. 61370224 and 61472074.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shen, H., Gao, C., He, D. et al. New biometrics-based authentication scheme for multi-server environment in critical systems. J Ambient Intell Human Comput 6, 825–834 (2015). https://doi.org/10.1007/s12652-015-0305-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-015-0305-8