Abstract
Cloud Computing is an emerging paradigm that is based on the concept of distributed computing. Its definition is related to the use of computer resources which are offered as a service. As with any novel technology, Cloud Computing is subject to security threats, vulnerabilities, and attacks. Recently, the studies on security impact include the interaction of software, people and services on the Internet and that is called cyber-security or cyberspace security. In spite of various studies, we still fail to define the needs of cybersecurity management in Cloud Computing. This paper principally focuses on a comprehensive study of Cloud Computing concerns, security, cybersecurity differences, ISO, and NIST standards. It aims at identifying the policies and the guidelines included in these standards as well as it provides a comprehensive Framework proposal to manage and prevent cyber risks in Cloud Computing taking into consideration the ISO 27,032, ISO 27,001, ISO 27,017 and NIST cybersecurity Framework CSF. In addition to that, our study pinpoints at the criteria that concern measuring the maturity of organizations that implement the framework. Our objective is to provide guidance to organizations on how to establish their proper approach of cybersecurity risk management in Cloud Computing or to complement their ‘already have’ processes.









Similar content being viewed by others
References
Hayes B (2008) Cloud computing. Commun ACM 51(7):9–11
Zaharia-Rădulescu AM, Radu I (2017) Cloud computing and public administration: approaches in several European countries. Proc Int Conf Business Excellence 11(1):739–749
Al Etawi NA (2018) A comparison between cluster, grid, and cloud computing. Int J Comput Appl 179(32):37–42
Yeo CS, Buyya R, Pourreza H, Eskicioglu R, Graham P, Sommers Cluster Computing: high-performance, high-availability, and high-throughput processing on a network of computers, vol. 29(6), Springer Science+Business Media Inc., New York, USA (2006) pp. 521–551
Chellappa R (1997) Intermediaries in cloud-computing. INFORMS Meeting. Talk. Dallas, Texas
Grossman RL, Gu Y, Sabala M, Zhang W (2009) Compute and storage clouds using wide area high performance networks. Future Generation Computer Systems 25(2):179–183
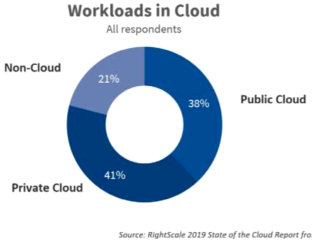
RightScale 2019 State of the cloud report from Flexera, 2019. [Online]. https://info.flexerasoftware.com/SLO-WP-State-of-the-Cloud-2019. Accessed 7 Aug 2019
Ghorbel A, Ghorbel M, Jmaiel M (2017) Privacy in cloud computing environments: a survey and research challenges. J Supercomput 73(6):2763–2800
World Economic Forum, The Global Risks Report 2019, 14th Edition, 2019. https://wef.ch/risks2019, ISBN: 978–1–944835–15- 6.Accessed: 15 Sept 2019
EUROPEAN UNION AGENCY FOR CYBERSECURITY. About ENISA. [Online]. https://www.enisa.europa.eu/. Accessed: 21 Sept 2019
Senyo PK, Addae E, Boateng R (2018) Cloud computing research: a review of research themes, frameworks, methods and future research directions. Int J Inf Manage 38(1):128–139
Tanzim Khorshed MD, Shawkat Ali ABM, Wasimi SA (2012) A survey on gaps, threat remediation challenges and some thoughts for proactive attack detection in cloud computing. Future Generation Comput Syst 28(6):833–851
Mell P, Grance T (2011) The NIST definition of cloud computing: recommendations of the national institute of standards and technology. NIST Spec Publ 800–145:1–7
Liu F, Tong J, Mao J, Bohn R, Messina J, Badger L, Leaf D (2012) NIST cloud computing reference architecture: recommendations of the national institute of standards and technology. NIST Spec Publ 500–292:1–35
Rittinghouse J.W, Ransome JF Cloud Computing Implementation, Management, and Security, Version Date: 2013 11 21, Taylor & Francis, Boca Raton, FL, USA:CRC Press, ISBN:978-1-4398-0681-4
Cloud Security Alliance. “Security Guidance for critical areas of focus in Cloud Computing V3.0”, 2011. [Online]. https://cloudsecurityalliance.org/artifacts/security-guidance-for-critical-areas-of-focus-in-cloud-computing-v3/. 29 July 2019
Varghese B, Buyya R (2018) Next generation cloud computing: new trends and research directions. Future Generation Comput Syst 79:849–861
Wailly A (2014) End-to-end security architecture for cloud computing environments. Doctoral thesis in Networking and Internet Architecture. National Institute of Telecommunications, (2014). English. p.180. <NNT: 2014TELE0020 >.
Meye. PO (2016) Dependability in cloud storage. Doctoral thesis in Distributed, Parallel, and Cluster Computing. Rennes University. 2016. English. P.130. < 10 NNT: 2016REN1S091 >.
Becker JD,Bailey E (2014) A comparison of IT Governance and control frameworks in cloud computing. In: Proceedings of twentieth americas conference on information systems, Savannah, pp 1–16.
Bulla CM, Bhojannavar SS, Danawade VM (2013) Cloud computing: research activities and challenges. Int J Emerging Trends Technol Comput Sci (IJETTCS) 2(5):206–214
Victor ICC (2020) A proposed framework for cloud computing adoption. In: Sustainable business: concepts, methodologies, tools, and applications, 2020, pp 978–1003. IGI Global.
Ko RK, Jagadpramana P, Mowbray M, Pearson S, Kirchberg M, Liang Q, Lee BS, TrustCloud: a framework for accountability and trust in cloud computing. In: 2011 IEEE World Congress on Services, SERVICES, July, 2011, pp 584–588.
ISO/IEC 27032:2012(E) information technology e security techniques e guidelines for Cyber Security, Geneva, Switzerland: ISO/IEC, 2012.
Hasrouny H, Samhat AE, Bassil C, Laouiti A (2017) VANet security challenges and solutions: a survey. Vehicular Commun 7:7–20
Rowe and Barry Lunt DC (2012) Mapping the cyber security terrain in a research context. In: Proceedings of the 1st annual conference on research in information technology, pp 7–12, Calgary, Alberta, Canada—October 11–13
Public Safety Canada, “National Cyber Security Strategy: Canada’s vision for security and prosperity in the digital age”. (2018). [Online]. https://www.publicsafety.gc.ca/cnt/rsrcs/pblctns/ntnl-cbr-scrt-strtg/ntnl-cbr-scrt-strtg-en.pdf
Von Solms B, von Solms R (2018) Cyber Security and information security—What goes where? Inform Comput Security 26(1):2–9
International Telecommunications Union (ITU). “Overview of Cybersecurity: Recommendation ITU-T X.1205, Geneva: International Telecommunication Union (ITU)”. (2009). https://www.itu.int/rec/T-REC-X.1205-200804-I/en
Bahuguna A, Bisht RK, Pande J (2018) Roadmap amid chaos: cyber security management for organisations. In: Proceedings of the ninth international conference on computing communication and networking technologies (ICCCNT), pp 1–6
Disterer G (2013) ISO/IEC 27000, 27001 and 27002 for information security management. J Inform Security 4(2):92–100
Humphreys E (2011) Information security management system standards. Datenschutz und Datensicherheit 35(1):7–11
ISO/IEC. 27017:2015, “Information technology—Security techniques—Code of practice for information security controls based on ISO/IEC 27002 for cloud services”, 2015.
ISO/IEC. 27001:2013, “International standard ISO/IEC Information technology—Security techniques—Information security management systems—Requirements”, vol. 2013, 2013.
ISO/IEC. 27000:2018, “Information technology—Security techniques—Information security management systems—Overview and vocabulary”, 2018.
ISO/IEC. 27002:2013, “Information technology—Security techniques—Code of practice for Information security controls”, 2013.
NIST, “Framework for Improving Critical Infrastructure Cybersecurity”. Version 1.0. (2014). [Online]. Available at https://www.nist.gov/document-3766
NIST, “Glossary of Key Information Security Terms”. NISTIR 7298 Rev.3. (2019). [Online]. https://doi.org/10.6028/NIST.IR.7298r3
Krumay B, Bernroider EWN, Walser R (2018) Evaluation of cybersecurity management controls and metrics of critical infrastructures: a literature review considering the NIST Cybersecurity Framework. In: Gruschka N. (ed) NordSec. Lecture Notes in Computer Science, vol 11252, pp 369–384.
NIST, “Framework for improving critical infrastructure cybersecurity”, Version1.1, (2018). [Online]. https://doi.org/10.6028/NIST.CSWP.04162018
Mbanaso UM, Abrahams L, Apene OZ (2019) Conceptual design of a cybersecurity resilience maturity measurement (CRMM) framework. African J Inform Commun 23:1–26
Chang V, Kuo YH, Ramachandran M (2016) a Cloud computing adoption framework: a security framework for business clouds. Future Generation Comput Syst 57:24–41
Chang V, Ramachandran M, Yao Y (2016) Chung-Sheng Li, A resiliency framework for an enterprise cloud. Int J Inf Manage 36(1):155–166
Wendler R (2012) The maturity of maturity model research: a systematic mapping study. Inf Softw Technol 54(12):1317–1339
Almuhammadi S, Majeed A (2017) Information Security maturity model for NIST cyber security framework. Comput Sci Inform Technol 51:51–62
Le NT, Hoang DB (2017) Capability maturity model and metrics framework for cyber cloud security. Scalable Comput 4:277–290
Abdel-Basset M, Mohamed M, Chang V (2018) NMCDA: a framework for evaluating cloud computing services. Future Generation Comput Syst 86:12–29
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tissir, N., El Kafhali, S. & Aboutabit, N. Cybersecurity management in cloud computing: semantic literature review and conceptual framework proposal. J Reliable Intell Environ 7, 69–84 (2021). https://doi.org/10.1007/s40860-020-00115-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40860-020-00115-0




