Abstract
The “Ping-Pong” (PP) protocol is a two-way quantum key protocol based on entanglement. In this protocol, Bob prepares one maximally entangled pair of qubits and sends one qubit to Alice. Then, Alice performs some necessary operations on this qubit and sends it back to Bob. Although this protocol was proposed in 2002, its security in the noisy and lossy channel has not been proven. In this report, we add a simple and experimentally feasible modification to the original PP protocol and prove the security of this modified PP protocol against collective attacks when the noisy and lossy channel is taken into account. Simulation results show that our protocol is practical.
Similar content being viewed by others
Introduction
Quantum key distribution (QKD)1,2 allows two remote parties (Alice and Bob) to establish unconditional secure-key bits. Research of QKD mainly concerns one-way protocols. BB841 protocol is the most commonly used one-way QKD protocol. One-way QKD protocols need the information carriers to be transferred from Alice to Bob via the quantum channel to generate the secure-key bits. For example, in BB84, Alice randomly prepares her qubits into one of the quantum states |0〉, |1〉,  and
and  and sends them to Bob via an untrusted quantum channel. Then Bob performs some measurements on the incoming qubits and key bits are generated.
and sends them to Bob via an untrusted quantum channel. Then Bob performs some measurements on the incoming qubits and key bits are generated.
In the past decade, some two-way QKD protocols have been proposed3,4,5,6,7 and experimentally realized8,9,10,11,12. In these protocols, Bob prepares some quantum states and sends them to Alice, Alice performs encoding operations on the received states and sends them back in the same quantum channel, then Bob makes some measurements and gets the key bits. Typical examples of these protocols are “Ping-Pong” (PP)3 protocol, LM056 protocol and N097 protocol. The first one uses entanglement while the last two protocols not. These protocols are all deterministic, which means Bob can obtain Alice's key bits directly, without a basis reconciliation step.
The major difficulty of the security proof for the two-way QKD protocols is that the eavesdropper, Eve, may attack the travel qubit on both the forward (Bob-Alice) channel and the backward (Alice-Bob) channel. This makes the security analysis quite complicated. Fortunately, for the LM05 protocol, its security has been proven in different ways13,14,15 recently and N09 protocol is also proven to be secure in Refs. 16, 17. A super dense coding (SDC) protocol similar to PP protocol is also proved secure15. However, these proofs are all based on the assumption that there are no losses in the channel and detectors. In fact, the security of PP protocol has been challenged by channel loss18,19,20,21. Hence, the security of PP protocol when loss is considered remains an open question until now.
In this paper, we propose a modified Ping-Pong protocol and prove its security against collective attacks in noisy and lossy channel. To the best of our knowledge, this is the first security proof of PP protocol considering the loss in channel.
Original ping-pong protocol
It's beneficial to give a brief description of the PP protocol. Consider that Bob prepares two-qubits maximally entangled state  , where |0〉 and |1〉 are the eigenstates of Pauli matrix σz. He sends one of the qubits (travel qubit) to Alice via an untrusted channel and retains the other (home qubit) in her quantum memory. Then, Alice randomly chooses message mode or control mode to proceed. In message mode, Alice performs an unitary operation I to the incoming qubit to encode classical bit 0, or σz to encode bit 1. After her encoding operation, Alice sends this qubit back to Bob. When Bob receives the travel qubit, he performs a Bell measurement on both qubits to decode Alice's bit. In control mode, Alice measures the travel qubit in the basis Bz = {|0〉, |1〉} and announces her measurement outcome through an authenticated channel. On receiving Alice's measurement result, Bob also measures his home qubit with Bz and compare his own measurement result with Alice's. If Alice's and Bob's measurement results coincide, the PP protocol continues; otherwise, they may terminate the protocol. Hence the control mode is used to guarantee the security, while the message mode is for key distribution.
, where |0〉 and |1〉 are the eigenstates of Pauli matrix σz. He sends one of the qubits (travel qubit) to Alice via an untrusted channel and retains the other (home qubit) in her quantum memory. Then, Alice randomly chooses message mode or control mode to proceed. In message mode, Alice performs an unitary operation I to the incoming qubit to encode classical bit 0, or σz to encode bit 1. After her encoding operation, Alice sends this qubit back to Bob. When Bob receives the travel qubit, he performs a Bell measurement on both qubits to decode Alice's bit. In control mode, Alice measures the travel qubit in the basis Bz = {|0〉, |1〉} and announces her measurement outcome through an authenticated channel. On receiving Alice's measurement result, Bob also measures his home qubit with Bz and compare his own measurement result with Alice's. If Alice's and Bob's measurement results coincide, the PP protocol continues; otherwise, they may terminate the protocol. Hence the control mode is used to guarantee the security, while the message mode is for key distribution.
In next section, the modified PP protocol will be given.
Modified ping-pong protocol
In the modified PP protocol, we also use the maximal EPR pair  . This protocol process contains four steps:
. This protocol process contains four steps:
-
1
Bob prepares N pairs of entangled states
 . He sends half of states (travel qubits) to Alice through a noisy and lossy quantum channel(forward channel) and keeps the other half (home qubits) in his quantum memory.
. He sends half of states (travel qubits) to Alice through a noisy and lossy quantum channel(forward channel) and keeps the other half (home qubits) in his quantum memory. -
2
Alice randomly switches to message mode or control mode with probability c and 1 − c respectively. In message mode, Alice performs one of the four unitary operations I0, I1, Y0 and Y1 to the incoming states, i.e.,

where |v〉 means the vacuum state. Due to the existence of vacuum state, I0 and I1 are no longer identical. So is Y0 and Y1. The probabilities of each operation are all 1/4. For operations I0 and I1, Alice records her classical information as bit 0. For Y0 and Y1, Alice records bit 1. Then Alice sends the encoded states back to Bob through the backward channel. In control mode, Alice measures the incoming signals with projectors {|v〉 〈v|, |0〉 〈0|, |1〉 〈1|}. Then Alice records her measurement results.
-
3
Bob also randomly switches to message mode or control mode with probability c and 1 − c respectively. In message mode, Bob performs a Bell-states measurement on his home qubit and his received travel qubit to decode Alice's information (i.e., when Alice encodes bit 0, Bob may obtain the Bell state
 ; when Alice encodes bit 1, Bob may obtain
; when Alice encodes bit 1, Bob may obtain  ). In control mode, Bob measures his reserved qubits with projectors {|v〉 〈v|, |0〉 〈0|, |1〉 〈1|} and records the measurement results.
). In control mode, Bob measures his reserved qubits with projectors {|v〉 〈v|, |0〉 〈0|, |1〉 〈1|} and records the measurement results. -
4
Alice and Bob publicly announces which trials are in message mode, which are in control mode and their measurements results in control mode. Then Alice and Bob can share the probabilities p00, p01, p0v, p10, p11 and p1v (i.e. p0v is the probability Alice receives a vacuum state when the travel qubit is |0〉 and other probabilities have the similar meanings). These probabilities will be used to bound the eavesdropper Eve's information on key bits. By sacrificing certain bits for error testing, Alice and Bob can also estimate the error rate e for their key bits. Alice and Bob then do classical postprocessing error correction (EC) and privacy amplification (PA) to generate secure-key bits.
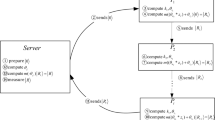
The protocol flow is illustrated in Fig. 1.
Coding system of modified PP protocol.
There are two modes: message mode(solid line) and control mode(dash line) in the operations of Alice and Bob. In message mode, if Alice wants to encode bit 0, she will randomly perform I0 or I1. If Alice wants to encode bit 1, she will randomly perform Y0 or Y1. The operations are defined as I0{|v〉, |0〉, |1〉} = {|v〉, |0〉, |1〉}, I1{|v〉, |0〉, |1〉} = {|v〉, −|0〉, −|1〉}, Y0{|v〉, |0〉, |1〉} = {|v〉, |0〉, −|1〉}, Y1{|v〉, |0〉, |1〉} = {|v〉, −|0〉, |1〉}. BSM is for Bell-states measurement and Z represents the measurement defined by projectors {|v〉〈v|, |0〉〈0|, |1〉〈1|}.
Security proof of modified ping-pong protocol
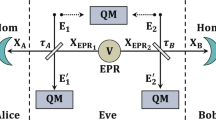
Eve's Attack in the Bob-Alice channel
Eve's most general collective attack in the Bob-Alice channel can be written in the form

where p0v is the probability Alice receives a vacuum state when the travel qubit is |0〉, so is p00, p01, p1v, p10 and p11. Normalized vectors|Eiv〉 and |Eij〉 are possible quantum states of Eve's ancilla.
So the joint density matrix of the travel qubit and Eve's ancilla becomes

in which,P{|x〉} = |x〉 〈x|.
After receiving the forward qubits, in encoding mode, Alice will encode her key bits onto the forward qubit by the operations I0, I1, Y0 and Y1 with the same probability 1/4. The operations I0 and I1 result in the same encoding key bit 0, Y0 and Y1 result in bit 1. The probabilities that Alice encodes key bit 0 or 1 are still both 1/2.
Let us at first consider the case where Bob's travel qubit collapses into |0〉 (i.e., this case corresponds to the third row of the Eq. (2).). After Alice encoding bit 0, the joint state of Alice and Eve becomes

For the case Alice encodes bit 1, the state is

As described in our modified protocol, Eve cannot obtain any information from the vacuum state. So we can exclude the vacuum state from the joint state and renormalize effective encoding density matrices. Define η→ = p00 + p01,  and
and  (i.e., η→ can be understood as the efficiency for the forward channel and is estimated directly in experiment.), then the effective encoding matrices in the orthogonal basis {|0〉A|E00〉, |1〉A|E01〉} are given by
(i.e., η→ can be understood as the efficiency for the forward channel and is estimated directly in experiment.), then the effective encoding matrices in the orthogonal basis {|0〉A|E00〉, |1〉A|E01〉} are given by


Since the density matrix we get is already diagonal, our following calculations can be very simple. With system AE, Eve's Von-Neumann entropies on Alice's key bit A′, is given by:

where H is the Shannon's binary entropy function.
Eve's Attack in the Alice-Bob channel
Quantum systems AE on the backward channel can be divided into two events: Bob receives the travel qubit and not. We label these two parts as  and
and  . As showed in the prior section, the ratio of the two parts are η← and 1 − η← respectively (i.e., η← is the efficiency of backward channel and can be estimated by Alice and Bob in experiment.). Our goal is to get the lower bound of H(A|E)received, which means the conditional entropy of Alice on Eve in the case Bob receives the backward qubits. From definition, we have
. As showed in the prior section, the ratio of the two parts are η← and 1 − η← respectively (i.e., η← is the efficiency of backward channel and can be estimated by Alice and Bob in experiment.). Our goal is to get the lower bound of H(A|E)received, which means the conditional entropy of Alice on Eve in the case Bob receives the backward qubits. From definition, we have


According to the joint entropy theorem and noticing that the events Bob receives a returning qubit or not are orthogonal, we obtain


By (10)–(11),

To obtain the lower bound of S(A′|AE)received, it is reasonable to assume that Eve has maximal entropy of Alice's key bit A′ in the case Bob doesn't receive the backward qubit. And recall Eq. (7), we get

Combined with the case that Bob's travel qubit collapsed into |1〉, Eve's total entropy on Alice is given by:

Secure key rate
We assume that the raw key bits are unbiased distributed, which means the error rate Alice encodes 0 or 1 are equal. The error bit e is defined as the probability Alice encodes 0 but the BSM gets |Φ−〉 or Alice encodes 1 but the BSM gets |Φ+〉. By the authenticated communications, Alice and Bob can estimate the error rate e of their raw key bits. Then they will perform error correction and privacy amplification to generate the secure-key bits. The secure-key rate is given by22:

where, S(A′|B) is the conditional entropy for Bob's key bits to Alice's key bits and equals H(e) under the unbiased distribution assumption.
We can find the the secure-key rate for this modified PP protocol is very simple. Eve's information on key bits can be just bounded by the error rates for forward channel  ,
,  and the efficiency of backward channel η←. The physics behind our proof is that our operation I0, I1, Y0 and Y1 will introduce a phase randomization to Eve's accessed system AE. This phase randomization will lead to the decoherence of system AE and limit the information that can be gained by Eve.
and the efficiency of backward channel η←. The physics behind our proof is that our operation I0, I1, Y0 and Y1 will introduce a phase randomization to Eve's accessed system AE. This phase randomization will lead to the decoherence of system AE and limit the information that can be gained by Eve.
Simulation
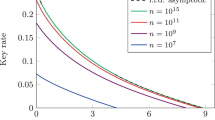
To estimate the performance of our protocol, numerical simulation is given. In this simulation, we use the polarization state of photon transmitted in optical fiber to realize the coding system. On Bob's side, the home qubit is assumed to transmit in a round channel whose the efficiency is the same as the Bob-Alice-Bob channel for simplicity. We use off-the-shelf experimental parameters to establish the simulation, e.g., optical fiber is of an attenuation of 0.20 dB/km, detection efficiency is ηd = 10% and its dark count rate is pd = 10−5. Besides, we consider a misalignment of detector as de = 1%, η→ and η← in the key rate generation formula just equal the transmission efficiency of the corresponding optical fiber η. All the polarization error corresponding to  comes from dark count of single photon detector, so
comes from dark count of single photon detector, so  . For the error rate between Alice and Bob, it only comes from dark count as
. For the error rate between Alice and Bob, it only comes from dark count as  . The overall secure-key generation rate is thus
. The overall secure-key generation rate is thus  per trial. The simulation is shown in Fig. 2. This result show that the modified PP protocol can distribute secure-key bits for distant peers around 50 km.
per trial. The simulation is shown in Fig. 2. This result show that the modified PP protocol can distribute secure-key bits for distant peers around 50 km.
Discussion and conclusion
Two-way deterministic QKD protocols, including PP protocol, do not require basis choices. Thus every encoded bit is used for final key generation. Besides, it has been proved some two-way deterministic QKD protocols are secure against detector-side-channel attacks on the backward channel23. These advantages make such type protocols potentially useful.
The security of PP protocol when channel loss and noise are presented has been an open problem for a long time. To overcome this problem, we add a simple and experimentally feasible modification to the original PP protocol. Quite interestingly, our modification only leads to a trivial overall to the system of Alice and Bob, but can introduce a phase randomization for Eve's system. With the effects of this phase randomization, we prove the security of this modified PP protocol when the noisy and lossy channel is taken into account. Simulation results show that our protocol is practical. And we also hope that our modification on PP protocol can shed lights on other two-way QKD protocols.
References
Bennett, C. H., & Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing. IEEE International Conference on Computers, Systems and Signal Processing 175–179 (IEEE Press, New York, 1984).
Gisin, N., Ribordy, G., Tittle, W. & Zbinden, H. Quantum Cryptography. Rev. Mod. Phys 74, 145–195 (2002).
Boström, K. & Felbinger, T. Deterministic Secure Direct Communication Using Entanglement. Phys. Rev. Lett. 89, 187902 (2002).
Cai, Q. &. Li, B. Improving the capacity of the Boström-Felbinger protocol. Phys. Rev. A 69, 054301 (2004).
Cai, Q. & Li, B. Deterministic secure communication without using entanglemen. Chin. Phys. Lett. 21, 601 (2004).
Lucamarini, M. & Mancini, S. Secure Deterministic Communication without Entanglement. Phys. Rev. Lett. 94, 140501 (2005).
Noh, T.-G. Counterfactual Quantum Cryptography Phys. Rev. Lett. 103, 230501 (2009).
Ostermeyer, M. & Walenta, N. On the implementation of a deterministic secure coding protocol using polarization entangled photons. Optics Communications 281, 4540 (2008).
Abdul Khir, M. F., Mohd Zain, M. N., Bahari, I., Suryadi & Shaari, S. Implementation of two way Quantum Key Distribution protocol with decoy state. Optics Communications 285, 842 (2012).
Ren, M., Wu, G., Wu, E. & Zeng, H. P. Experimental demonstration of counterfactual quantum key distribution. Laser Physics 21, 755–760.
Brida et al. Experimental realization of Counterfactual Quantum Cryptography. Laser Phys. Lett. 3, pp 247 (2012).
Liu, Y. et al. Experimental Demonstration of Counterfactual Quantum Communication. Phys. Rev. Lett. 109, 030501 (2012).
Lu, H., Fung, C.-H. F., Ma, X. & Cai, Q. Unconditional security proof of a deterministic quantum key distribution with a two-way quantum channel. Physical Review A 84, 042344 (2011).
Fung, C.-H. F., Ma, X., Chau, H. F. & Cai, Q. Quantum key distribution with delayed privacy amplification and its application to the security proof of a two-way deterministic protocol. Physical Review A 85, 032308 (2012).
Beaudry, N. J., Lucamarini, M., Mancini, S. & Renner, R. Security of two-way quantum key distribution. Physical Review A 88,062302 (2013).
Yin, Z. Q., Li, H. W., Chen, W., Han, Z. F. & Guo, G.-C. Security of counterfactual quantum cryptography. Physical Review A 82, 042335 (2010).
Yin, Z. Q. et al. Counterfactual quantum cryptography based on weak coherent states. Physical Review A 86, 022313 (2012).
Cai, Q. The “Ping-Pong” Protocol Can Be Attacked without Eavesdropping. Physical Review Letters 91,109801 (2003).
Wójcik A. Eavesdropping on the “Ping-Pong” Quantum Communication Protocol. Physical Review Letters 90,157901 (2003).
Zhang, Z., Man, Z. & Li, Y. Improving Wójciks eavesdropping attack on the ping-pong protocol. Physics Letters A 333, 46 (2004).
Boström, K. & Felbinger, T. On the security of the ping-pong protocol. Physics Letters A 372, 22 (2008).
Devetak, I. & Winter, A. Distillation of secret key and entanglement from quantum states. Proc. R. Soc. Lond. A 461, 207 (2005).
Lu, H., Fung, C.-H. F. & Cai, Q. Two-way deterministic quantum key distribution against detector-side-channel attacks. Physical Review A 88,044302 (2013).
Acknowledgements
This work was supported by the National Basic Research Program of China (Grants No. 2011CBA00200 and No. 2011CB921200), National Natural Science Foundation of China (Grants No. 61101137 and No. 61201239).
Author information
Authors and Affiliations
Contributions
For this publication, Z.Y. proposed the protocol. Y.H. did the analysis. H.L. wrote the main manuscript and S.W. prepared figures 1–2. W.C., Z.H. and G.G. provided essential comments to the manuscript. All authors reviewed the manuscript. The first two authors contributed equally in this letter.
Ethics declarations
Competing interests
The authors declare no competing financial interests.
Rights and permissions
This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 3.0 Unported License. The images in this article are included in the article's Creative Commons license, unless indicated otherwise in the image credit; if the image is not included under the Creative Commons license, users will need to obtain permission from the license holder in order to reproduce the image. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/
About this article
Cite this article
Han, YG., Yin, ZQ., Li, HW. et al. Security of modified Ping-Pong protocol in noisy and lossy channel. Sci Rep 4, 4936 (2014). https://doi.org/10.1038/srep04936
Received:
Accepted:
Published:
DOI: https://doi.org/10.1038/srep04936
This article is cited by
-
Detector blinding attacks on counterfactual quantum key distribution
Quantum Information Processing (2021)
-
State-of-the-Art Survey of Quantum Cryptography
Archives of Computational Methods in Engineering (2021)
-
Ping-pong quantum key distribution with trusted noise: non-Markovian advantage
Quantum Information Processing (2020)
-
Decoherence can help quantum cryptographic security
Quantum Information Processing (2018)
-
Deterministic MDI QKD with two secret bits per shared entangled pair
Quantum Information Processing (2018)
Comments
By submitting a comment you agree to abide by our Terms and Community Guidelines. If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.

 . He sends half of states (travel qubits) to Alice through a noisy and lossy quantum channel(forward channel) and keeps the other half (home qubits) in his quantum memory.
. He sends half of states (travel qubits) to Alice through a noisy and lossy quantum channel(forward channel) and keeps the other half (home qubits) in his quantum memory.
 ; when Alice encodes bit 1, Bob may obtain
; when Alice encodes bit 1, Bob may obtain  ). In control mode, Bob measures his reserved qubits with projectors {|v〉 〈v|, |0〉 〈0|, |1〉 〈1|} and records the measurement results.
). In control mode, Bob measures his reserved qubits with projectors {|v〉 〈v|, |0〉 〈0|, |1〉 〈1|} and records the measurement results.
