Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Galbraith, Steven D.
Petit, Christophe
Shani, Barak
and
Ti, Yan Bo
2016.
Advances in Cryptology – ASIACRYPT 2016.
Vol. 10031,
Issue. ,
p.
63.
Biasse, Jean-François
Fieker, Claus
and
Jacobson, Michael J.
2016.
Fast heuristic algorithms for computing relations in the class group of a quadratic order, with applications to isogeny evaluation.
LMS Journal of Computation and Mathematics,
Vol. 19,
Issue. A,
p.
371.
Petit, Christophe
2017.
Advances in Cryptology – ASIACRYPT 2017.
Vol. 10625,
Issue. ,
p.
330.
Galbraith, Steven D.
Petit, Christophe
and
Silva, Javier
2017.
Advances in Cryptology – ASIACRYPT 2017.
Vol. 10624,
Issue. ,
p.
3.
Smith, Benjamin
2018.
Arithmetic of Finite Fields.
Vol. 11321,
Issue. ,
p.
3.
Eisenträger, Kirsten
Hallgren, Sean
Lauter, Kristin
Morrison, Travis
and
Petit, Christophe
2018.
Advances in Cryptology – EUROCRYPT 2018.
Vol. 10822,
Issue. ,
p.
329.
Galbraith, Steven D.
and
Vercauteren, Frederik
2018.
Computational problems in supersingular elliptic curve isogenies.
Quantum Information Processing,
Vol. 17,
Issue. 10,
Bank, Efrat
Camacho-Navarro, Catalina
Eisenträger, Kirsten
Morrison, Travis
and
Park, Jennifer
2019.
Research Directions in Number Theory.
Vol. 19,
Issue. ,
p.
41.
Flynn, E. V.
and
Ti, Yan Bo
2019.
Post-Quantum Cryptography.
Vol. 11505,
Issue. ,
p.
286.
De Feo, Luca
Masson, Simon
Petit, Christophe
and
Sanso, Antonio
2019.
Advances in Cryptology – ASIACRYPT 2019.
Vol. 11921,
Issue. ,
p.
248.
Xu, Xiu
Leonardi, Chris
Teh, Anzo
Jao, David
Wang, Kunpeng
Yu, Wei
and
Azarderakhsh, Reza
2019.
Information Security Practice and Experience.
Vol. 11879,
Issue. ,
p.
293.
Li, Songsong
Ouyang, Yi
and
Xu, Zheng
2020.
Neighborhood of the supersingular elliptic curve isogeny graph at j = 0 and 1728.
Finite Fields and Their Applications,
Vol. 61,
Issue. ,
p.
101600.
De Feo, Luca
Kohel, David
Leroux, Antonin
Petit, Christophe
and
Wesolowski, Benjamin
2020.
Advances in Cryptology – ASIACRYPT 2020.
Vol. 12491,
Issue. ,
p.
64.
Castryck, Wouter
Panny, Lorenz
and
Vercauteren, Frederik
2020.
Advances in Cryptology – EUROCRYPT 2020.
Vol. 12106,
Issue. ,
p.
523.
Love, Jonathan
and
Boneh, Dan
2020.
Supersingular curves with small noninteger endomorphisms.
Open Book Series,
Vol. 4,
Issue. 1,
p.
7.
Merz, Simon-Philipp
Minko, Romy
and
Petit, Christophe
2020.
Topics in Cryptology – CT-RSA 2020.
Vol. 12006,
Issue. ,
p.
496.
Galbraith, Steven D.
Petit, Christophe
and
Silva, Javier
2020.
Identification Protocols and Signature Schemes Based on Supersingular Isogeny Problems.
Journal of Cryptology,
Vol. 33,
Issue. 1,
p.
130.
Costello, Craig
and
Smith, Benjamin
2020.
Post-Quantum Cryptography.
Vol. 12100,
Issue. ,
p.
151.
Castryck, Wouter
Decru, Thomas
and
Smith, Benjamin
2020.
Hash functions from superspecial genus-2 curves using Richelot isogenies.
Journal of Mathematical Cryptology,
Vol. 14,
Issue. 1,
p.
268.
Burdges, Jeffrey
and
De Feo, Luca
2021.
Advances in Cryptology – EUROCRYPT 2021.
Vol. 12696,
Issue. ,
p.
302.
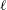 $\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\ell $-isogeny path problem
$\def \xmlpi #1{}\def \mathsfbi #1{\boldsymbol {\mathsf {#1}}}\let \le =\leqslant \let \leq =\leqslant \let \ge =\geqslant \let \geq =\geqslant \def \Pr {\mathit {Pr}}\def \Fr {\mathit {Fr}}\def \Rey {\mathit {Re}}\ell $-isogeny path problem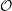 $\mathcal{O}$ be a maximal order in a definite quaternion algebra over
$\mathcal{O}$ be a maximal order in a definite quaternion algebra over 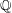 $\mathbb{Q}$ of prime discriminant
$\mathbb{Q}$ of prime discriminant 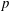 $p$, and
$p$, and 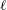 $\ell $ a small prime. We describe a probabilistic algorithm which, for a given left
$\ell $ a small prime. We describe a probabilistic algorithm which, for a given left 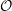 $\mathcal{O}$-ideal, computes a representative in its left ideal class of
$\mathcal{O}$-ideal, computes a representative in its left ideal class of 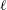 $\ell $-power norm. In practice the algorithm is efficient and, subject to heuristics on expected distributions of primes, runs in expected polynomial time. This solves the underlying problem for a quaternion analog of the Charles–Goren–Lauter hash function, and has security implications for the original CGL construction in terms of supersingular elliptic curves.
$\ell $-power norm. In practice the algorithm is efficient and, subject to heuristics on expected distributions of primes, runs in expected polynomial time. This solves the underlying problem for a quaternion analog of the Charles–Goren–Lauter hash function, and has security implications for the original CGL construction in terms of supersingular elliptic curves.



