Quantum one-time tables for unconditionally secure qubit-commitment
1Department of Physics and Astronomy, Seoul National University, Seoul, 151-742, Korea
2QOLS, Blackett Laboratory, Imperial College London, London SW7 2AZ, United Kingdom
3Korea Institute for Advanced Study, Seoul, 02455, Korea
| Published: | 2021-03-10, volume 5, page 405 |
| Eprint: | arXiv:1903.12304v4 |
| Doi: | https://doi.org/10.22331/q-2021-03-10-405 |
| Citation: | Quantum 5, 405 (2021). |
Find this paper interesting or want to discuss? Scite or leave a comment on SciRate.
Abstract
The commodity-based cryptography is an alternative approach to realize conventionally impossible cryptographic primitives such as unconditionally secure bit-commitment by consuming pre-established correlation between distrustful participants. A unit of such classical correlation is known as the one-time table (OTT). In this paper, we introduce a new example besides quantum key distribution in which quantum correlation is useful for cryptography. We propose a scheme for unconditionally secure qubit-commitment, a quantum cryptographic primitive forbidden by the recently proven no-masking theorem in the standard model, based on the consumption of the quantum generalization of the OTT, the bipartite quantum state we named $\textit{quantum one-time tables}$ (QOTT). The construction of the QOTT is based on the newly analyzed internal structure of quantum masker and the quantum secret sharing schemes. Our qubit-commitment scheme is shown to be universally composable. We propose to measure the randomness cost of preparing a (Q)OTT in terms of its entropy, and show that the QOTT with superdense coding can increase the security level with half the cost of OTTs for unconditionally secure bit-commitment. The QOTT exemplifies an operational setting where neither maximally classically correlated state nor maximally entangled state, but rather a well-structured partially entangled mixed state is more valuable resource.
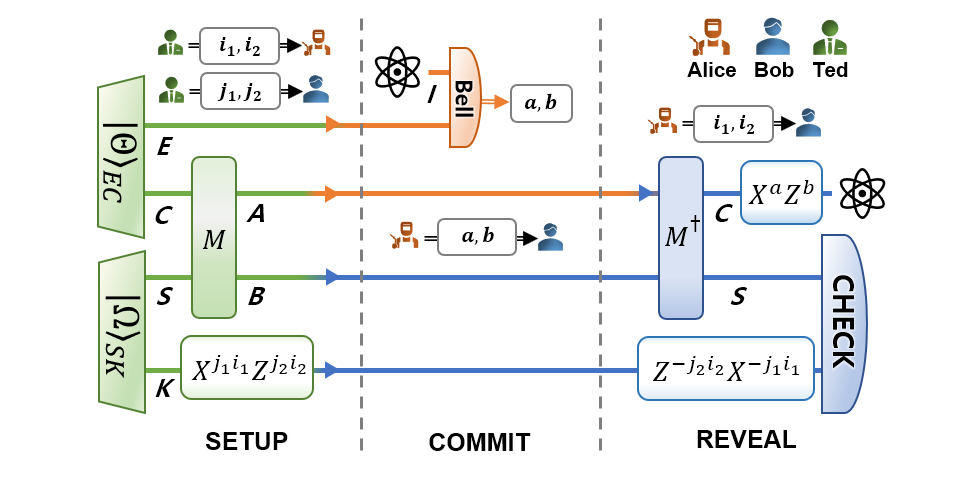
Featured image: A schematic depiction of the qubit-commitment protocol utilizing the quantum one-time table.
Popular summary
► BibTeX data
► References
[1] Ronald Rivest. Unconditionally secure commitment and oblivious transfer schemes using private channels and a trusted initializer. Unpublished manuscript, 1999. URL http://people.csail.mit.edu/rivest/Rivest-commitment.pdf.
http://people.csail.mit.edu/rivest/Rivest-commitment.pdf
[2] MO Rabin. technical report tr-81. technical report TR-81, 1981. 10.1145/191177.191221.
https://doi.org/10.1145/191177.191221
[3] S Even, O Goldreich, and A Lempel. Advances in cryptology: Proceedings of crypto’82. Plenum, 28: 205, 1982. 10.1007/978-1-4757-0602-4_19.
https://doi.org/10.1007/978-1-4757-0602-4_19
[4] Gilles Brassard, Claude Crépeau, Richard Jozsa, and Denis Langlois. A quantum bit commitment scheme provably unbreakable by both parties. In Proceedings of 1993 IEEE 34th Annual Foundations of Computer Science, pages 362–371. IEEE, 1993. 10.1109/SFCS.1993.366851.
https://doi.org/10.1109/SFCS.1993.366851.
[5] Dominic Mayers. Unconditionally secure quantum bit commitment is impossible. Physical Review Letters, 78 (17): 3414, 1997. 10.1103/PhysRevLett.78.3414.
https://doi.org/10.1103/PhysRevLett.78.3414
[6] Hoi-Kwong Lo and Hoi Fung Chau. Is quantum bit commitment really possible? Physical Review Letters, 78 (17): 3410, 1997. 10.1103/PhysRevLett.78.3410.
https://doi.org/10.1103/PhysRevLett.78.3410
[7] Adrian Kent. Unconditionally secure bit commitment. Physical Review Letters, 83 (7): 1447, 1999. 10.1103/PhysRevLett.83.1447.
https://doi.org/10.1103/PhysRevLett.83.1447
[8] Tommaso Lunghi, Jedrzej Kaniewski, Félix Bussieres, Raphaël Houlmann, Marco Tomamichel, Adrian Kent, Nicolas Gisin, Stephanie Wehner, and Hugo Zbinden. Experimental bit commitment based on quantum communication and special relativity. Physical review letters, 111 (18): 180504, 2013. 10.1103/PhysRevLett.111.180504.
https://doi.org/10.1103/PhysRevLett.111.180504.
[9] Adrian Kent. Unconditionally secure bit commitment by transmitting measurement outcomes. Physical review letters, 109 (13): 130501, 2012. 10.1103/PhysRevLett.109.130501.
https://doi.org/10.1103/PhysRevLett.109.130501.
[10] Donald Beaver. Commodity-based cryptography. In Proceedings of the twenty-ninth annual ACM symposium on Theory of computing, pages 446–455, 1997. 10.1145/258533.258637.
https://doi.org/10.1145/258533.258637
[11] Donald Beaver. One-time tables for two-party computation. In International Computing and Combinatorics Conference, pages 361–370. Springer, 1998. 10.1007/3-540-68535-9_40.
https://doi.org/10.1007/3-540-68535-9_40
[12] Li Yu. Quantum preprocessing for information-theoretic security in two-party computation. arXiv preprint arXiv:1908.05584, 2019. URL https://arxiv.org/abs/1908.05584.
arXiv:1908.05584
[13] Kavan Modi, Arun Kumar Pati, Aditi Sen, Ujjwal Sen, et al. Masking quantum information is impossible. Physical Review Letters, 120 (23): 230501, 2018. 10.1103/PhysRevLett.120.230501.
https://doi.org/10.1103/PhysRevLett.120.230501
[14] Richard Cleve, Daniel Gottesman, and Hoi-Kwong Lo. How to share a quantum secret. Physical Review Letters, 83 (3): 648, 1999. 10.1103/PhysRevLett.83.648.
https://doi.org/10.1103/PhysRevLett.83.648
[15] Daniel Gottesman. Theory of quantum secret sharing. Physical Review A, 61 (4): 042311, 2000. 10.1103/PhysRevA.61.042311.
https://doi.org/10.1103/PhysRevA.61.042311
[16] William K Wootters and Wojciech H Zurek. A single quantum cannot be cloned. Nature, 299 (5886): 802, 1982. 10.1038/299802a0.
https://doi.org/10.1038/299802a0
[17] Howard Barnum, Carlton M Caves, Christopher A Fuchs, Richard Jozsa, and Benjamin Schumacher. Noncommuting mixed states cannot be broadcast. Physical Review Letters, 76 (15): 2818, 1996. 10.1103/PhysRevLett.76.2818.
https://doi.org/10.1103/PhysRevLett.76.2818
[18] Kavan Modi, Aharon Brodutch, Hugo Cable, Tomasz Paterek, and Vlatko Vedral. The classical-quantum boundary for correlations: discord and related measures. Reviews of Modern Physics, 84 (4): 1655, 2012. 10.1103/RevModPhys.84.1655.
https://doi.org/10.1103/RevModPhys.84.1655.
[19] Michał Horodecki, Paweł Horodecki, Ryszard Horodecki, Jonathan Oppenheim, Aditi Sen, Ujjwal Sen, Barbara Synak-Radtke, et al. Local versus nonlocal information in quantum-information theory: formalism and phenomena. Physical Review A, 71 (6): 062307, 2005. 10.1103/PhysRevA.71.062307.
https://doi.org/10.1103/PhysRevA.71.062307.
[20] Kavan Modi, Tomasz Paterek, Wonmin Son, Vlatko Vedral, and Mark Williamson. Unified view of quantum and classical correlations. Physical Review Letters, 104 (8): 080501, 2010. 10.1103/PhysRevLett.104.080501.
https://doi.org/10.1103/PhysRevLett.104.080501
[21] Harold Ollivier and Wojciech H Zurek. Quantum discord: a measure of the quantumness of correlations. Physical Review Letters, 88 (1): 017901, 2001. 10.1103/PhysRevLett.88.017901.
https://doi.org/10.1103/PhysRevLett.88.017901
[22] Ashwin Nayak and Pranab Sen. Invertible quantum operations and perfect encryption of quantum states. Quantum Information & Computation, 7 (1): 103–110, 2007.
[23] P Oscar Boykin and Vwani Roychowdhury. Optimal encryption of quantum bits. Physical Review A, 67 (4): 042317, 2003. 10.1103/PhysRevA.67.042317.
https://doi.org/10.1103/PhysRevA.67.042317.
[24] Brian Hayes. Computing science: Randomness as a resource. American Scientist, 89 (4): 300–304, 2001. 10.1511/2001.4.300.
https://doi.org/10.1511/2001.4.300
[25] P Boes, H Wilming, R Gallego, and J Eisert. Catalytic quantum randomness. Physical Review X, 8 (4): 041016, 2018. 10.1103/PhysRevX.8.041016.
https://doi.org/10.1103/PhysRevX.8.041016
[26] Samuel L Braunstein and Arun K Pati. Quantum information cannot be completely hidden in correlations: implications for the black-hole information paradox. Physical review letters, 98 (8): 080502, 2007. 10.1103/PhysRevLett.98.080502.
https://doi.org/10.1103/PhysRevLett.98.080502.
[27] Hideki Imai, Jörn Müller-Quade, Anderson CA Nascimento, Pim Tuyls, and Andreas Winter. An information theoretical model for quantum secret sharing. Quantum Information & Computation, 5 (1): 69–80, 2003.
[28] Masahito Hayashi and Lin Chen. Weaker entanglement between two parties guarantees stronger entanglement with a third party. Physical Review A, 84 (1): 012325, 2011. 10.1103/PhysRevA.84.012325.
https://doi.org/10.1103/PhysRevA.84.012325
[29] Jörn Müller-Quade and Renato Renner. Composability in quantum cryptography. New Journal of Physics, 11 (8): 085006, 2009. 10.1088/1367-2630/11/8/085006.
https://doi.org/10.1088/1367-2630/11/8/085006.
[30] Dominique Unruh. Simulatable security for quantum protocols. arXiv preprint quant-ph/0409125, 2004. URL https://arxiv.org/abs/quant-ph/0409125.
arXiv:quant-ph/0409125
[31] Dominique Unruh. Universally composable quantum multi-party computation. In Annual International Conference on the Theory and Applications of Cryptographic Techniques, pages 486–505. Springer, 2010. 10.1007/978-3-642-13190-5_25.
https://doi.org/10.1007/978-3-642-13190-5_25
[32] M Lemus, P Yadav, P Mateus, N Paunković, and A Souto. On minimal assumptions to obtain a universally composable quantum bit commitment. In 2019 21st International Conference on Transparent Optical Networks (ICTON), pages 1–4. IEEE, 2019. 10.1109/ICTON.2019.8840386.
https://doi.org/10.1109/ICTON.2019.8840386
[33] Yu-Ao Chen, An-Ning Zhang, Zhi Zhao, Xiao-Qi Zhou, Chao-Yang Lu, Cheng-Zhi Peng, Tao Yang, and Jian-Wei Pan. Experimental quantum secret sharing and third-man quantum cryptography. Physical review letters, 95 (20): 200502, 2005. 10.1103/PhysRevLett.95.200502.
https://doi.org/10.1103/PhysRevLett.95.200502
[34] Jan Bogdanski, Nima Rafiei, and Mohamed Bourennane. Experimental quantum secret sharing using telecommunication fiber. Physical Review A, 78 (6): 062307, 2008. 10.1103/PhysRevA.78.062307.
https://doi.org/10.1103/PhysRevA.78.062307
[35] Wolfgang Tittel, Hugo Zbinden, and Nicolas Gisin. Experimental demonstration of quantum secret sharing. Physical Review A, 63 (4): 042301, 2001. 10.1038/ncomms6480.
https://doi.org/10.1038/ncomms6480.
[36] Zhan-Jun Zhang. Multiparty quantum secret sharing of secure direct communication. Physics Letters A, 342 (1-2): 60–66, 2005. 10.1016/j.physleta.2005.05.049.
https://doi.org/10.1016/j.physleta.2005.05.049
[37] Mark Adcock and Richard Cleve. A quantum goldreich-levin theorem with cryptographic applications. In Annual Symposium on Theoretical Aspects of Computer Science, pages 323–334. Springer, 2002. 10.1007/3-540-45841-7_26.
https://doi.org/10.1007/3-540-45841-7_26
[38] H Jeff Kimble. The quantum internet. Nature, 453 (7198): 1023, 2008. 10.1038/nature07127.
https://doi.org/10.1038/nature07127.
[39] Yonghae Lee, Ryuji Takagi, Hayata Yamasaki, Gerardo Adesso, and Soojoon Lee. State exchange with quantum side information. Physical Review Letters, 122 (1): 010502, 2019. 10.1103/PhysRevLett.122.010502.
https://doi.org/10.1103/PhysRevLett.122.010502
[40] Jonathan Oppenheim and Andreas Winter. Uncommon information (the cost of exchanging a quantum state). arXiv preprint quant-ph/0511082, 2005. URL https://arxiv.org/abs/quant-ph/0511082.
arXiv:quant-ph/0511082
[41] Andreas Elben, Benoı̂t Vermersch, Rick van Bijnen, Christian Kokail, Tiff Brydges, Christine Maier, Manoj K Joshi, Rainer Blatt, Christian F Roos, and Peter Zoller. Cross-platform verification of intermediate scale quantum devices. Physical Review Letters, 124 (1): 010504, 2020. 10.1103/PhysRevLett.124.010504.
https://doi.org/10.1103/PhysRevLett.124.010504
[42] Vladimir Bužek and Mark Hillery. Quantum copying: Beyond the no-cloning theorem. Physical Review A, 54 (3): 1844, 1996. 10.1103/PhysRevA.54.1844.
https://doi.org/10.1103/PhysRevA.54.1844
[43] Ashish V Thapliyal. Multipartite pure-state entanglement. Physical Review A, 59 (5): 3336, 1999. 10.1103/PhysRevA.59.3336.
https://doi.org/10.1103/PhysRevA.59.3336
[44] Animesh Datta. A condition for the nullity of quantum discord. arXiv preprint arXiv:1003.5256, 2010. URL https://arxiv.org/abs/1003.5256.
arXiv:1003.5256
Cited by
[1] Houquan Liu and Libo Yuan, "Unconditionally Secure Relativistic Quantum Qubit Commitment", Applied Sciences 11 23, 11416 (2021).
[2] Seok Hyung Lie, Seongjeon Choi, and Hyunseok Jeong, "Min-entropy as a resource for one-shot private state transfer, quantum masking, and state transition", Physical Review A 103 4, 042421 (2021).
[3] Seok Hyung Lie and Hyunseok Jeong, "Catalytic quantum randomness as a correlational resource", Physical Review Research 3 4, 043089 (2021).
[4] Seok Hyung Lie and Hyunseok Jeong, "Delocalized and dynamical catalytic randomness and information flow", Physical Review A 107 4, 042430 (2023).
[5] Siming Zhang, Minghao Wang, and Bin Zhou, "Quantifying the information distribution of quantum information masking", Quantum Information Processing 22 7, 284 (2023).
[6] Seok Hyung Lie and Hyunseok Jeong, "Randomness cost of masking quantum information and the information conservation law", Physical Review A 101 5, 052322 (2020).
[7] Seok Hyung Lie and M. S. Kim, "Quantum operations with the time axis in a superposed direction", arXiv:2306.02755, (2023).
[8] Mao-Sheng Li and Kavan Modi, "Probabilistic and approximate masking of quantum information", Physical Review A 102 2, 022418 (2020).
[9] Seok Hyung Lie and Hyunseok Jeong, "Randomness for quantum channels: Genericity of catalysis and quantum advantage of uniformness", Physical Review Research 3 1, 013218 (2021).
[10] Yuxing Du, Zhihua Guo, Huaixin Cao, Kanyuan Han, and Chuan Yang, "Masking Quantum Information Encoded in Pure and Mixed States", International Journal of Theoretical Physics 60 7, 2380 (2021).
[11] Seok Hyung Lie and Hyunsek Jeong, "Correlational Resource Theory of Catalytic Quantum Randomness under Conservation Law", arXiv:2104.00300, (2021).
[12] Seok Hyung Lie and Hyunseok Jeong, "Randomness for quantum channels:Genericity of catalysis and quantum advantage of uniformness", arXiv:2010.14795, (2020).
[13] Uzi Pereg, Christian Deppe, and Holger Boche, "Quantum Channel State Masking", arXiv:2006.05925, (2020).
[14] Seok Hyung Lie, Yong Siah Teo, and Hyunseok Jeong, "Hacking Quantum Networks: Extraction and Installation of Quantum Data", arXiv:2105.13823, (2021).
[15] A. G. Abdelwahab, S. A. Ghwail, Nasser Metwally, M. H. Mahran, and A. -S. F. Obada, "The concealment of accelerated information is possible", Quantum Information Processing 20 2, 71 (2021).
[16] Huaixin Cao, Yuxing Du, Zhihua Guo, Kanyuan Han, and Chuan Yan, "Masking quantum information into a tripartite syste", arXiv:2004.14540, (2020).
[17] Huaixin Cao, Yuxing Du, Zhihua Guo, Kanyuan Han, and Chuan Yang, "Masking quantum information encoded in pure and mixed states", arXiv:2004.14572, (2020).
The above citations are from Crossref's cited-by service (last updated successfully 2024-05-31 10:35:09) and SAO/NASA ADS (last updated successfully 2024-05-31 10:35:10). The list may be incomplete as not all publishers provide suitable and complete citation data.
This Paper is published in Quantum under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. Copyright remains with the original copyright holders such as the authors or their institutions.