Distributed Blockchain-Based Message Authentication Scheme for Connected Vehicles
Abstract
:1. Introduction
- We propose distributed message authentication scheme based on blockchain, the vehicles can authenticate the broadcast messages in distributed manner.
- In our system, we consider malicious nodes which exist in the network. The proposed scheme can prevent several attacks from the insiders.
- We provide formal verification for the proposed scheme and implement the proposed system which the mobility of vehicles is considered.
2. Related Works
3. Preliminary Knowledge
3.1. Blockchain
3.2. Consensus Algorithm
4. System Model
4.1. Network Model
4.2. Block Model
4.3. Adversary Model
4.4. System Goal
4.4.1. Strong Privacy Preservation
4.4.2. Message Integrity
4.4.3. Non-Repudiation
4.4.4. Traceability
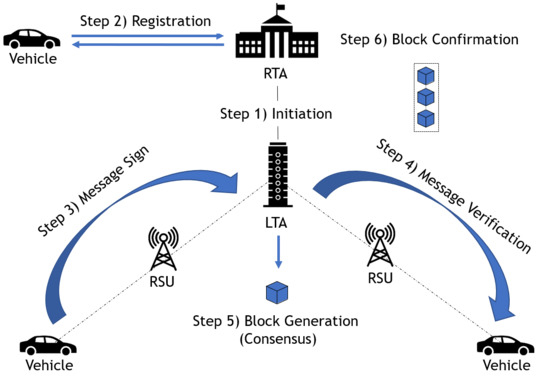
5. The Proposed Authentication Scheme
5.1. Initiation
5.2. Registration
5.3. Message Sign
5.4. Message Verification
5.5. Block Generation and Verification
5.6. Block Confirmation
6. Security and Overhead Analysis
6.1. Formal Verification
- I1.
- → :
- I2.
- → :
6.1.1. Assumptions and Goals
- A1.
- A2.
- A3.
- A4.
- A4.
- A5.
- A6.
- A7.
- A8.
- G1.
- G2.
- G3.
- G4.
6.1.2. Verification
6.2. Security Requirements
6.2.1. Strong Privacy Preservation
6.2.2. Message Integrity
6.2.3. Non-Repudiation
6.2.4. Traceability
6.3. Overhead Analysis
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| VANET | Vehicular ad-hoc Network |
| MANET | Mobile ad-hoc Network |
| V2V | Vehicle-to-Vehicle |
| V2I | Vehicle-to-Infrastructure |
| PoW | Proof of Work |
| PoS | Proof of Stake |
| PBFT | Practical Byzantine |
| RTA | Root Trusted Authority |
| LTA | Local Trusted Authority |
| RSU | Road Side Unit |
| OBU | On Board Unit |
| DSRC | Dedicated Short-Range Communication |
| ECDSA | Elliptic curve Digital Signature Algorithm |
| TESLA | Timed Efficient Stream Loss-tolerant Authentication |
| MAC | Message Authentication Code |
| BI | Biological Information |
| SNR | Signal-to-Noise Ratio |
| LFT | Loof-fault tolerance |
| BER | Bit Error Rate |
| TPS | Transaction Per Second |
References
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Hasrouny, H.; Samhat, A.E.; Bassil, C.; Laouiti, A. VANet security challenges and solutions: A survey. Veh. Commun. 2017, 7, 7–20. [Google Scholar] [CrossRef]
- Wang, M.; Liu, D.; Zhu, L.; Xu, Y.; Wang, F. LESPP: Lightweight and efficient strong privacy preserving authentication scheme for secure VANET communication. Computing 2016, 98, 685–708. [Google Scholar] [CrossRef]
- Perrig, A.; Canetti, R.; Tygar, J.D.; Song, D. The TESLA broadcast authentication protocol. Rsa Cryptobytes 2005, 5, 2–13. [Google Scholar]
- Wang, F.; Xu, Y.; Zhang, H.; Zhang, Y.; Zhu, L. 2FLIP: A two-factor lightweight privacy-preserving authentication scheme for VANET. IEEE Trans. Veh. Technol. 2016, 65, 896–911. [Google Scholar] [CrossRef]
- Jeon, S.; Noh, J.; Kim, J.; Cho, S. Strong privacy preserving authentication scheme for unmanned cars. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 12–14 January 2018; pp. 1–4. [Google Scholar]
- Manvi, S.S.; Tangade, S. A survey on authentication schemes in VANETs for secured communication. Veh. Commun. 2017, 9, 19–30. [Google Scholar] [CrossRef]
- Xu, C.; Huang, X.; Ma, M.; Bao, H. GAKAV: Group authentication and key agreement for LTE/LTE-A vehicular networks. In Proceedings of the 2017 IEEE 19th International Conference on High Performance Computing and Communications; IEEE 15th International Conference on Smart City; IEEE 3rd International Conference on Data Science and Systems (HPCC/SmartCity/DSS), Bangkok, Thailand, 18–20 December 2017; pp. 412–418. [Google Scholar]
- Jiang, S.; Zhu, X.; Wang, L. An efficient anonymous batch authentication scheme based on HMAC for VANETs. IEEE Trans. Intell. Transp. Syst. 2016, 17, 2193–2204. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, Y.; Chang, G. Efficient privacy-preserving dual authentication and key agreement scheme for secure V2V communications in an IoV paradigm. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2740–2749. [Google Scholar] [CrossRef]
- Liu, Y.; Guo, W.; Zhong, Q.; Yao, G. LVAP: Lightweight V2I authentication protocol using group communication in VANET s. Int. J. Commun. Syst. 2017, 30, e3317. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Nam, S.Y. Blockchain-based message dissemination in vanet. In Proceedings of the 2018 IEEE 3rd International Conference on Computing, Communication and Security (ICCCS), Kathmandu, Nepal, 25–27 October 2018; pp. 161–166. [Google Scholar]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. Blockchain: A distributed solution to automotive security and privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef] [Green Version]
- Kaur, K.; Garg, S.; Kaddoum, G.; Gagnon, F.; Ahmed, S.H. Blockchain-based Lightweight Authentication Mechanism for Vehicular Fog Infrastructure. arXiv 2019, arXiv:1904.01168. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 13 December 2019).
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Zyskind, G.; Nathan, O.; Pentland, A. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the 2015 IEEE Security and Privacy Workshops (SPW), San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar]
- Castro, M.; Liskov, B. Practical Byzantine fault tolerance. In Proceedings of the OSDI, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 3–16. [Google Scholar]
- Burrows, M.; Abadi, M.; Needham, R.M. A logic of authentication. Proc. R. Soc. Lond. A Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar] [CrossRef]
- Theloop. LFT: High Performance Lightweight Consensus Algorithm Supporting Byzantine Fault Tolerance. 2017. Available online: https://loopchain.files.wordpress.com/2017/07/lft-e18487e185a2e186a8e18489e185a5.pdf (accessed on 13 December 2019).
- Yin, M.; Malkhi, D.; Reiter, M.K.; Gueta, G.G.; Abraham, I. Hotstuff: Bft consensus with linearity and responsiveness. In Proceedings of the 2019 ACM Symposium on Principles of Distributed Computing, Toronto, ON, Canada, 29 July–2 August 2019; pp. 347–356. [Google Scholar]
- Kyösti, P.; Meinilä, J.; Hentila, L.; Zhao, X.; Jämsä, T.; Schneider, C.; Narandzi’c, M.; Milojevi’c, M.; Hong, A.; Ylitalo, J.; et al. IST-4-027756 WINNER II D1.1.2 V1.2 WINNER II Channel Models. 2007. Available online: http://www.ist-winner.org (accessed on 13 December 2019).
- Song, Y.S.; Choi, H.K. Analysis of V2V Broadcast Performance Limit for WAVE Communication Systems Using Two-Ray Path Loss Model. ETRI J. 2017, 39, 213–221. [Google Scholar] [CrossRef]
- 5GAA. An Assessment of LTE-V2X (PC5) and 802.11p Direct Communications Technologies for Improved Road Safety in the EU; Technical Report; 5G Automotive Association: Munich, Germany, 2017. [Google Scholar]
















| Notations | Description |
|---|---|
| The i-th vehicle | |
| Biological identity of | |
| A shared system key in the region of | |
| Public key of RTA | |
| Private key of RTA | |
| Public key of i-th vehicle | |
| Private key of i-th vehicle | |
| Hash value of previous block | |
| Message authentication code using | |
| Time stamp | |
| Hash function | |
| Encryped message X with | |
| Decryped message X with | |
| Concatenation function |
| Notation | Description |
|---|---|
| P believes X | |
| P sees X, or P holds X | |
| P had sent X | |
| P completely controls over X | |
| X is fresh | |
| P uses k as a secret key | |
| P cannot believe X | |
| If rule1 is true, then rule2 is true |
| Process | PBFT | LFT | HotStuff |
|---|---|---|---|
| Pre-prepare/Prepare | |||
| Prepare/Pre-commit | |||
| Commit | |||
| Reply | - | ||
| Total | |||
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Noh, J.; Jeon, S.; Cho, S. Distributed Blockchain-Based Message Authentication Scheme for Connected Vehicles. Electronics 2020, 9, 74. https://doi.org/10.3390/electronics9010074
Noh J, Jeon S, Cho S. Distributed Blockchain-Based Message Authentication Scheme for Connected Vehicles. Electronics. 2020; 9(1):74. https://doi.org/10.3390/electronics9010074
Chicago/Turabian StyleNoh, Jaewon, Sangil Jeon, and Sunghyun Cho. 2020. "Distributed Blockchain-Based Message Authentication Scheme for Connected Vehicles" Electronics 9, no. 1: 74. https://doi.org/10.3390/electronics9010074