1. Introduction
Internet of Things, or IoT, refers to the billions of physical objects around the world, wirelessly connected to the internet and each other, collecting and sharing data. Cheap processors and wireless networks can integrate anything into the IoT. Such a procedure adds digital intelligence to devices, by allowing them to communicate by themselves. The idea of adding sensor and intelligence to basic objects was discussed throughout the 1980s and 1990s, but apart from some early projects, such as an internet-connected vending machine, progress was slow, simply because the technology was not ready. The term Internet of Things (IoT) was coined in 1999 by Ashton [
1], a British technology pioneer, during a presentation he made at Procter & Gamble (P&G). “The IoT integrates the interconnectedness of human culture—our ‘things’—with the interconnectedness of our digital information system—‘the internet.’ That’s the IoT,” Ashton [
1]. The IoT aims to extend the benefits of the regular internet—constant connectivity, remote control ability, data sharing, and so on—to goods in the physical world [
2]. Its powerhouse is efficiency and innovation, enabling connectivity for everyone, everything and everywhere.
The IoT is the hot trend in the tech and business world. McLellan [
3] states that, “IoT is a fast-growing constellation of Internet-connected sensors attached to a wide variety of things”. There are numerous real-world applications of IoT such as smart homes, wearable devices, smart healthcare, smart buildings, smart city, smart farming, smart appliances and so on, ranging from consumer IoT and enterprise IoT to manufacturing and industrial IoT (IIoT). IoT applications span numerous verticals, including automotive, telecommunications, energy and more.
Some widely used technology acceptance theories may not be eligible or applicable for exploring individuals’ adoption of IoT applications. After the technology acceptance model (TAM) [
4] and its extensions were heavily criticized [
5,
6,
7], more antecedents were incorporated leading to the creation of Unified Theory of Acceptance and Use of Technology (UTAUT) and later to UTAUT2 models [
8].
Several studies have investigated the technical issues of implementing IoT technology [
9]. Hancke, Markantonakis and Mayes [
10] and Medaglia and Serbanati [
11] identified the security and privacy issues as the major challenges for user-oriented IoT applications. Mendez and Papapanagiotou [
12] explored IoT security. Uckelmann, Harrison and Michahelles [
13] explained the architecture of IoT. Guinard, Trifa, Mattern and Wilde [
14] outlined IoT best practices based on the web technologies and recommended prototypes using the web principles. Hyun Gi Hong [
15] found that factors, such as technical issues, personal characters, environmental factors, and cost factor affect the users’ adoption of IoT products. The original IoT aimed to increase supply chain efficiencies for organizations [
16], but more recently the potentials of IoT applications in social networking [
16], smart cities [
17] and m-health [
18] have been explored. Gao, Li and Luo [
19] showed that all factors from technology acceptance, health behavior, and privacy context perspectives would significantly affect consumers’ decision to adopt wearable technology in healthcare.
Potential discrepancies between IoT and the adoption process of other information technologies must be factored. It is unlikely that even complicated technology adoption models will fail to investigate IoT adoption [
8]. Though IoT’s overarching aim is to make an individual’s life easier and simpleminded, there may be other objections that could decelerate or even hinder its adoption process. Much prior research has focused on the design and usage of IoT technologies from the point of view of the organization or industry [
20], while little attention has been devoted to understanding the acceptance of IoT technologies from the perspective of individual consumers [
21]. According to Evanschitzky, Iyer, Pillai, Kenning and Schütte [
22], IoT technology needs further research in order to understand the factors that determine its acceptance.
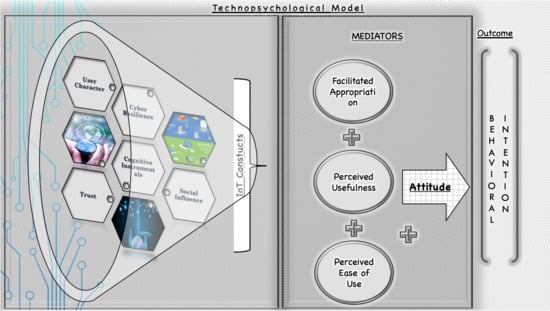
The common managerial and theoretical concerns are to know how individuals perceive IoT products and applications and how to accelerate adoption of them. It is an overriding requirement to try to explain the behavioral intention of individuals towards IoT without neglecting either technical or psychological attribute data. The main research question is “what factors define the behavioral intention to adopt IoT products and applications among individuals?” Thus, the research’s goal is to develop and test a model explaining the attitude and behavioral intention towards IoT products and applications by individuals, incorporating pull factors from two different information impact sources: technical and psychological.
Previous research has focused mainly on the driving factors behind IoT systems from the perspective of the enterprise [
23]. This research, however, differs because it focuses on IoT usage from the consumers’ perspective. Additionally, this study explores the factors that affect perceived usefulness, perceived ease of use and attitude in the context of IoT systems. Even though the previous studies have enriched our knowledge about factors influencing consumers’ intention to use information systems, they have not thoroughly examined the IoT systems.
The overall significance of this new IoT acceptance model (IoTAM) can create the prospect of instilling awareness for IoT dynamics. According to Prayoga and Abraham [
24], IoT acceptance is based on techno-psychological points of view and acceptance must be explained in terms of its affective, cognitive, behavioral, and technological elements. The findings will be used to advance knowledge in this newly introduced technology, by providing a collection of techno-psychological factors that define IoT acceptance and help create strategies for management and other stakeholders who are interested in the successful implementation of IoT.
4. Results
Table 2 exhibits the demographic characteristics of the 812 survey participants. Trying to fortify the egalitarianism of the sample, we tried to compose the sample of an approximately even number of participants in the context of gender and age. The survey respondents were generally well educated, the majority of them (47.3%) had a bachelor degree and 22% declared postgraduate degrees.
User mode was included in demographic characteristics to imprint participants’ personal perspective towards the decision to buy/use an IoT product or application. Generally, consumers, known as “early adopters” tend to embrace a new technological product immediately after its introduction to a market. On the other hand, “late adopters” tend to wait and monitor the adoption of new technological products before deciding whether to buy/use or not [
15]. According to Rogers [
40], consumers are divided to “Innovators”, “Early adopters”, “Early majority”, “Late majority” and “Laggards”. As stated above, in this research, “User mode” is divided in “Consumer-first mode”, incorporating the first three categories of consumers (50%), and “Carry-over effect mode” incorporating the last two categories of consumers (50%). The ratio of “Consumer-first mode” participants to “Carry-over effect mode” participants was about one.
Table 3 shows the descriptive statistics of the latent variables and the reliability coefficients of the tool. Testing the presence of normality is essential. If the data are not normally distributed, the validity and reliability of the results may be affected. Skewness and kurtosis measures were used to check whether data were normally distributed. Skewness value indicates the symmetry of the distribution [
53]. A negative skew indicates that the distribution is shifted to the right, whereas positive skew indicates a shift to the left. Kurtosis provides information about the height of the distribution. A positive kurtosis value indicates a peaked distribution, whereas a negative value indicates a flatter distribution. A good measure is obtained by dividing the skewness and kurtosis number by its standard error. The skewness ranged from 0.297 to 1.997 and kurtosis ranged from −0.341 to −1.137. Following Kline’s [
53] suggestion that the skew and kurtosis indices should be below 3.0 and 8.0, respectively, there were no severe problems in the data, which were considered fairly normal. As shown in
Table 3, each measured variable satisfied the assumption of the univariate normality. To analyze the relationship between measured variables, matrices of Pearson product moment correlation coefficients are used to measure the related index between variables.
Samples to be tested are based on the questions of every construct. As
Table 4 shows, each IoTAM’s Pearson correlation coefficient factors range from 0.006 to 0.829.
The overall fit of the model was assessed with the following goodness of fit indices representing absolute, comparative and parsimonious aspects of fit: Chi square—χ
2/degree of freedom [
53], goodness of fit (GFI): >0.90 [
53,
54], adjusted goodness of fit index (AGFI): >0.90 and root mean square error of approximation (RMSEA): <0.05 [
54]. The overall model fit statistics indicated an overall acceptable fit between data and the conceptual model, proving the adequacy of the model: GFI = 0.93, AGFI = 0.93, RMSEA = 0.04, x2(127) = 407.26,
p < 0.001.
Attitude interprets 60.4%, facilitated appropriation 21.6%, PU 50.8% and PEOU 51.7% of the variances. In total, the proposed model explains 71.8% of the behavioral intention variances, since the concerned R2 = 0.718.
Figure 2 presents the results of the structural model, including path coefficients and variances explained.
Table 5 exhibits standardized and unstandardized estimates of the model for each endogenous variable. The model included five exogenous variables: user character, cyber resilience, cognitive instrumental, social influence and trust. The only endogenous outcome in
Figure 2 was behavioral intention—the final outcome. The remaining variables, facilitated appropriation, perceived usefulness, perceived ease of use and attitude, were included as endogenous variables that mediate some part of the effect of antecedent variables on subsequent variables. Each of these endogenous variables are explained by other variables in the model (
Table 5). Results indicate that PEOU is a stronger predictor of attitude than PU, as well as that PEOU predicts PU stronger than facilitated appropriation (
Table 5).
Table 6 presents standardized effects of direct, indirect, and total effects of exogenous variables on endogenous variables. The direct effect of facilitated appropriation on PU and the indirect effect of user character on attitude are close to being statistically significant. Facilitated appropriation on behavioral intention is at the margin of statistical significance. All other direct, indirect and total effects were statistically significant, at
p < 0.05. Considering both direct and indirect effects of the variables on behavioral intention, the strongest total effect was from attitude followed by PU and PEOU. The path model revealed that there is a significant indirect effect of the variables on attitide and ultimately on behavioral inention.
5. Discussion of Findings
Figure 2 illustrates the outcome effect validation of the model. The overall fitness indices for the IoTAM indicated an acceptable fit. It showed that facilitated appropriation can be explained to the tune of 21.6% by user character and cyber resilience. It appears that PU can be explained to the tune of 50.8% by FA, CI, SI, trust and PEOU. PEOU can be explained to the tune of 51.7% by SI and trust. Attitude can be explained to the tune of 60.4% by PU and PEOU. BI can be explained to the tune of 71.8% by attitude. It also apparent that user character explains the strongest FA as the concerned path coefficient (β = 1.000) is strongest. FA was found to be the mediator in the series of constructs starting from user character, to FA, to PU, to attitude and finally to the outcome BI. This translates to an upswing of behavioral intention towards IoT products and applications. Since personal character influences attitude formation through facilitated appropriation, it is proven that the facilitation degree is affected more by consumers’ technology stance than their age.
Implicitly, it is presumed that consumers will have the technological knowledge and skills to deal with this “digital environment”. However, without any formal technology prerequisites, individuals are equipped with differing technological skills, stratified by prior experience. Beyond skills, individuals vary in their history with technology, which results in a range of technology identities, influencing their relationship with technology. Since technology expertise is not just a set of technical skills but a bundle of interactions, experiences and understandings of a new technology, knowledge about technology affects an individual’s technology stance [
55,
56] and according to our results, technology stance strongly influences facilitation. Therefore, it is concluded that previous knowledge about technology affects facilitation. Accordingly, Porter and Donthu [
57] proved that in the context of internet use particular beliefs about technology adoption rates differently affect consumers representing diverse segments of the population.
Trust explains PEOU stronger than social influence, since the concerned path coefficient (β = 0.411) is higher. It is observed that trust of consumers, as a focal construct in social psychology, strongly affects PU (trust → PEOU), probably because, especially in an online environment, consumers feel free to explore every aspect of the new IoT product or application only if they believe that there will be no privacy breaches and infringements. This trust stimulated “freedom of movements”, which probably countersigns a predisposed ease of use. Rooted in Wixom and Todd’s integrated framework [
58], this model showed how PU and PEOU mediate the effect of trust on individual intention towards IoT technologies. E-commerce research and evidence supports this proposal. Pavlou [
35] found that Internet consumer trust influenced both PU and PEOU. Additionally, Thatcher et al. [
59] found evidence that PEOU either fully or partially mediates the influence of trust in IoT on intention to explore.
Facilitated appropriation was measured by long-term orientation and flexibility. It had a statistically significant indirect effect on attitude through perceived usefulness. This translates to an upswing of behavioral intention towards IoT products and applications. It is proven that PU is significantly influenced by cognitive instrumentals leading to a more positive attitude perception towards IoT products and applications and therefore a higher behavioral intention.
Many of the researchers who have investigated consumers’ adoption of IoT technologies have incorporated factors that address the social aspect of adopting new technologies and found significant effects from social influence [
60]. In our research, social influence was found to influence PEOU and PU, which in turn influence attitude, which forms behavioral intention. IoT products and applications can be viewed both as fashion products that have aesthetic attributes and could offer consumers the chance to express their characters and values. Our results corroborate with previous research, for example, the significant effect of social influences on behavioral intention to use smartwatches was confirmed by Wu et al. [
61], signifying the significant effect of cultural appeal on customers’ attitude and intention to use. Trust was also found to significantly influence behavioral intention towards IoT products and applications. Specifically, it can be suggested that higher levels of trust lead to higher levels of PEOU.
Cyber resilience, cognitive instrumentals, social influence and trust, all with different significance rates, prove to be the predicting factors that form the IoTAM. User character and cyber resilience channel a mediating process of facilitated appropriation, where the positive interaction of perceived attitude leads to a positive behavioral intention towards IoT products and applications. The probative value of this result substantiates the fact that when consumers experience an IoT product or application, resilience, as a psychological factor, triggers their problem-solving ability and motivation to deal with emotional stress. To be resilient and adaptive to their new asset, they must find an adaptation solution. An adaptation solution is changing their current way of interacting with the product or applications. As a result, the more resilient consumers are more likely to be able to modify their behavior rapidly to adapt to the change. Concerning the factor of cognitive instrumentals, it is evidenced that potential consumers exhibit a positive PU towards IoT products and applications.
Attitudes are formed when consumers face the various behavioral patterns in their direct social network. Potential consumers of IoT products and applications are found to be more inclined to directly experience, in terms of enjoyment, the effect of social influence. Social influence is confirmed to lead to PEOU directly and to PU either directly or through the mediating process of PEOU, because a consumer who thinks of a system or an application as easy to use will tend to perceive it as being useful as well. The same flow on PEOU and PU is consistent with the last antecedent, trust. The mediating processes lead to positive attitude, which in turn is of paramount importance to the creation of behavioral intentions towards IoT products and applications.
PEOU and PU affect consumers’ initial intention to use and are the main determinants of the consumers’ attitudes. In our research, it is observed that PEOU (β = 0.301) explains attitude stronger than PU (β = 0.283), a result that contradicts past research results in the wider sphere of new technologies. For example, PU is found to be more useful than PEOU in predicting consumer attitudes to using mobile commerce [
62]. Additionally, according to Yang [
63], PU is a more powerful predictor of attitude towards a new technology than PEOU. This may be because in addition to the fact that PU is one of the fundamental antecedents of innovation usage, which is related to the utilitarian value that technology provides to customers [
26], it refers to the extent to which target consumers believe that using IT will create significant value for them [
64]. Moreover, in the context of a completely new concept, such as IoT, consumers may be more likely to adapt their behavior to the new technology if they perceive it to be easy to use, which refers to PEOU [
65] and less to the utilitarian value that it presumably provides.
PEOU (β = 0.392) is found to exert a significant influence on PU, and both PU and PEOU influence a consumer’s behavioral intention to use a new system. This complies with past research [
66,
67,
68,
69], concluding that PU and PEOU are useful as predictive tools.
This study enables us to draw several conclusions. The overall fitness indices for the IoTAM exhibit an acceptable fit of the model. All path coefficients were statistically significant. It was demonstrated that facilitated appropriation, PU and PEOU significantly influence consumers’ attitude and BI towards IoT products and applications. User character, cyber resilience, cognitive instrumentals, social influence and trust exhibited a significantly indirect effect on attitude and BIs, through the three main mediators. The IoTAM is proved to be a practical and serviceable model of investigating how different variables influence BI towards IoT products and applications.
6. Conclusions
The goal of this paper was to reveal the factors that define behavioral intention to adopt IoT products and applications among individuals. It was demonstrated that, even though TAM has proven its scientific value and applicability to many different disciplines, its application in the IoT area has not been validated yet. A model that includes both psychological and technical aspects was required to reflect and predict consumer behavioral intention. Remedying this inconsistency, this research provides a foundation for further research through developing and testing IoTAM. The predictive power and applicability of the factors forming IoTAM, all of them with different significance rates and relationship directions, were scientifically substantiated.
Perceived usefulness and perceived ease of use are found to strongly predict and form a positive attitude, which, due to their positive interaction, results in behavioral intention. The first two antecedents of user character and cyber resilience lead to a mediating process of facilitated appropriation towards technology acceptance. When individuals believe they could actually adopt, adapt or incorporate an artefact into working practice, they may seek for an IoT product or application to simplify their lives. Then, they move to assessing their usefulness, which, according to our results, is positive and strongly affects attitude formulation and ultimately behavioral intention. The third antecedent of cognitive instrumentals relates to the mental representation that individuals use to decide whether to adopt a technology or not. Therefore, the positive relationship between cognitive instrumentals and perceived usefulness indicates that individuals exhibit positive cognitions for IoT products and applications, forming a positive perceived usefulness judgment, which eventually leads to a positive attitude and behavioral intention. The fourth antecedent of social influence is found to have the distinctive feature of either having a direct positive influence or an indirect positive influence, through perceived ease of use, on perceived usefulness. This double path is in accordance with the research of Venkatesh and Davis [
3], who found that if an individual perceives any technological product/system as easy to use and free of effort, he or she perceives that product/system is more useful. The fifth antecedent of trust shares the same distinctive feature of the double path to perceived usefulness as social influence. It is found that in both paths—indirectly through perceived ease of use and directly to perceived usefulness—trust positively affects perceived usefulness, which in turn strongly predicts attitude formulation, leading to behavioral intention.
7. Implications for Theory and Practice
Acceptance of a new technology may be influenced by its merits, but it can also be affected by users’ psychological barriers, such as the reluctance to change the status quo [
70] and the fear of losing control [
71]. Impacts of psychological barriers on consumers’ attitudes and behaviors towards IoT products and applications are currently under-researched. To describe behavioral intention towards IoT products and applications, we developed the IoTAM. The integrative psychological-technological viewpoint implies that managers should consider these key factors simultaneously.
The emergence of IoT products and applications has two key consequences. The first is that things will be transformed into ‘‘smart things’’, capable of enhancing existing goods, as well as creating new ones. The second is that the large network organization of these smart things will create a wired IoT infrastructure, whose anatomical layers could imitate biological ones. IoT is not just a new technology, but also a completely new way for people to interact with their “brick-and- mortar” environments.
This study has both theoretical and practical implications. The strongest theoretical contribution is that theorizes the factors influencing consumers’ behavioral intention towards IoT products and applications from an integrated perspective, including technology perceptions (e.g., perceived usefulness), social context variables (e.g., social influence) and consumers’ individual psychological characteristics (e.g., long term orientation). It successfully extends several technology acceptance models, e.g., TAM, in the IoT context, which is extremely different from the context of other information systems. Internet of Things (IoT) helps other information systems to extend provided services while providing flexibility and reachability for things from anywhere to anyone worldwide [
72]. What makes the IoT different is that it can function without human-to-human or human-to-computer interaction, as well as utilizing unique identifiers to share information in a network [
35]. The IoT system results in the outreach from objects to other objects, and this is the basic characteristic that distinguish IoT systems from traditional information systems.
This IoTAM contributes to current knowledge pertaining to consumer behavior and marketing in two ways. First, theoretical contributions on the factors of consumer behavior towards IoT products and applications is largely neglected in current consumer behavioral and information technology literature. This study tries to fill the literature gap, while calling for further studies, by identifying user mode, social influence, flexibility, long term orientation, cognitive instrumentals and cyber resilience as the additional antecedents of consumer behavioral intention towards IoT products and applications. As a result, the model integrated with technical and psychological features instills an explanation for consumers’ behavioral intention, upgrades current knowledge and provides a solid base for examining multirooted models for the acceptance of newly formed technologies.
Accordingly, this research’s contribution for practitioners is through its provision of a grassroot template for improving their goods, in order to have a chance of targeting better current customers or attracting new ones. It was substantiated that consumers are not only interested in a useful and easy-to-use IoT product or application, but also expect to fulfil other emotions in order for a positive attitude to be created. Therefore, IoT service providers are advised to offer potential customers products and services that are flexible, challenging, dynamic, beneficial, prestigious, trustworthy and futuristic. With respect to usefulness, IoT practitioners are expected to improve the quality of life and daily performance of consumers through designing IoT products and applications that require the minimum possible effort to accomplish tasks. Furthermore, they need to identify consumers’ user modes and stimulate their usage of IoT products and services, so that they can be used as axes, enhancing wider and faster diffusion.
The growth of the internet has led to a different marketing landscape in which consumers actively seek out the opinions of other consumers before making a purchase [
73]. Drawn upon the results, marketers should pay attention to the role of social influence on IoT consumer acceptance, given that it is still new. Social influence can play an important role in the diffusion of IoT technologies. Behavioral science suggests that individuals dislike disturbances to social norms and often act in the way that most people do.
Despite the research’s results about the variety of sectors that influence customer behavior towards IoT, little is known about the long-run effects of IoT marketing tactics, which is critically important to study in order to understand the strategic marketing implications of IoT technology. Without better knowledge of long-run and competitive outcomes, it will be difficult to address the more basic strategic questions of what markets get served and by whom. If marketers and practitioners want consumers to relate to IoT products and applications, they must find an elaborate way of enticing them to try the products. They need to be visceral and tap into to the most powerful parts of the human psyche.
Integrated marketing communication strategies must be composed, facilitating consumers to accept IoT products and applications by creating interactive marketing tools that will target mostly emotion rather than logic. In an interactive world where physical products are no longer the king, these strategies must highlight the profound benefits of IoT products and applications to reduce the psychological barrier. It is obvious that if practitioners want to speed up the pace of the adoption process, they should make the most of the psychology of both creators and consumers of IoT products and applications, rather than rely on only the technical details of what the products are designed to do. In contrast to the conventional wisdom that marketers should mostly emphasize the novelty of new products and congruent with the results of Faraji-Rad et al. [
74], this tactic may be specifically problematic among consumer segments that are high in desire for control, which can be identified through aggregate level proxy measures.
By exploring what values trigger consumers to use social IoT products and applications and how these values affect consumers’ attitudes toward behavioral intentions, this study helps us understand a beneficial marketing strategy in both theory and practice. It is time to broaden the horizons of consumer behavior because currently used human-centric perspectives diminish the prospect of formulating prominent questions for the future of consumer behavior science.