An Enhanced Three-Factor User Authentication Scheme Using Elliptic Curve Cryptosystem for Wireless Sensor Networks
Abstract
:1. Introduction
1.1. Related Works
1.2. Motivations and Contributions
- We depict the system architecture, adversary model and security requirements of wireless sensor networks. Though these factors are the basis of the authentication scheme, researchers usually ignore them.
- We demonstrate that: (1) Jung et al.’s scheme cannot resist against offline password guessing attack, impersonation attack, and fails to achieve user anonymity and forward secrecy, etc.; (2) Park et al.’s scheme suffers from offline password guessing attack, and no user anonymity. Furthermore, we explain the inherent reason for these attacks.
- We propose an improved scheme with various desirable attributes, and prove its security via BAN logic and heuristic analysis. Then, we compare our scheme with other related schemes. The results show the great advantage of our scheme.
1.3. Organization of the Paper
2. Preliminaries
2.1. Computational Problems
- Elliptic curve discrete logarithm problem: given (P, ), it is impossible to compute within polynomial time.
- Elliptic curve computational Diffie–Hellman problem: given (, ), it is impossible to compute within polynomial time.
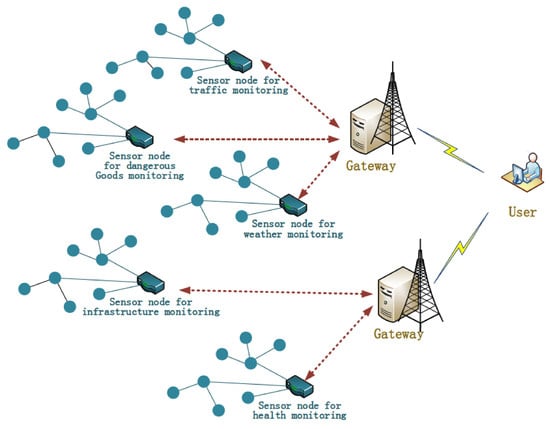
2.2. System Architecture
2.3. Adversary Models
- can get the past session keys [30].
2.4. Security Requirements
- S1
- S2
- User anonymity. It is a privacy protection requirement for individual users, not directly related to system security. Many systems have such a requirement including distributed system [36]. While the privacy protection in wireless sensor networks is more severe, since the information among sensor nodes (usually unreliable) is transmitted in a way of broadcasting. Protecting user anonymity is to stop from computing the user’s identity or linking the transcript to a same user. Note that such a requirement is not applied to the gateway, but to sensor nodes for they are untrusted.
- S3
- Key agreement. It is also an essential requirement in most authentication schemes. The session key is used to encrypt the further communications to achieve confidentiality.
- S4
- Forward secrecy. It is for the final collapse of the whole system, and it requires that the previous communications will be secure, even the system collapses (usually refers to the adversary that owns the long-term key of the system).
- S5
- User friendly. It is an additional requirement to improve the user experience with the development of the network. A user friendly scheme usually includes: let the user select the password freely, and change it locally [30]; when finds the smart card insecure, let he/she revoke it and re-register to the system with original identity.
- S6
- No stolen-verifier attack. It is a requirement related to the security of the whole system (so as the following attacks), which requires that the verifier table does not expose any sensitive information for to impersonate the participants or learn/control the session key.
- S7
- No insider attack. It requires that the participants cannot get any sensitive information, which may provoke an attack.
- S8
- No dictionary attack. It requires that cannot conduct a brute force attack.
- S9
- No replay attack. It stops from conducting an attack via replaying the history message, which requires that the participants can check the freshness and validity of the received message.
- S10
- No parallel session attack. This requirement is a bit similar to the replay attack, but it considers a condition where conducts an attack via initiating multi-session simultaneously.
- S11
- No de-synchronization attack. The synchronization attack in wireless sensor networks is more destructive than that in traditional networks, since a gateway may connect even hundreds of sensor nodes. It requires that the parameters among corresponding participants are consistent.
- S12
- No impersonation attack. It is a very important requirement in authentication, which requires that the outside adversary (inside adversary has been considered in insider attack) will not be able to impersonate any participants. A scheme resistant to impersonation attack requires that the participants verify whether the corresponding communication party is a counterfeit one. Note that: the occasion where performs a user impersonation attack using the password from a dictionary attack is not included—such an attack belongs to dictionary attack.
- S13
- No known key attack. It is an attack related to the session key, which requires , who knows that the current session key cannot compute the keys in others.
3. Cryptanalysis of Jung et al.’s Scheme
3.1. A Brief Review of Jung et al.’s Scheme
3.1.1. Registration Phase
- : , where = , = and u is a random number chosen by the user .
- : a smart card containing , where = , = , = , = .
- stores in the smart card, where = .
- : .
- : = .
- stores as a secret key.
3.1.2. Login Phase and Verification Phase
- : . inputs the and , and his biometrics ; then, the smart card computes:Finally, the card checks ?= . If it is equal, the card computes = and = , and sends to . Otherwise, it ends the session.
- : . first checks the freshness of , then computes:and further tests ?= . If the condition is not satisfied, rejects the request. Otherwise, it computes = , = , = and = , and sends to .
- : . first checks , and computes:If = , further computes = , = , and sends to the . Otherwise, it exits the session.
- : . first checks , and computes:If = , further computes = , = , and sends to the . Otherwise, it exits the session.
- first checks , and computes = , = and = . If = , believes the legitimacy of and the authentication phase ends successfully. Otherwise, the authentication fails.
3.2. Security Flaws in Jung et al.’s Scheme
3.2.1. Offline Dictionary Attack
- Guesses the value of to be and to be from the dictionary space and , respectively. In fact, according to Wang et al. [28], once an adversary picks the victim’s () smart card, it is easy to learn the corresponding identity of the user .
- Computes = .
- Computes u = , where is from the smart card.
- Computes = .
- Computes = , where is from the card.
- Computes = , where is from the public channel.
- Verifies the correctness of and by checking if the computed is equal to the intercepted .
- Repeats Steps 1–7 of this procedure until the correct value of and is found.
- Step 6. Computes = , where is from the card.
- Step 7. Verifies the correctness of and by checking if ?= .
- Step 8. Repeats Steps 1–7 of this procedure until the correct value of and is found.
3.2.2. Impersonation Attack
- Computes u = , where is from the smart card.
- Computes = .
- Computes = .
- Computes = , where is from the card.
- Computes x = , where is from the card.
3.2.3. User Anonymity
3.2.4. Forward Secrecy
- Computes = .
- Computes R = , where is from the open channel.
- Computes = , where is from the open channel.
4. Cryptanalysis of Park et al.’s Scheme
4.1. A Brief Review of Park et al.’s Scheme
4.1.1. Registration Phase
- : , where = , = .
- : a smart card containing , where = , = , = , = , = . Furthermore, stores in database, and is a random number, is initialized to NULL.
- inputs into the smart card. Note that, in Park et al.’s scheme [26], this step is not mentioned. But, according to the scheme, this step is necessary. We speculate it is missed.
4.1.2. Login Phase and Verification Phase
- : . inputs the and , and the biometrics , and then the smart card computes:If == , the card selects a random number , and computes = , = , = and = , and sends to . Otherwise, it ends the session.
- : . first checks , then gets and computes:If ≠, rejects the request. Otherwise, it computes = , = , and sends to .
- : . first checks , and if ≠, rejects it. Otherwise, chooses and computes:and sends to the .
- : . first checks , and computes = , = , if == , further computes:and updates as , then sends to the . Otherwise, it exits the session.
- checks , and computes = , if == , computes = , and updates as . Otherwise, it exits the session.
4.2. Security Flaws in Park et al.’s Scheme
4.2.1. Offline Dictionary Attack
- Guesses to be and to be .
- Computes = , where is from the smart card.
- Computes = .
- Computes = .
- Computes = , where is from the card, and are from the channel.
- Verifies the correctness of and by checking whether == .
- Repeats Step 1–7 of this procedure until the correct value of and is found.
4.2.2. User Anonymity
5. Proposed Scheme
- based on Wang et al. [3,41], we apply a public key algorithm for resisting against offline dictionary attack via the verification from the open channel. In such an attack, as we analyzed above, the key solution is about the way to construct the verification parameter between the user and the gateway node. Once the verification parameter consists of a “challenge” that is deployed a public key algorithm, a trap door will be built. Therefore only the one who owns the corresponding secret key can compute the correct “challenge” (i.e., X in our scheme). In Park et al.’s scheme, though a public key algorithm is deployed, it is not used to construct a “challenge” for authentication. More specifically, all the parameters in the verification (=) can be computed with the static or open knowledge in the user side and the open channel, so can compute all parameters (,,,) with guessed password and then use to verify the guessed value. While, in our new scheme, a “challenge” X is built. Besides the static or open knowledge on the user side, has to know the dynamic or the long-term key to compute X, and thus fails to conduct such an attack;
- as introduced in Section 3.2.1, we use “honeywords” + “fuzzy-verifiers” to resist against offline dictionary attack via verification from the smart card [30,42];
- we do not protect user anonymity via updating parameters as Park et al., but deploy a dynamic identity technique via a public key algorithm [3].
5.1. Registration Phase
- : , where = , = .
- : a smart card containing , where = ( is a random number), = , = mod , Y = . Furthermore, stores in database, and is supposed to count the number of failing in user login phase and it is initialized to NULL. Once its value is bigger than the predetermined threshold, the corresponding smart card will be discarded till the user re-registers.
- inputs into the smart card.
5.2. Login Phase and Verification Phase
- : . inputs his/her identity , password , and biometrics ; then, the smart card computes:If == , the card accepts the user, and selects a random number , computes:and then sends as a login request to . Otherwise, it ends the session.
- : . first checks the freshness of , computes:and then finds and via . If the preset value (for example 10), the thinks this smart card has been suspended and rejects the request. Otherwise, computes = , = . If ≠, rejects the request and sets = . Once is bigger than the preset value, the corresponding smart card is suspended. Otherwise, it computes:and sends to to conveys ’s request.
- : . first checks the valid of , and computes = . If ≠, does not believe and rejects the session. Otherwise, chooses and computes:and sends to .
- : . first checks . Then, it computes = , and if == , further computes = , and then sends to to transmit ’s responds. Otherwise, it exits the session.
- first checks , and if == , authenticates the , and computes = to finish the authentication successfully. Otherwise, the authentication fails.
5.3. Password Change Phase
- inputs , and new password .
- The card computes:If , the card does not permit to change the password. Otherwise, it further computes:and finally replaces with .
5.4. Revocation Phase
- firstly get authenticated by the card as the way to the step 1 in Section 5.2.
- : . As described in Section 5.2, the smart card computes ,, and sends to the gateway.
- After receiving the revocation request from , first verifies . If authenticates successfully, it sets to a big number, which is bigger than the preset value. Then, the smart card will be revoked, and nobody can login to the system with the card unless re-register. Otherwise, rejects the request.
5.5. Re-Register Phase
- : .
- Firstly, looks for from , checks whether the preset value. If so, believes the card is suspended, then performs the corresponding steps in Section 5.1.
6. Security Analysis
6.1. Formal Analysis Based on BAN Logic
- Goal 1: .
- Goal 2: .
- Goal 3: .
- Goal 4: .
- : : .
- : : .
- : : .
- : : .
- : .
- : .
- : .
- : .
- : .
- : .
- : .
- : .
- : .
- : .
6.2. Informal Analysis
6.2.1. Mutual Authentication
6.2.2. User Anonymity
6.2.3. Forward Secrecy
6.2.4. Offline Dictionary Attack
6.2.5. Privileged Insider Attack
6.2.6. Verifier-Stolen Attack
6.2.7. Replay Attack
7. Performance Analysis
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Pecori, R.; Veltri, L. 3AKEP: Triple-authenticated key exchange protocol for peer-to-peer VoIP applications. Comput. Commun. 2016, 85, 28–40. [Google Scholar]
- Pecori, R. A comparison analysis of trust-adaptive approaches to deliver signed public keys in P2P systems. In Proceedings of the 7th International Conference on New Technologies, Mobility and Security (NTMS), Paris, France, 27–29 July 2015. [Google Scholar]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of “two-factor user authentication in wireless sensor networks”. Sensors 2010, 10, 2450–2459. [Google Scholar] [PubMed]
- Kumar, P.; Choudhury, J.A.; Sain, M.; Lee, S.G.; Lee, H.J. RUASN: A robust user authentication framework for wireless sensor networks. Sensors 2011, 11, 5020–5046. [Google Scholar] [CrossRef] [PubMed]
- Ling, C.; Lee, C.; Yang, C.; Hwang, M. A secure and efficient one-time password authentication scheme for WSN. Int. J. Netw. Secur. 2017, 19, 177–181. [Google Scholar]
- Chen, C.T.; Lee, C.C. A two-factor authentication scheme with anonymity for multi-server environments. Secur. Commun. Netw. 2013, 8, 1608–1625. [Google Scholar]
- Das, M.L. Two-factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar]
- Lee, C.; Li, C.; Chen, S. Two attacks on a two-factor user authentication in wireless sensor networks. Parallel Process. Lett. 2011, 21, 21–26. [Google Scholar] [CrossRef]
- Kumar, P.; Gurtov, A.; Ylianttila, M.; Lee, S.; Lee, H. A strong authentication scheme with user privacy for wireless sensor networks. ETRI J. 2013, 35, 889–899. [Google Scholar] [CrossRef]
- Sun, D.; Li, J.; Feng, Z.; Cao, Z.; Xu, G. On the security and improvement of a two-factor user authentication scheme in wireless sensor networks. Pers. Ubiquitous Comput. 2013, 17, 895–905. [Google Scholar] [CrossRef]
- Fan, R.; He, D.P.X.P.L. An efficient and dos-resistant user authentication scheme for two-tiered wireless sensor networks. J. Zhejiang Univ. Sci. C 2011, 12, 550–560. [Google Scholar] [CrossRef]
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014, 20, 1–15. [Google Scholar] [CrossRef]
- Xue, K.; Ma, C.; Hong, P.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Li, C.T.; Weng, C.Y.; Lee, C.C. An advanced temporal credential-based security scheme with mutual authentication and key agreement for wireless sensor networks. Sensors 2013, 13, 9589–9603. [Google Scholar] [CrossRef] [PubMed]
- Li, C.T.; Lee, C.C.; Lee, C.W. An improved tTwo-factor user authentication protocol for wireless sensor networks using elliptic curve cryptography. Sens. Lett. 2013, 11, 958–965. [Google Scholar] [CrossRef]
- Hsiu-Lien, Y.; Chen, T.H.; Liu, P.C.; Tai-Hoo, K.; Wei, H.W. A secured authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar]
- Choi, Y.; Lee, D.; Kim, J.; Nam, J.; Won, D. Security enhanced user authentication protocol for wireless sensor networks using elliptic curves cryptography. Sensors 2014, 14, 10081–10106. [Google Scholar] [CrossRef] [PubMed]
- Shi, W.; Gong, P. A new user authentication protocol for wireless sensor networks using elliptic curves cryptography. Int. J. Distrib. Sens. Netw. 2013, 2013, 51–59. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An efficient two-factor user authentication scheme with unlinkability for wireless sensor networks. Peer-to-Peer Netw. Appl. 2015, 8, 1070–1081. [Google Scholar] [CrossRef]
- Wu, F.; Xu, L.; Kumari, S.; Li, X. A new and secure authentication scheme for wireless sensor networks with formal proof. Peer-to-Peer Netw. Appl. 2017, 10, 16–30. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. Int. J. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- Chang, I.; Lee, T.; Lin, T.; Liu, C. Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Jung, J.; Moon, J.; Lee, D.; Won, D. Efficient and security enhanced anonymous authentication with key agreement scheme in wireless sensor networks. Sensors 2017, 17. [Google Scholar] [CrossRef] [PubMed]
- Park, Y.; Park, Y. Three-factor user authentication and key agreement using elliptic curve cryptosystem in wireless sensor networks. Sensors 2016, 16, 2123. [Google Scholar] [CrossRef] [PubMed]
- Huang, X.; Xiang, Y.; Bertino, E.; Zhou, J.; Xu, L. Robust multi-factor authentication for fragile communications. IEEE Trans. Depend. Secur. Comput. 2013, 11, 568–581. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Depend. Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Two birds with one stone: Two-factor authentication with security beyond conventional bound. IEEE Trans. Depend. Secur. Comput. 2016. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Choo, K.K.R.; Shen, J. Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Futur. Gener. Comput. Syst. 2017, 68, 320–330. [Google Scholar] [CrossRef]
- He, D.; Wang, D. Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst. J. 2015, 9, 816–823. [Google Scholar] [CrossRef]
- Jiang, Q.; Chen, Z.; Li, B.; Shen, J.; Yang, L.; Ma, J. Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems. J. Ambient Intell. Humaniz. Comput. 2017. [Google Scholar] [CrossRef]
- Lee, C.C.; Chen, C.T.; Wu, P.H.; Chen, T.Y. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–56. [Google Scholar] [CrossRef]
- He, D.; Zeadally, S.; Kummar, N.; Wu, W. Efficient and anonymous mobile user authentication protocol using self-certified public key cryptography for multi-server architectures. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2052–2064. [Google Scholar] [CrossRef]
- Wang, C.; Wang, D.; Xu, G.; Guo, Y. A lightweight password-based authentication protocol using smart card. Int. J. Commun. Syst. 2017. [Google Scholar] [CrossRef]
- Wang, D.; Cheng, H.; Wang, P.; Huang, X.; Jian, G. Zipf’s law in passwords. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2776–2791. [Google Scholar] [CrossRef]
- Kumari, S.; Khan, M.K.; Li, X.; Wu, F. Design of a user anonymous password authentication scheme without smart card. Int. J. Commun. Syst. 2016, 29, 441–458. [Google Scholar] [CrossRef]
- Li, X.; Qiu, W.; Zheng, D.; Chen, K.; Li, J. Anonymity enhancement on robust and efficient password-authenticated key agreement using smart cards. IEEE Trans. Ind. Electron. 2010, 57, 793–800. [Google Scholar]
- Li, X.; Xiong, Y.; Ma, J.; Wang, W. An enhanced and security dynamic identity based authentication protocol for multi-server architecture using smart cards. J. Netw. Comput. Appl. 2012, 35, 763–769. [Google Scholar] [CrossRef]
- Ma1, C.; Wang, D.; Zhao, S. Security flaws in two improved remote user authentication schemes using smart cards. Int. J. Commun. Syst. 2012, 27, 2215–2227. [Google Scholar]
- Wang, C.; Xu, G. Cryptanalysis of three password-based remote user authentication schemes with non-tamper-resistant smart card. Secur. Commun. Netw. 2017. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R. A logic of authentication. IEEE Trans. Comput. 1990, 8, 18–36. [Google Scholar] [CrossRef]
- Amin, R.; Islam, S.H.; Biswas, G.P.; Khan, M.K.; Leng, L.; Kumar, N. Design of an anonymity-preserving three-factor authenticated key exchange protocol for wireless sensor networks. Comput. Netw. 2016, 101, 42–62. [Google Scholar] [CrossRef]


| Symbol | Description |
|---|---|
| th user | |
| the gateway node | |
| th sensor node | |
| malicious attacker | |
| identity of user | |
| password of user | |
| biometrics of user | |
| the shared secret key between and | |
| the secret key of remote server | |
| ⊕ | the bitwise exclusive OR (XOR) operation |
| ∥ | the string concatenation operation |
| collision free one-way hash function to the biometrics | |
| collision free one-way hash function | |
| one part of fuzzy extraction function, output a biometric key and a helper string | |
| one part of fuzzy extraction function, output the biometric key in | |
| a insecure channel | |
| a secure channel |
| P believes X, i.e., the principal P believes the statement X is true. | |
| P sees X, i.e., the principal P receives a message that contains X. | |
| P has jurisdiction over X, i.e., the principal P can generate or compute X. | |
| P said X, i.e., the principal P has sent a message containing X. | |
| X is fresh, i.e., X is sent in a message only at the current run of the protocol, it is usually a timestamp or a random number. | |
| K is the shared key for P and Q. | |
| Y is the secret known only to P and Q or some principals trusted by them. | |
| X combined with Y, and Y is usually a secret. | |
| X encrypted with K. | |
| or | : the message-meaning rule. |
| This rule will be used in the proving process. | |
| : the nonce-verification rule. | |
| This rule will be used in the proving process. | |
| : the jurisdiction rule. | |
| This rule will be used in the proving process. | |
| : the freshness-conjuncatenation rule. | |
| This rule will be used in the proving process. |
| Computation Overhead | Communication Cost | The Proposed Evaluation Criteria | |||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Login (ms) | Auth. (ms) | Login | Auth. | S1 | S2 | S3 | S4 | S5 | S6 | S7 | S8 | S9 | S10 | S11 | S12 | S13 | |||
| Amin et al. [44] | 768 bits | 1536 bits | √ | × | √ | × | √ | √ | √ | × | √ | √ | √ | √ | √ | ||||
| Jiang et al. [29] | + | + | 1408 bits | 1280 bits | √ | × | √ | × | √ | √ | √ | × | √ | √ | √ | √ | √ | ||
| Jung et al. [25] | 512 bits | 1024 bits | √ | × | √ | × | × | √ | √ | × | √ | √ | √ | × | √ | ||||
| Park et al. [26] | + | + | 1536 bits | 4096bits | √ | × | √ | √ | × | × | √ | × | √ | √ | √ | √ | √ | ||
| Our scheme | + | + | 1408 bits | 3968 bits | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | √ | ||
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, C.; Xu, G.; Sun, J. An Enhanced Three-Factor User Authentication Scheme Using Elliptic Curve Cryptosystem for Wireless Sensor Networks. Sensors 2017, 17, 2946. https://doi.org/10.3390/s17122946
Wang C, Xu G, Sun J. An Enhanced Three-Factor User Authentication Scheme Using Elliptic Curve Cryptosystem for Wireless Sensor Networks. Sensors. 2017; 17(12):2946. https://doi.org/10.3390/s17122946
Chicago/Turabian StyleWang, Chenyu, Guoai Xu, and Jing Sun. 2017. "An Enhanced Three-Factor User Authentication Scheme Using Elliptic Curve Cryptosystem for Wireless Sensor Networks" Sensors 17, no. 12: 2946. https://doi.org/10.3390/s17122946