Crossref Citations
This article has been cited by the following publications. This list is generated based on data provided by
Crossref.
Shparlinski, Igor E.
and
Winterhof, Arne
2005.
On the linear complexity of bounded integer sequences over different moduli.
Information Processing Letters,
Vol. 96,
Issue. 5,
p.
175.
Zhixiong, Chen
Ning, Zhang
and
Guozhen, Xiao
2006.
Binary sequences from a pair of elliptic curves.
Wuhan University Journal of Natural Sciences,
Vol. 11,
Issue. 6,
p.
1511.
Murty, Ram
and
Shparlinski, Igor
2006.
Topics in Geometry, Coding Theory and Cryptography.
Vol. 6,
Issue. ,
p.
167.
Chen, Zhixiong
Li, Shengqiang
and
Xiao, Guozhen
2006.
Sequences and Their Applications – SETA 2006.
Vol. 4086,
Issue. ,
p.
285.
Topuzoğlu, Alev
and
Winterhof, Arne
2006.
Topics in Geometry, Coding Theory and Cryptography.
Vol. 6,
Issue. ,
p.
135.
Brumley, Billy Bob
and
Järvinen, Kimmo
2007.
Selected Areas in Cryptography.
Vol. 4876,
Issue. ,
p.
126.
Gutierrez, Jaime
and
Ibeas, Álvar
2007.
Inferring sequences produced by a linear congruential generator on elliptic curves missing high-order bits.
Designs, Codes and Cryptography,
Vol. 45,
Issue. 2,
p.
199.
Farashahi, Reza Rezaeian
and
Pellikaan, Ruud
2007.
Arithmetic of Finite Fields.
Vol. 4547,
Issue. ,
p.
219.
Chen, Zhixiong
2008.
Elliptic curve analogue of Legendre sequences.
Monatshefte für Mathematik,
Vol. 154,
Issue. 1,
p.
1.
Farashahi, Reza Rezaeian
2008.
Information Security and Privacy.
Vol. 5107,
Issue. ,
p.
447.
Farashahi, Reza Rezaeian
Pellikaan, Ruud
and
Sidorenko, Andrey
2008.
Extractors for binary elliptic curves.
Designs, Codes and Cryptography,
Vol. 49,
Issue. 1-3,
p.
171.
Chen, Zhixiong
Zhang, Ning
and
Xiao, Guozhen
2008.
Information Security and Cryptology.
Vol. 4990,
Issue. ,
p.
231.
Deepthi, P.P.
and
Sathidevi, P.S.
2009.
New stream ciphers based on elliptic curve point multiplication.
Computer Communications,
Vol. 32,
Issue. 1,
p.
25.
Chen, Zhixiong
and
Wu, Chenhuang
2009.
A Construction of Binary Sequences from Elliptic Curves.
p.
137.
El-Mahassni, Edwin
2010.
EXPONENTIAL SUMS FOR NONLINEAR RECURRING SEQUENCES IN RESIDUE RINGS.
Albanian Journal of Mathematics,
Vol. 4,
Issue. 1,
Farashahi, Reza Rezaeian
and
Shparlinski, Igor E.
2012.
Pseudorandom Bits From Points on Elliptic Curves.
IEEE Transactions on Information Theory,
Vol. 58,
Issue. 2,
p.
1242.
Ostafe, Alina
and
Shparlinski, Igor E.
2012.
On the power generator and its multivariate analogue.
Journal of Complexity,
Vol. 28,
Issue. 2,
p.
238.
Ostafe, Alina
and
Shparlinski, Igor E.
2012.
EXPONENTIAL SUMS OVER POINTS OF ELLIPTIC CURVES WITH RECIPROCALS OF PRIMES.
Mathematika,
Vol. 58,
Issue. 1,
p.
21.
McLEMAN, CAM
and
MOODY, DUSTIN
2013.
CLASS NUMBERS VIA 3-ISOGENIES AND ELLIPTIC SURFACES.
International Journal of Number Theory,
Vol. 09,
Issue. 01,
p.
125.
Ahmadi, Omran
and
Shparlinski, Igor E.
2014.
Exponential sums over points of elliptic curves.
Journal of Number Theory,
Vol. 140,
Issue. ,
p.
299.
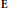 $\mathbf{E}$, we obtain an upper bound on the discrepancy of sets of multiples
$\mathbf{E}$, we obtain an upper bound on the discrepancy of sets of multiples 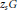 ${{z}_{s}}G$ where
${{z}_{s}}G$ where  ${{z}_{s}}$ runs through a sequence
${{z}_{s}}$ runs through a sequence 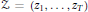 $Z\,=\,\left( {{z}_{1}},\ldots ,{{z}_{T}} \right)$ such that
$Z\,=\,\left( {{z}_{1}},\ldots ,{{z}_{T}} \right)$ such that 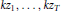 $k{{z}_{1}},\ldots ,k{{z}_{T}}$ is a permutation of
$k{{z}_{1}},\ldots ,k{{z}_{T}}$ is a permutation of 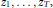 ${{z}_{1}},\ldots ,{{z}_{T}}$, both sequences taken modulo
${{z}_{1}},\ldots ,{{z}_{T}}$, both sequences taken modulo  $t$, for sufficiently many distinct values of
$t$, for sufficiently many distinct values of  $k$ modulo
$k$ modulo  $t$.
$t$.



