1. Introduction
Quantum key distribution (QKD) is a cryptographic protocol which allows two communicating parties, conventionally called Alice and Bob, to distribute a secret key in such a way that the presence of an eavesdropper, Eve could be revealed [1] . QKD makes use of quantum mechanical concepts such as the Heisenberg uncertainty principle and the no-cloning theorem in order to ensure that Eve cannot gain non-negligible amount of information without being detected, even if her computational power is unlimited [2] . Since the proposal of the BB84 protocol by Bennett and Brassard in 1984, both theorists and experimentalist have invented various protocols due to various security needs and applications. For example, in 1991, Ekert [3] extended the idea of the BB84 protocol by introducing quantum entanglement and the violation of Bell’s theorem [1] . Several variations of these protocols include: Bennett 1992 (B92) [4] , six states [5] , the Scarani Acn Ribordy Gisin 2004 (SARG04) [6] , the differential-phase shift (DPS) [7] , the coherent-one-way (COW) [8] and the Phoenix Barnett and Chefles 2000 (PBC00) protocol [9] . The PBC00 protocol is based on the B92 protocol, with the main difference between the two beings that the latter uses two states whilst the former uses three states. Consequently, the PBC00 protocol is more symmetrical (in the sense that either Alice or Bob, but not both, can declare unused observables) and shows lower qubit losses than the B92 protocol. Our proposed scheme improves the PBC00 protocol by making use of additional detection set which has three non-orthogonal states. Moreover, the additional detection states allow increased possibility for eavesdropper detection. As a result, this greatly improves the security of our protocol.
2. Operation of Our Protocol
In our scheme, Alice uses one of the three mutually non-orthogonal states in one set to encode her bit of infor- mation, and on the receiving side, Bob uses one of the three mutually non-orthogonal states of the other set to make measurements. The protocol is realized through the following steps, as shown in Table 1:
1) Alice randomly and with equal probability prepares and sends quantum signals using any of the two detec- tion sets. Detection set0 is made up of the following mutually non-orthogonal states: ,
,
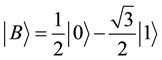 and
and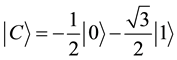 , while detection set1 is made up of these states:
, while detection set1 is made up of these states: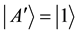 ,
,
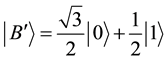 and.
and.
2) Bob performs a positive operator valued measurement (POVM) on each received signal, using any of the two detector sets. He then announces to Alice which detection set he used. They discard signals corresponding to time slots where they used similar detection sets for both preparation and measurement, and keep the rest. This is shown as the first result in the table.
3) On the remaining measured signals, Bob announces the time slots where he received no detections at all. Again, they discard the signals corresponding to these time slots and keep the rest.
4) Alice then announces one of the states she did not send. After this, Bob would then know what state Alice sent, and the signals corresponding to such time slots would be used to construct the secret key.
![]()
Table 1. An illustration of exchange of qubits between Alice and Bob showing some various possibilities and the result of the inferred bits.
Consider the states of detection set0 to be ,
, 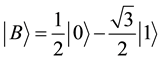 and
and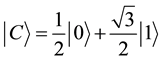 , while
, while
detection set1, which has a set of states orthogonal to those in detection set0, has the states: ,
,
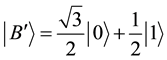 and.
and.
In order to assign bit values shown in Table 1, the following procedure is followed. The signals that have not been eliminated are used for this protocol, and this is shown by the first result in the table. From this, Alice and Bob will know which state was sent and which state she announces that she did not send. Detection set0 is assigned the basis “0” and detection set1 is assigned basis state “1”. The major additional feature, which happens in our protocol, occurs when Alice sends signals in a particular detection set and Bob uses the same detection set to make measurements. During this time slot, they discard their results. This happens in time slots 3, 6 and 8. In time slot 1, Alice prepares the state 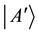 which in fact corresponds to basis in the detection set1, Bob uses detection set0 to make the measurements, since they use different detection sets, they use signals from this time slot and they record “1” (yes). Bob then performs some measurements on the signals, which he received. Since Alice has announced the result as not a
which in fact corresponds to basis in the detection set1, Bob uses detection set0 to make the measurements, since they use different detection sets, they use signals from this time slot and they record “1” (yes). Bob then performs some measurements on the signals, which he received. Since Alice has announced the result as not a 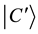 (this is two hops clockwise from
(this is two hops clockwise from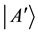 ), so they record a “1”. The sequence becomes
), so they record a “1”. The sequence becomes 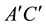 and then the inferred bit is “1”. If the state that Alice announces is one hop away in a clockwise direction they record a “0” as in time slot 3. Moreover, the bit inferred will also be “0”.
and then the inferred bit is “1”. If the state that Alice announces is one hop away in a clockwise direction they record a “0” as in time slot 3. Moreover, the bit inferred will also be “0”.
3. Optimum Measurements
In this section we begin by describing some of the most important aspects of information, i.e., measurement of information. Information can be measured according to its degree of uncertainty, i.e., if an event is likely then one gains little information in learning that it finally occurred and the converse is true. This brings us to the concept of entropy [10] , specifically the Shannon entropy. The Shannon entropy is used to quantify the expected value of information contained in a message. It is defined as
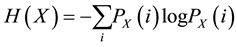 (1)
(1)
where ![]() is a discrete random variable. One can also describe the Shannon mutual information of two events
is a discrete random variable. One can also describe the Shannon mutual information of two events ![]() and
and![]() . The Shannon mutual information gives the amount of information that one can obtain from the bitstring shared between Alice
. The Shannon mutual information gives the amount of information that one can obtain from the bitstring shared between Alice ![]() and Bob
and Bob![]() . It is defined in terms of conditional probability
. It is defined in terms of conditional probability ![]() as:
as:
![]() (2)
(2)
where ![]() is the joint probability, and
is the joint probability, and ![]() and
and ![]() are the marginal probabilities of the input and output letters
are the marginal probabilities of the input and output letters ![]() and
and![]() , respectively. In the context of QKD, this can be interpreted as the amount of information that one (Eve) additionally obtains when considering both Alice and Bob’s source, and not only Alice’s source X. The eavesdropper can use any strategy in order to obtain any information shared between Alice and Bob. For example, Eve can obtain as much information as possible from the long strings by maxi- mizing the Shannon mutual information. On the other hand, if Eve wants to obtain as much information as possible from single measurements then she has to maximize the discrimination probability. The probability of correctly discriminating between states is given as
, respectively. In the context of QKD, this can be interpreted as the amount of information that one (Eve) additionally obtains when considering both Alice and Bob’s source, and not only Alice’s source X. The eavesdropper can use any strategy in order to obtain any information shared between Alice and Bob. For example, Eve can obtain as much information as possible from the long strings by maxi- mizing the Shannon mutual information. On the other hand, if Eve wants to obtain as much information as possible from single measurements then she has to maximize the discrimination probability. The probability of correctly discriminating between states is given as
![]() (3)
(3)
where ![]() is the apriori probability of the state
is the apriori probability of the state ![]() and
and ![]() refers to the probability that the state
refers to the probability that the state ![]() is sent and that the measurement performed by Eve shows the outcome
is sent and that the measurement performed by Eve shows the outcome![]() . In the case of six apriori equal likely symmetric states, the discrimination probability is expressed as
. In the case of six apriori equal likely symmetric states, the discrimination probability is expressed as
![]() . (4)
. (4)
By introducing an extra detection set, we obtain a discrimination probability which is higher than that of the original scheme (where![]() ). This means that the proposed protocol makes it difficult for Eve to dis- criminate between the states sent by Alice to Bob. The probability that the state is incorrectly detected as one of the other five states is 1/30. The optimum measurement has six elements, which are defined as
). This means that the proposed protocol makes it difficult for Eve to dis- criminate between the states sent by Alice to Bob. The probability that the state is incorrectly detected as one of the other five states is 1/30. The optimum measurement has six elements, which are defined as
![]() (5)
(5)
Since these elements are positive semi-definite and form an identity, they are positive operator-valued mea- sures (POVMs). The maximum value of the mutual information can be achieved by a POVM with six elements described by
![]() (6)
(6)
which implies that the system is not in one of the signal states. The signal states are the ones that carry the necessary information from which the secret key would be extracted.
4. Eavesdropper Detection
Alice and Bob can detect the presence of an eavesdropper during the classical communication. This is achieved when they realize that the bits sent by Alice and measured by Bob are different. Let’s consider the case where Alice sends the state![]() . When Eve performs optimal state discrimination measurement, she will obtain the measurement results
. When Eve performs optimal state discrimination measurement, she will obtain the measurement results ![]() with probabilities 5/6, 1/30, 1/30, 1/30, 1/30 and 1/30, respectively.
with probabilities 5/6, 1/30, 1/30, 1/30, 1/30 and 1/30, respectively.
If Alice sends the signal state![]() , the average state which Bob receives is then defined as
, the average state which Bob receives is then defined as
![]() (7)
(7)
We have simplified the above equation by applying the fact that
![]() (8)
(8)
By performing optimal mutual information measurement, it follows that Eve will obtain the results of
![]() ,
, ![]() ,
, ![]() ,
, ![]() ,
, ![]() , each with probability 1/5. Then a density matrix
, each with probability 1/5. Then a density matrix
that describes the average state received by Bob is written as
![]() (9)
(9)
that is the state with a similar form as that obtained for the maximum state-discrimination measurement.
For detection set0, the protocol will give a correct key bit if Bob measures![]() , and
, and ![]() and gets the result 1 and if Alice reveals that she didn’t send
and gets the result 1 and if Alice reveals that she didn’t send ![]() or
or ![]() respectively. Conversely, for detection set1, the protocol will give a correct key bit if Bob measures
respectively. Conversely, for detection set1, the protocol will give a correct key bit if Bob measures![]() , and
, and ![]() and gets the result 1 and if Alice reveals that she didn’t send
and gets the result 1 and if Alice reveals that she didn’t send ![]() or
or ![]() respectively. The probability for this to happen is
respectively. The probability for this to happen is
![]() (10)
(10)
where 1/6 is the probability for Bob to have chosen the given measurement and 1/5 is the probability that arises from Alice’s random choice of announcing which state she did not send. This probability is less than the one proposed in [9] . However, our scheme makes it easier for the presence of Eve to be detected. In detection set0, if Alice prepares state![]() , the probability that Eve’s activity will produce an incorrect key bit is simply the pro- bability that Bob chooses to measure
, the probability that Eve’s activity will produce an incorrect key bit is simply the pro- bability that Bob chooses to measure ![]() and obtains a non-zero number. The opposite also holds for detection set1.
and obtains a non-zero number. The opposite also holds for detection set1.
![]() (11)
(11)
As compared to the previous scheme, we realize that in our protocol, there is a higher chance that Eve will be detected. If Eve performs an intercept and resend attack, she will introduce errors in Alice’s and Bob’s shared key with the probability![]() .
.
Ultimately the average state received by Bob will be
![]() (12)
(12)
For Bob, the probabilities of correct detection ![]() and incorrect detection
and incorrect detection ![]() are given by
are given by
![]() (13)
(13)
and![]() , respectively. This shows another improvement of our scheme since the pro-
, respectively. This shows another improvement of our scheme since the pro-
bability that Bob will generate an incorrect key bit is lower than in the original scheme. This means that most of the time Bob will be able to correctly generate the correct bit.
5. Optical Implementation
We provide an optical implementation of this scheme in Figure 1. Different trine and anti-trine measurement values for the proposed protocol are depicted in Table 2. In each arm three polarising beamsplitters and two half-wave plates are used. On the right had side, the polarising beamsplitters transmit horizontally polarised light and reflect the vertically polarised light. In the left arm, the opposite happens, the vertically polarised light is transmitted and the horizontally polarised one is reflected. In Table 2, we show the signal states at different locations. For each set, the input state after the non-polarising beamsplitter at position 2 goes through the polarising beamsplitter. On the right arm, between positions 3 and 4, we have a half-wave plate, which is given by the following unitary operator:
![]() . (14)
. (14)
In a like manner, on the left arm, between positions 3 and 4, we have a half-wave plate, which is given by the following unitary operator:
![]() . (15)
. (15)
In both arms, these unitary operators are responsible for producing the states at position 4. On the right arm, the vertically polarised light at position 7, will be detected by D4, while on the left arm at the same position, the horizontally polarised light will be detected by D1. Between positions 8 and 9 of the right arm, the following unitary operator describes the half-wave plate:
![]()
Figure 1. An optical implementation of the proposed six-state QKD protocol. The part S is the signal from Alice, and this signal goes a non-polarising beamsplitter and either goes to the left arm or right arm. We assume the interferometers used in each arm are balanced. The left arm represents the set0 measurements and the right arm represents the set1 measurements. From position 2, the polarising beamsplitters are used together with half-wave plates. The signals states for the positions marked are shown in Table 2 and the single photon detectors are marked D1 - D6.
![]()
Table 2. States at each location, as depicted in Figure 1.
![]() , (16)
, (16)
while on the left arm the unitary operator is given as
![]() . (17)
. (17)
On the right arm, the vertically polarised light at position 10, will be detected by D5, while on the left arm at the same position, the horizontally polarised light will be detected by D2. The horizontally polarised light at position 11 for the right arm will be detected by D6 while the vertically polarised light on the left arm at position 11 will be detected by D3.
It is worth noting that in order to switch from set0 to set1, the following unitary is used:
![]() , (18)
, (18)
Conversely, the unitary used for switching from set1 to set0 is given as:
![]() . (19)
. (19)
Apart from our proposed protocol being more secure, the additional symmetry that exists in our protocol also allows the various security proofs methods to be applied for instance the post-selection technique which was proposed by Renner and Christandl [11] and has recently been applied in [12] .
6. Conclusion
In this work, we have demonstrated an optical implementation of a six-state symmetric QKD protocol. Since our protocol uses additional detection set, this improves its symmetry, increases the discrimination probability and thereby improves the detection of Eve. In our proposed scheme, we have also demonstrated that the Bob’s pro- bability of generating error-free bitstring is lower than that of the original scheme. This shows that our proposed six-state symmetric QKD protocol is more secure.
Acknowledgements
This work is based on research supported by the South African Research Chair Initiative of the Department of Science and Technology and National Research Foundation.